Control method, controller and monitoring device
A technology of monitoring equipment and control method, applied in the field of electronics, can solve problems such as large investment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
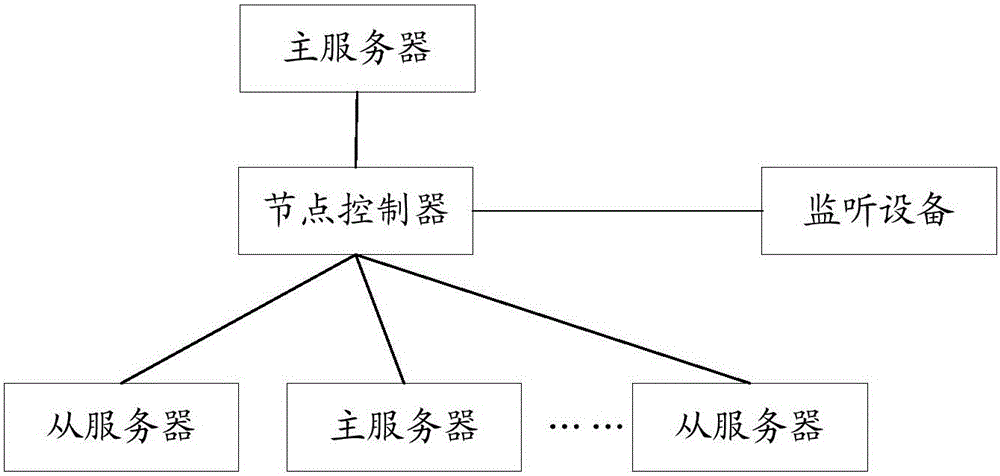
[0069] This embodiment provides a control method, specifically, this embodiment provides a disaster recovery method, that is, control a master server and multiple slave servers through a node pool (that is, the node controller described in this embodiment) communication connection between servers to achieve mutual backup and disaster recovery between servers; when a disaster occurs, slave servers in a normal communication state can be selected through the node pool, thereby maximizing the continuity of services and the resource availability of the database system and, the disaster recovery method described in the present embodiment can realize high-efficiency fault detection without making large changes to the existing database system. The method described in the example is inexpensive.
[0070] Here, the method described in this embodiment can be specifically applied to a database system; the database system specifically includes: a node controller, a listening device, a mast...
Embodiment 2
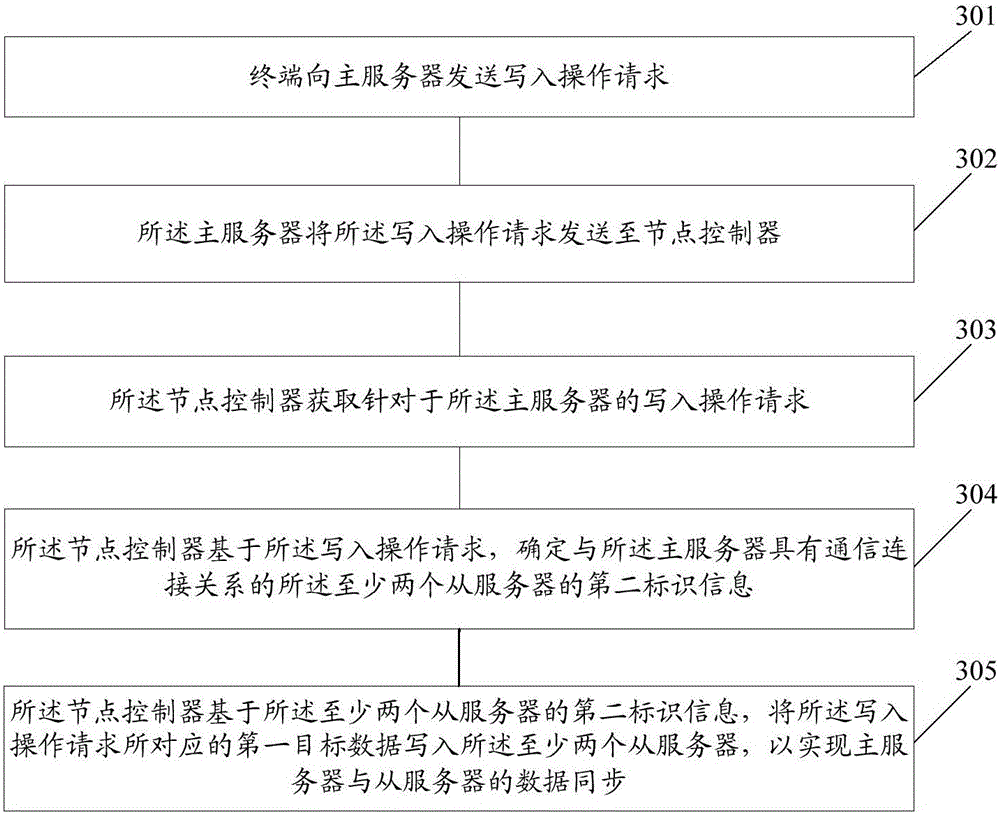
[0080] Based on the method described in Embodiment 1, this embodiment provides an implementation of the write operation; specifically, as image 3 As shown, the method includes:
[0081] Step 301: the terminal sends a write operation request to the main server;
[0082] Wherein, the write operation request represents an operation request sent by the terminal to the main server to request to write the first target data;
[0083] Step 302: the main server sends the write operation request to the node controller;
[0084] Step 303: the node controller acquires a write operation request for the main server;
[0085] Step 304: The node controller determines second identification information of the at least two slave servers that have a communication connection relationship with the master server based on the write operation request;
[0086] In an embodiment, based on the write operation request, the node controller determines the second identification information of all slave s...
Embodiment 3
[0091] Based on the method described in Embodiment 1 or Embodiment 2, this embodiment provides an implementation of the read operation; specifically, as Figure 4 as shown,
[0092] Step 401: the terminal sends a read operation request to the address selection controller;
[0093] Wherein, the read operation request represents that the terminal requests to read the second target data from the server to the third target;
[0094] Step 402: the address selection controller receives the read operation request;
[0095] Step 403: The address selection controller receives the second identification information for the second target slave server sent by the listening device;
[0096] Wherein, the second target slave server is a target slave server selected by the monitoring device from at least two slave servers in the second communication state with the master server;
[0097] Specifically, when the monitoring device monitors the communication state between the master server and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com