A Feedback-Based Randomized Multi-User Access Method
A multi-user access and user technology, applied in wireless communication, electrical components, etc., can solve the problems of insufficient throughput and insufficient utilization of received data packets, and achieves improved throughput, system throughput, and access to users. Number boosting effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
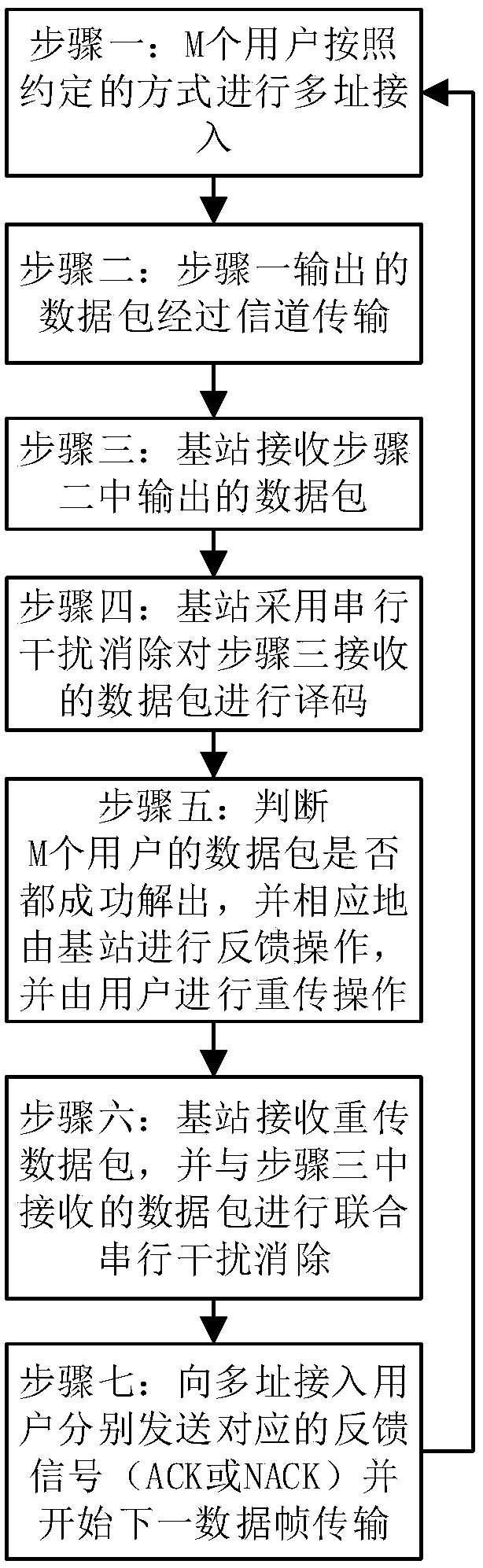
[0071] The following describes how to apply an improved CSA access method based on feedback retransmission in the present invention to improve the throughput of the system in conjunction with the specific access process.
[0072] figure 1 It is a feedback-based random multi-user access method of the present invention and an overall flow chart of this embodiment; figure 1 It can be seen that the specific implementation steps in this embodiment are as follows:
[0073] Step 1: M users perform multiple access according to the agreed method;
[0074] Step 2: The data packet output in step 1 is transmitted through the channel;
[0075] Step 3: the base station receives the data packet output in step 2;
[0076] Step 4: The base station uses serial interference cancellation to decode the data received in Step 3;
[0077] Step 5: Determine whether the data packets of M users are successfully decoded, and the base station performs a feedback operation accordingly, and the user per...
Embodiment 2
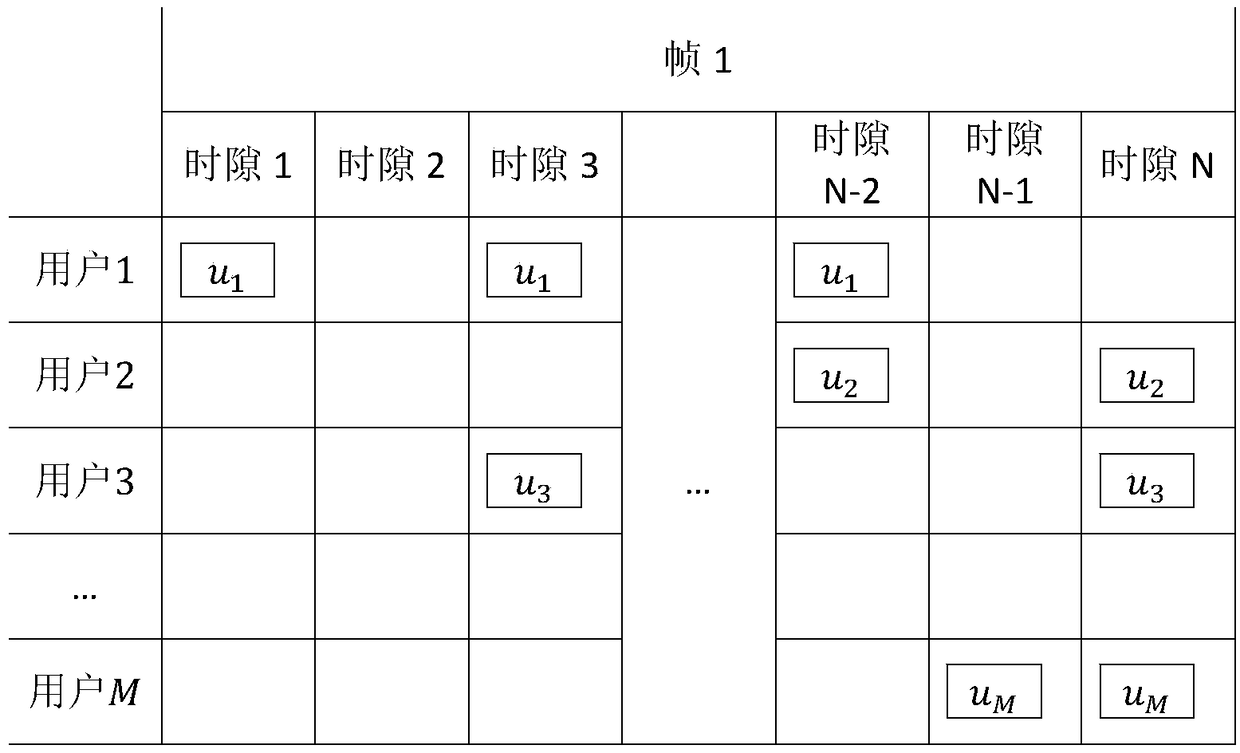
[0082] figure 2 Indicates the access process of the traditional CSA access mode, figure 2 shows a frame 1 containing N time slots, which is multiple-accessed by M users. Taking user 1 as an example, the degree of user 1 selection is 3, and randomly selects time slot 1, time slot 3 and slot N-2 for transmission.
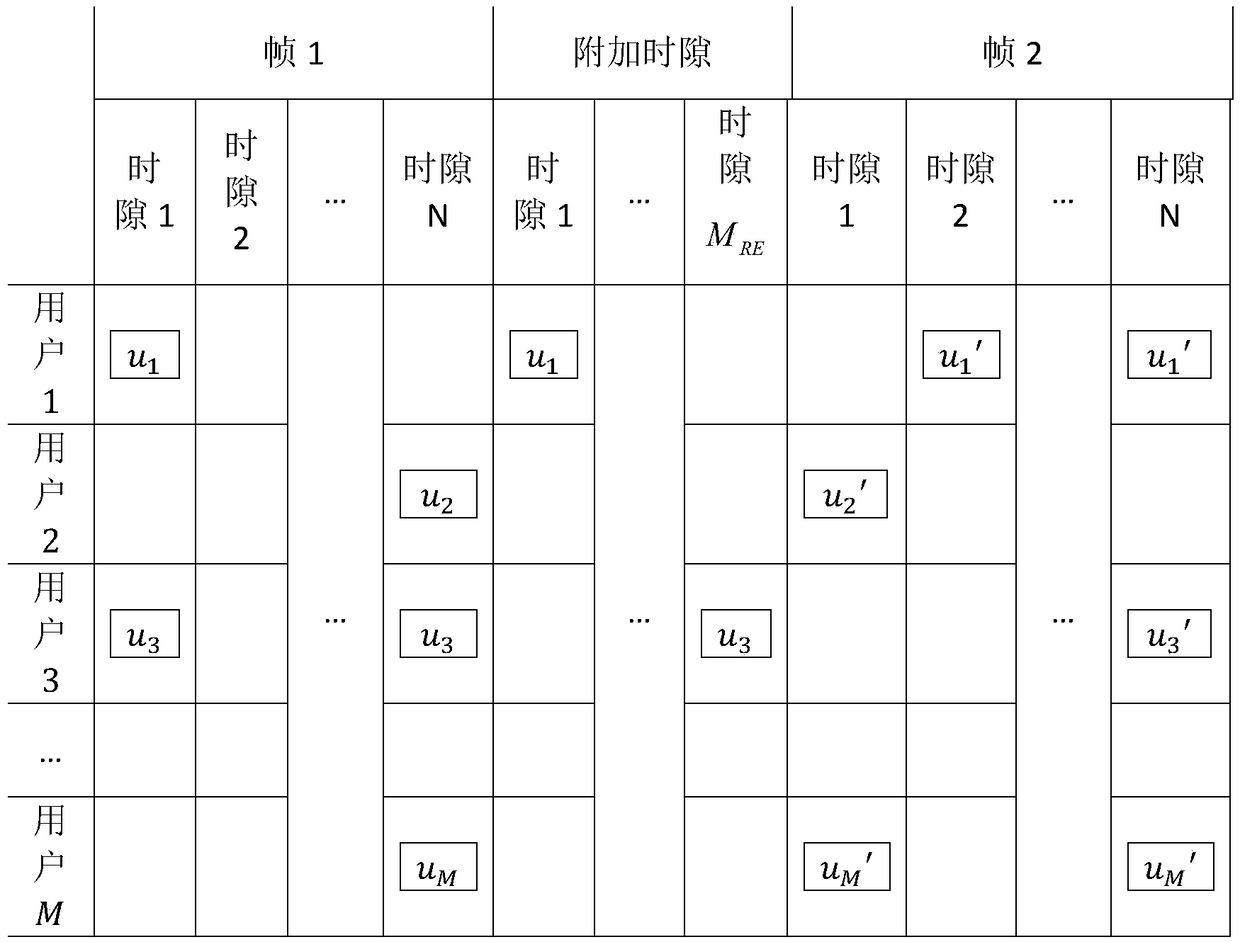
[0083] image 3 It is a possible access in this embodiment of a random multi-user access method based on feedback in the present invention, where frame 1 and frame 2 are according to figure 2 The access is performed by M users respectively in the additional time slots 1 to M RE Among them, there are M RE Each user retransmits the data packets in order, and the additional time slot transmission criterion is determined by step 5 in the description, for example, user 1 retransmits in time slot 1 in this embodiment.
Embodiment 3
[0085] Figure 4 It is a possible access in this embodiment based on a feedback-based random multi-user access method of the present invention.
[0086] This embodiment adopts CSA access based on feedback retransmission, including the following steps:
[0087] Step A, using the MAC frame model; the present embodiment is specific to Figure 4 The possible access situation reflected in , the current MAC frame contains an average of 5 time slots, and assuming that the user and the base station are fully synchronized, there are 5 users, respectively: u 1 ,u 2 ,u 3 ,u 4 ,u 5 ; Access and send data packets in this MAC frame, define the normalized load of the system as The normalized throughput T is defined as the average number of data packets sent on each frame, and the degree distribution of this embodiment is:
[0088] Λ(x)=Λ 1 x+Λ 2 x 2 +…+Λ 5 x 5 (4)
[0089] Among them, Λ l Represents the probability that the user chooses to resend the data packet for l times. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com