Software security detection method based on combination of vulnerability model and symbolic execution
A symbolic execution and software security technology, which is applied in the field of computer software security testing, can solve problems such as insufficient vulnerability mining, achieve efficient software security vulnerability detection, high efficiency, and improve software security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
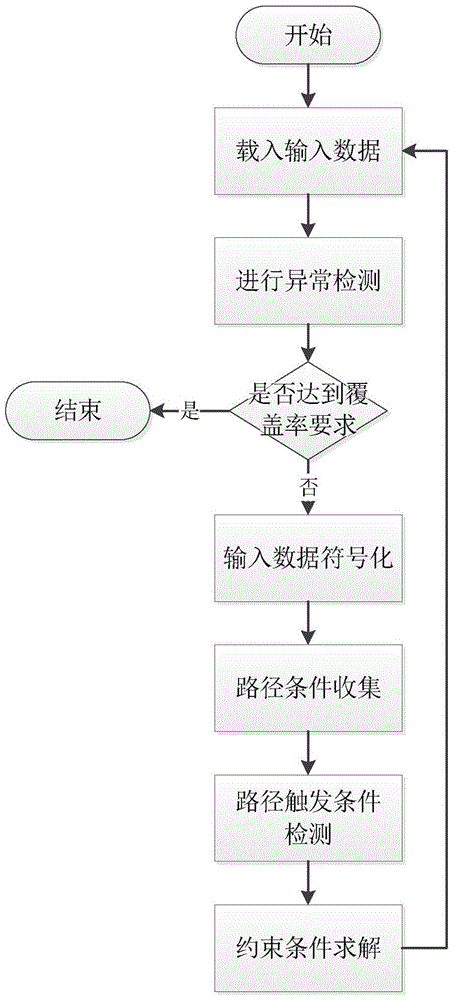
[0022] Embodiment one, see figure 1 As shown, a software security detection method based on the combination of vulnerability model and symbolic execution includes the following steps:
[0023] Step 1. Load the input data into the program under test, and the input data drives the execution of the program under test to detect abnormalities;
[0024] Step 2. Determine whether the program path coverage requirement is met, and if so, end the test, otherwise, enter step 3;
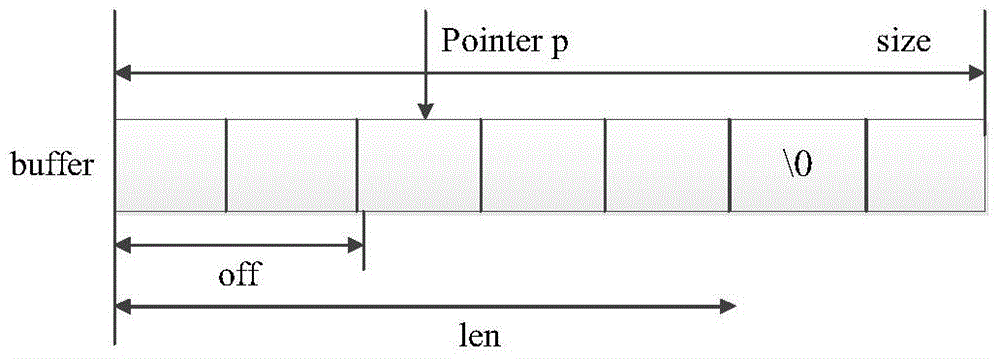
[0025] Step 3. Symbolize the input data, determine the input point and the size of the input data, mark the symbolic variables in the symbolic execution, and define these symbolic variables as a set of original symbolic variables, the symbolic variables include the original symbolic variables and intermediate symbolic variables, intermediate symbols The variable is the symbolic variable represented by the original symbolic variable expression. When the program starts symbolic execution and actual execution, the...
Embodiment 2
[0028] Embodiment two, see Figure 1~3 As shown, a software security detection method based on the combination of vulnerability model and symbolic execution includes the following steps:
[0029] Step 1. Load the input data into the program under test, and the input data drives the execution of the program under test to detect abnormalities;
[0030] Step 2. Determine whether the program path coverage requirement is met, and if so, end the test, otherwise, enter step 3;
[0031] Step 3. Symbolize the input data, determine the input point and the size of the input data, mark the symbolic variables in the symbolic execution, and define these symbolic variables as a set of original symbolic variables, the symbolic variables include the original symbolic variables and intermediate symbolic variables, intermediate symbols The variable is the symbolic variable represented by the original symbolic variable expression. When the program starts symbolic execution and actual execution, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com