A user authentication method and device
A user authentication and user technology, applied in the direction of digital data authentication, etc., can solve problems such as loss and personal information leakage, and achieve the effect of not easy to counterfeit and good security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
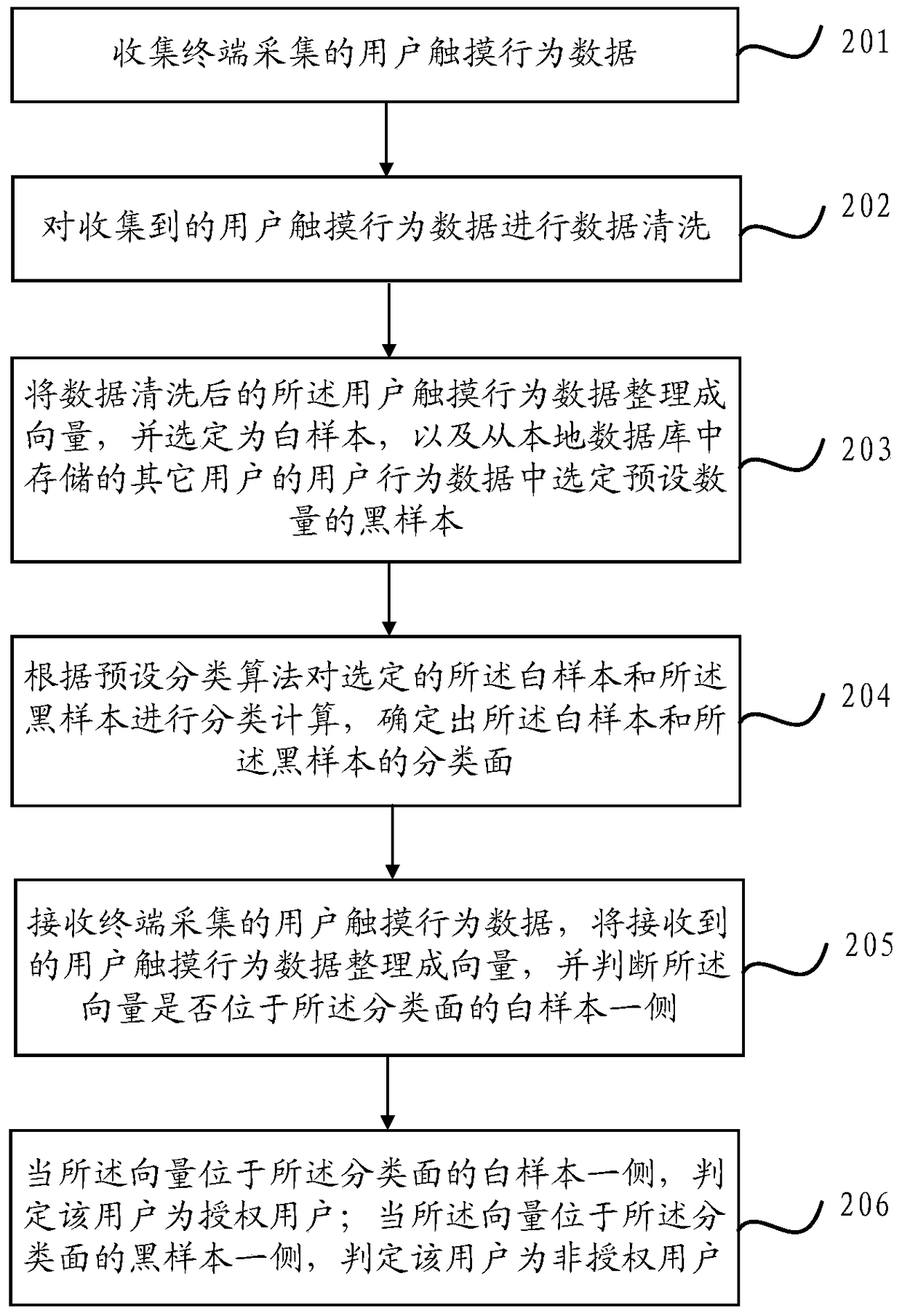
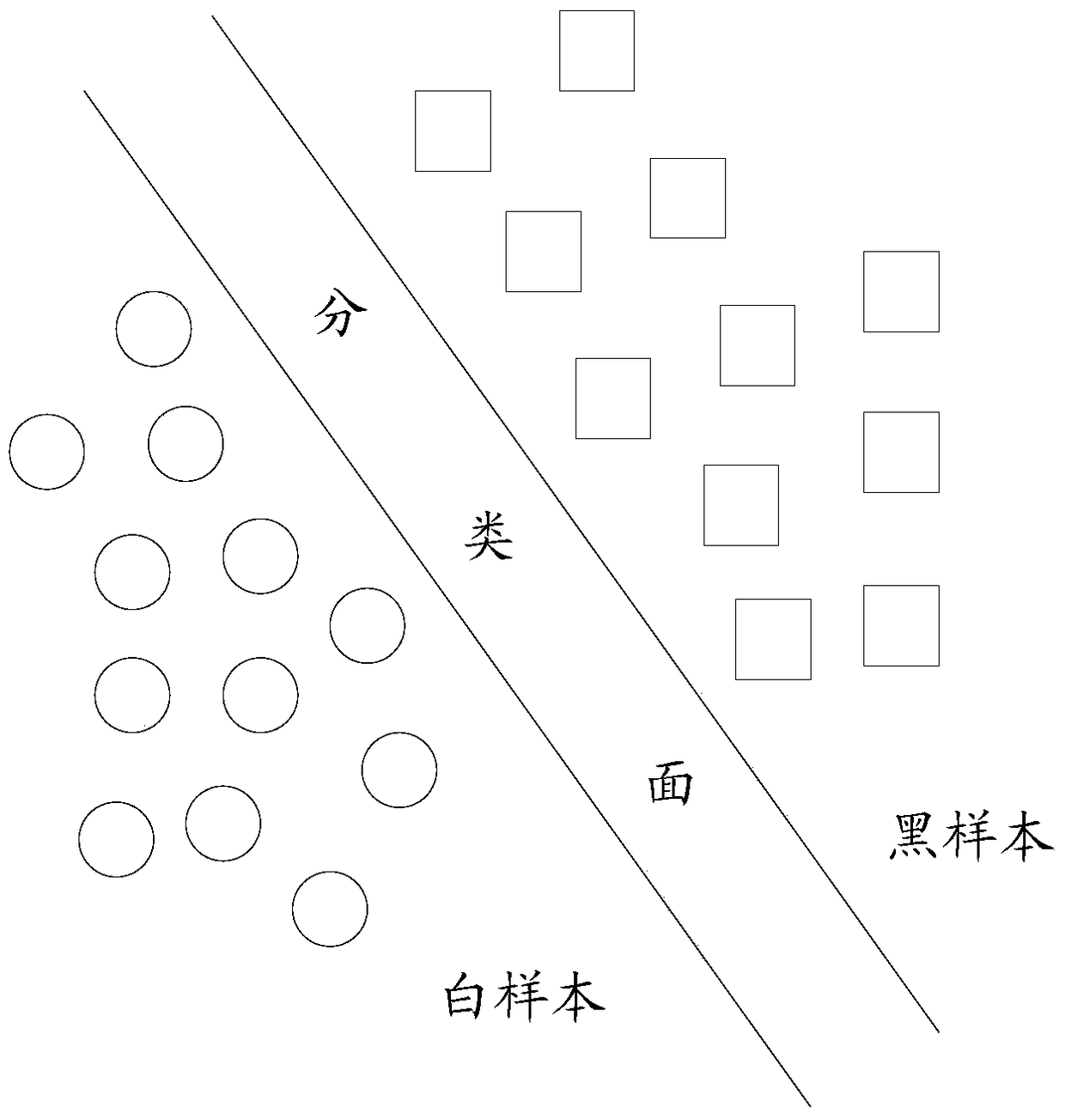
[0060] This application proposes a user authentication method, which determines whether the user is an authorized user by matching the user's touch behavior data collected by the terminal with the customary touch behavior of the authorized user of the terminal; it is similar to the user authentication method in the existing implementation Compared with this application, since the identity authentication is performed based on the user's touch behavior data collected by the terminal, it is not easy to counterfeit, and the security is better; and this application can complete the identity authentication of the user without the user's knowledge, which has a certain degree of privacy, so When the terminal is lost, it will not cause leakage of personal information.
[0061] The present application is described below through specific embodiments and in combination with different application examples.
[0062] Please refer to figure 1 ,figure 1 It is a user authentication method prov...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com