A threat detection method and security device based on fusion verification of key parameters
A threat detection and key parameter technology, applied in electrical testing/monitoring, testing/monitoring control systems, instruments, etc., can solve problems such as not making full use of security detection and protection, ignoring data consistency verification, etc., to achieve a rich level Security, good threat detection, and the effect of meeting individual needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
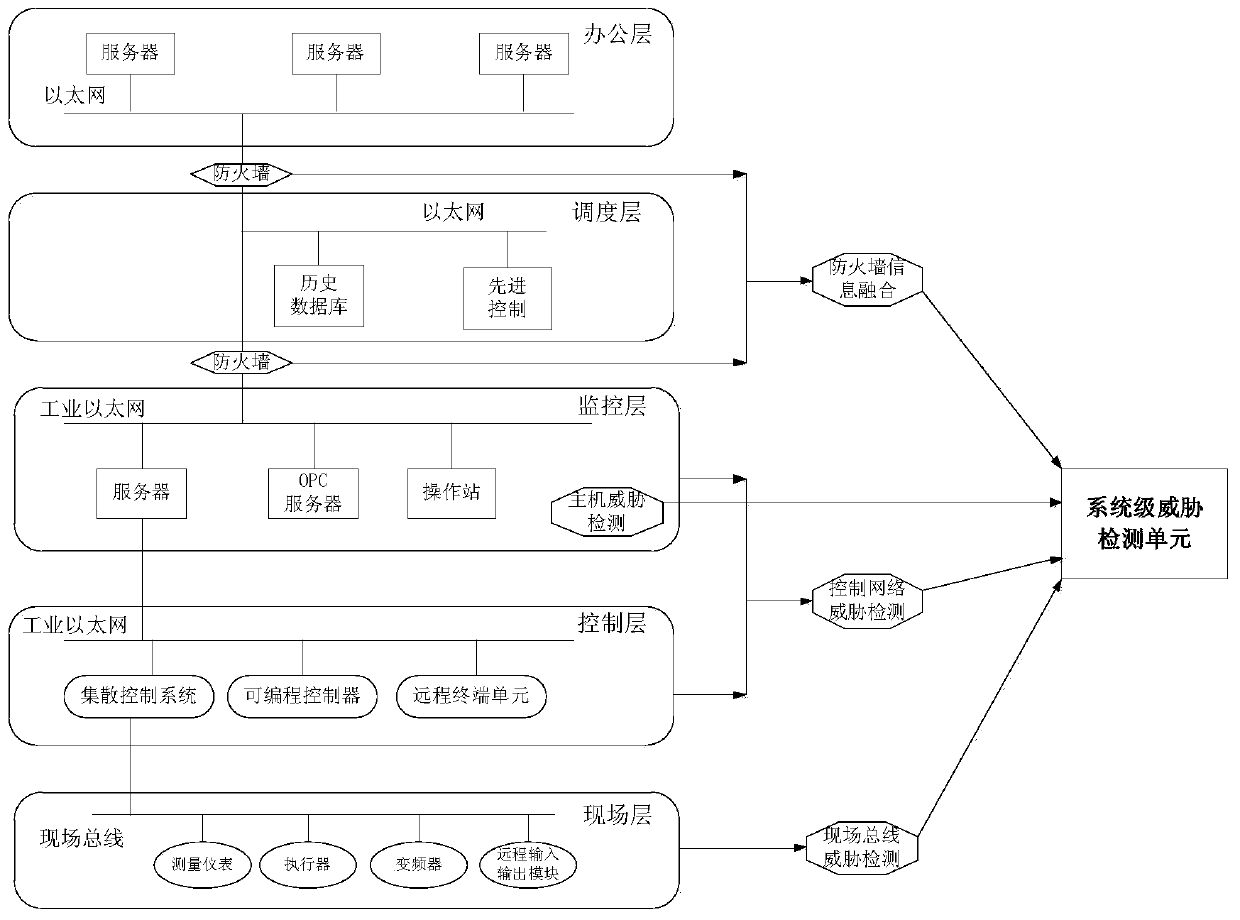
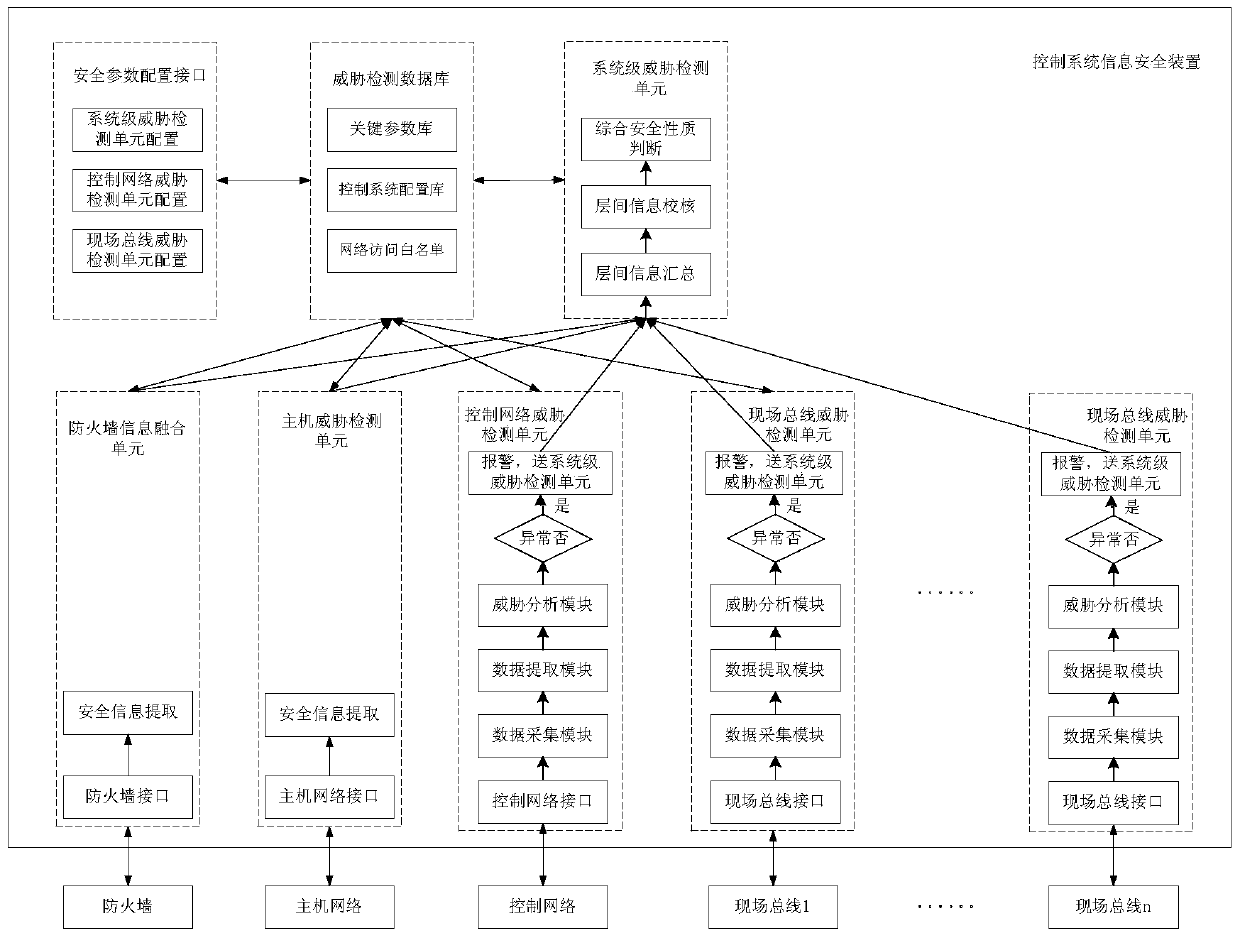
[0042] figure 1 It is a structural schematic diagram of the threat detection of the industrial control system in Embodiment 1. The system mainly conducts threat detection for typical industrial control systems including fieldbus layer, control layer, monitoring layer, scheduling layer and office layer.
[0043] The detected equipment at the field level mainly includes measuring instruments, actuators, frequency converters and remote input and output units.
[0044] The main equipment detected by the control layer includes the controller of the distributed control system, the programmable controller, the remote terminal unit and other equipment.
[0045] The main equipment detected by the host threat detection unit includes the server of the control system, the OPC server and the workstation (operator station, engineer station, etc.).
[0046] The firewall installed between the control layer and the scheduling layer detects the information exchange between the two layers, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com