Login method, terminal device and communication system
A login method and terminal equipment technology, applied in the communication field, can solve problems such as many input operations, poor user interaction experience, and cumbersome procedures
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0074] see figure 1 , is a schematic flowchart of an embodiment of the login method provided by the present invention. This login method is applicable to a terminal device configured with a software client and a system client, which mainly includes steps 101 to 107, specifically as follows:
[0075] Step 101: The software client establishes a local connection channel with the system client, and receives the account information provided by the system client through the local connection channel; wherein, the software client and the system client are configured in the same terminal device, and the system client The account information has been used to log in to the system server successfully, and the login credentials corresponding to the account information are stored in the system server.
[0076] In this embodiment, all clients share the same account system, and each account is managed by the account server. The account server can verify whether the account information of ea...
Embodiment 2
[0112] see Figure 4 , Figure 4 is a schematic structural diagram of an embodiment of a terminal device provided by the present invention, such as Figure 4As shown, the terminal device is configured with a software client 1 and a system client 2. The software client 1 includes: a local connection building unit 11 , a persistent connection building unit 12 , a first receiving unit 13 , a first sending unit 14 , a second receiving unit 15 , and a first login unit 16 . The system client 2 includes: a second sending unit 21 .
[0113] The local connection construction unit 11 is used to establish a local connection channel with the system client 2, and receive the account information provided by the system client 2 through the local connection channel; wherein, the system client 2 has successfully logged into the system server using the account information, The login credential corresponding to the account information is stored in the system server.
[0114] The persistent c...
Embodiment 3
[0127] see Figure 7 , Figure 7 It is a structural schematic diagram of an embodiment of the communication system provided by the present invention. Such as Figure 7 As shown, the communication system includes: an account server 701 , a system server 702 , a software server 703 and a terminal device 704 . Wherein, the detailed structure and working principle of the terminal device 704 can be referred to, but not limited to, related records in Embodiment 1 and Embodiment 2.
[0128] Combine below Figure 8 to Figure 10 , to describe in detail the flow of information exchange provided by the communication system in this embodiment. The flow of information interaction in this communication system mainly includes steps S1 to S6, specifically as follows:
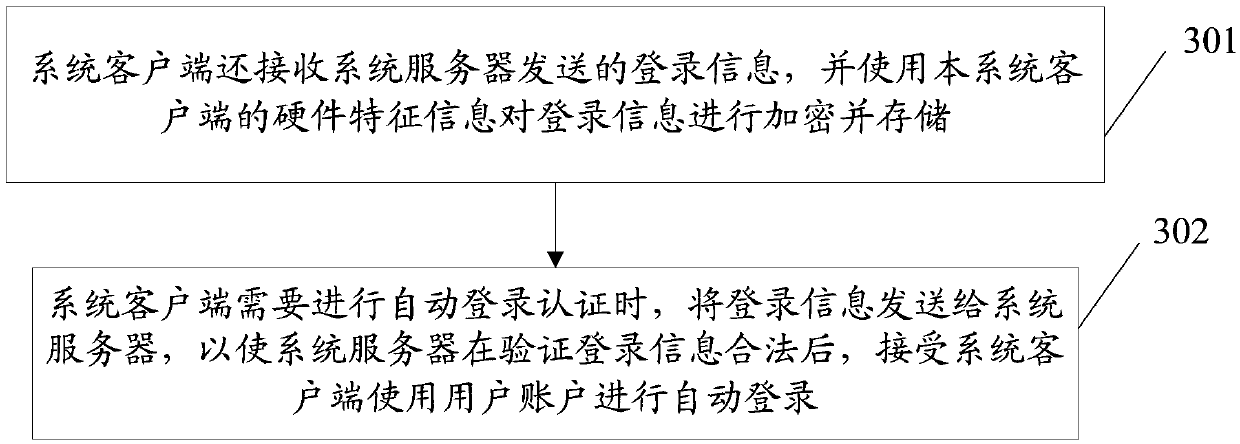
[0129] S1, the system client successfully logs in to the system server using the account information, and the system server stores the login credentials.
[0130] S2, the software client and the system client perform hand...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com