Data processing method and device
A data processing and indexing technology, applied in the field of network security, which can solve the problems of insufficient consideration of security situation statistics and inaccurate network security situation assessment results, and achieve accurate asset security situation assessment results, improve reliability, and statistics. Comprehensive effect of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
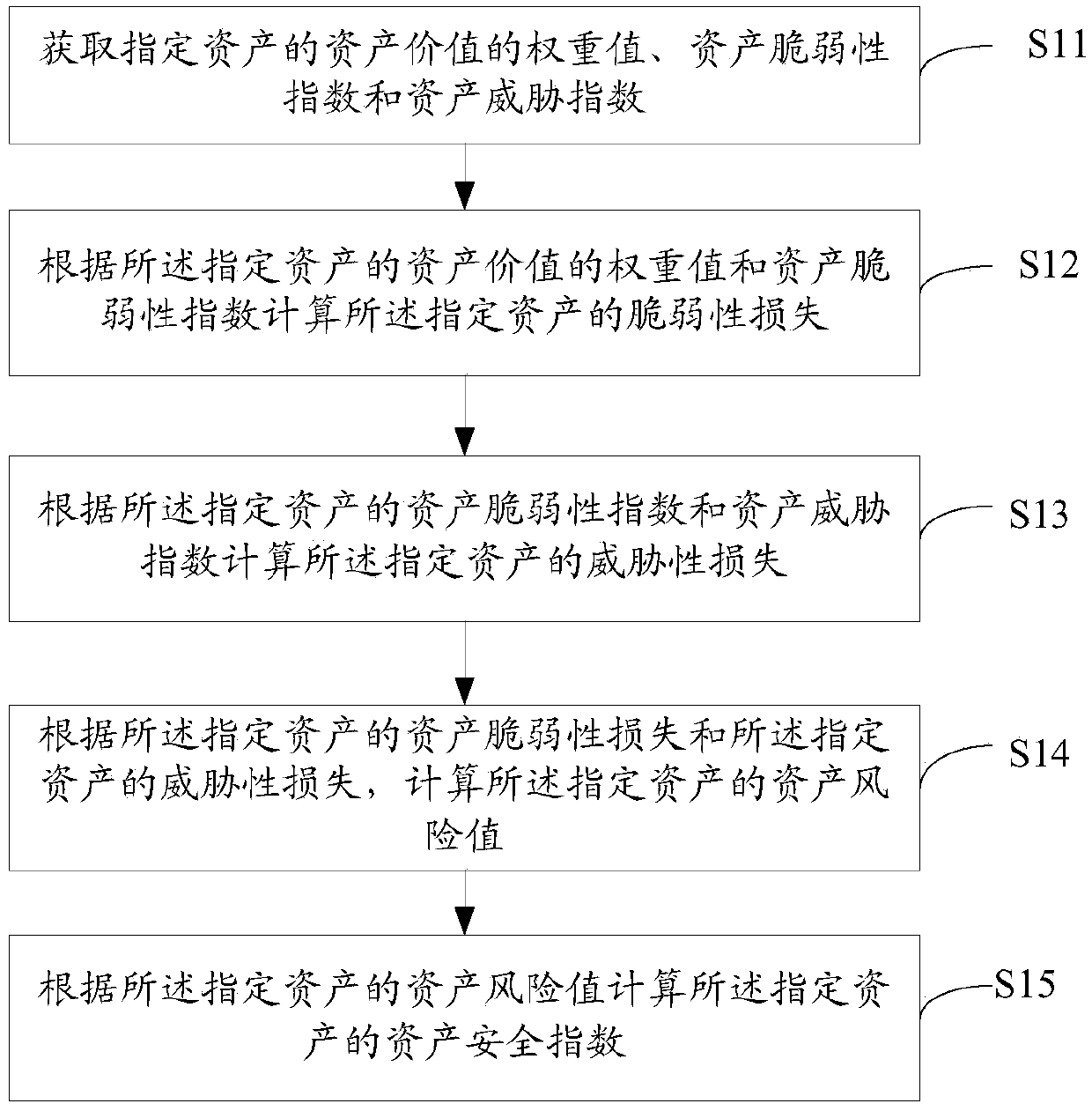
[0055] figure 1It is a schematic flowchart of a data processing method in the process of assessing the security situation at the asset level provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the method includes the following steps:
[0056] S11. Obtain the weight value of the asset value of the specified asset, the asset vulnerability index and the asset threat index;
[0057] The asset value is an inherent attribute of the asset, and the asset value is specified when the asset is added. Asset value is the characteristic value of asset importance. In the embodiment of the present invention, after a specified asset is determined, the asset value of the specified asset can be obtained, so as to further obtain the weight value of the asset value.
[0058] In the embodiment of the present invention, the asset value can be divided into core asset A, key asset B, important asset C, general asset D and simple asset E, and their corresponding weight val...
Embodiment 2
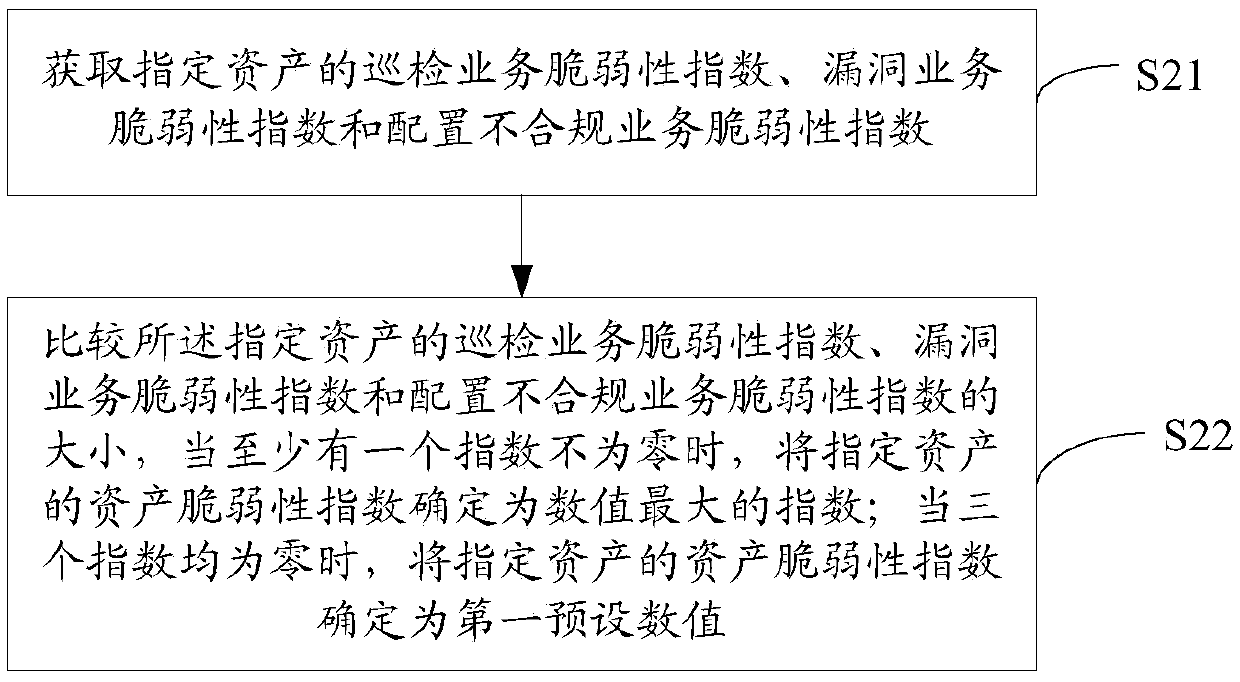
[0146] It should be noted that the business system is determined by the business content carried by the asset and is divided by the customer, such as OA system, mail system, etc. The assessment of the network security situation at the business system level needs to consider the security status of the assets under the business system. For an asset, the business system is also one of its attributes, which is used to indicate the business content carried by the asset. Each asset belongs to a business system, and each business system can have multiple assets. There is a one-to-many relationship between business systems and assets.
[0147] The data processing method of the network security situation assessment process at the business system level includes: calculating the business system security index, business system threat index and business system vulnerability index of a business system;
[0148] Among them, the process of calculating the business system security index of a...
Embodiment 3
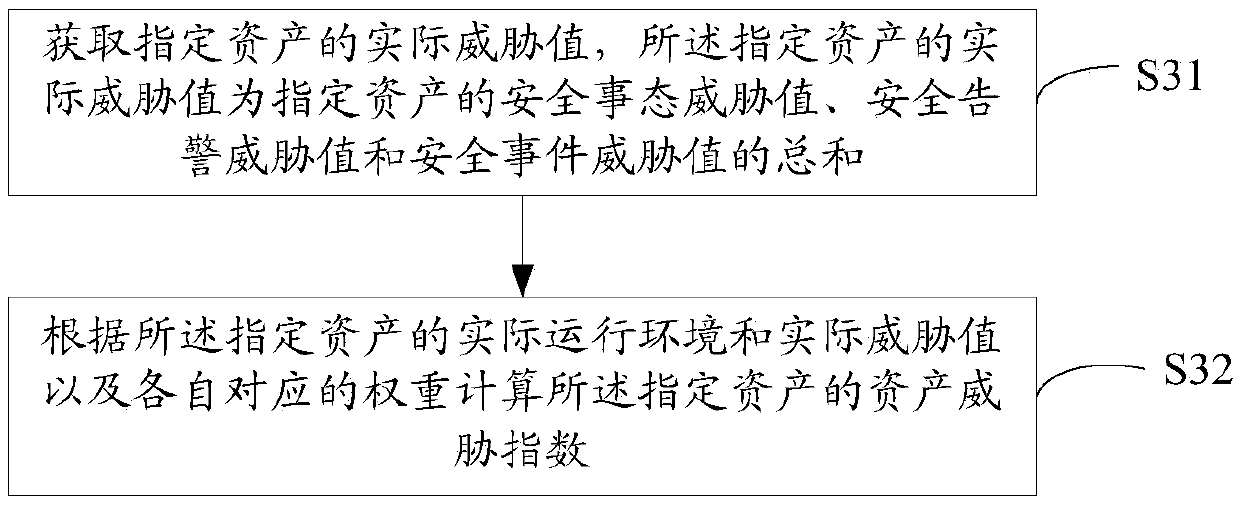
[0182] It should be noted that a customer has multiple business systems, so the security status at the customer level is determined by all business systems belonging to the customer. The data processing method of the network security situation assessment process at the customer level includes: calculating customer security index, customer threat index and customer vulnerability index.
[0183] As a specific embodiment of the present invention, the method for calculating the customer safety index is as follows Figure 7 shown, including:
[0184] S71. Respectively obtain the security risk indices of all business systems owned by a customer and the weights of each business system level:
[0185] According to the data processing method described in the second embodiment, the security risk indexes of all business systems owned by a customer are obtained respectively.
[0186] It should be noted that, in the embodiment of the present invention, different service systems are set w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com