Distributing secret keys for managing access to ECUs
An encryption key and authorization key technology, applied in the field of electronic control units, can solve problems such as consuming computing space and resources, system problems, and complex databases
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
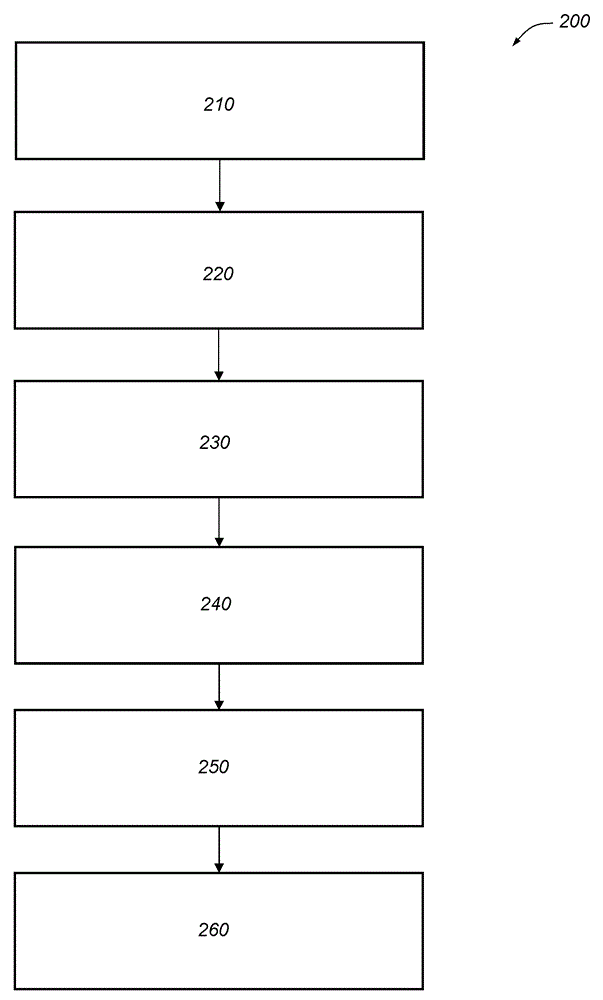
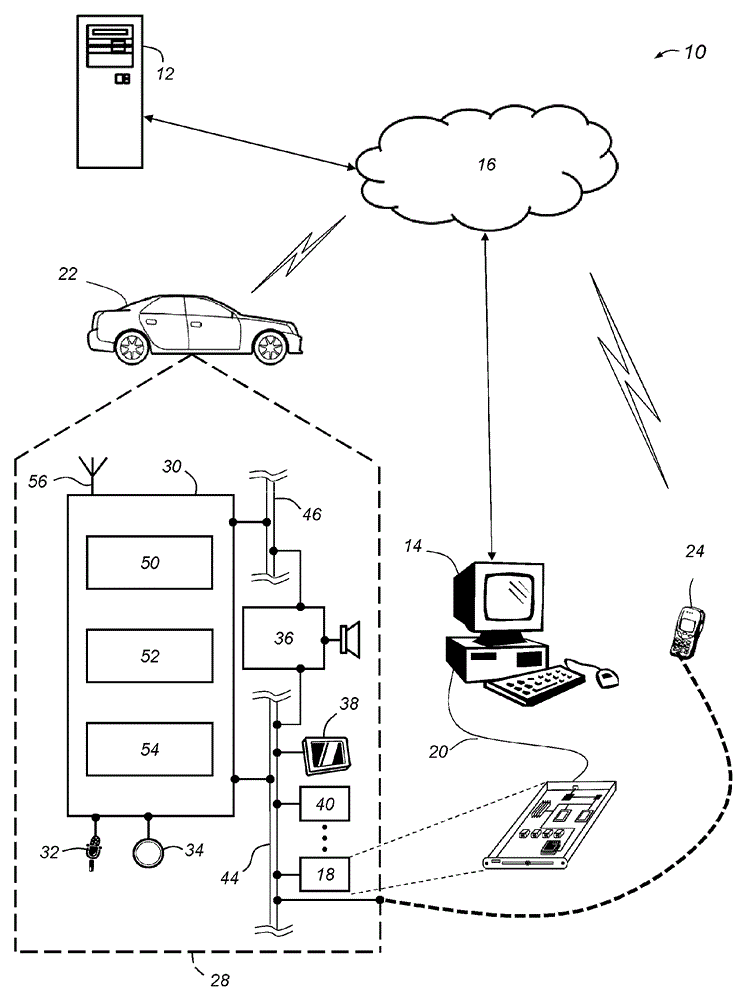
[0044] The system and method described below control access to the electronic control unit (ECU) by using a secret master encryption key that is cryptographically manipulated by the supplier identifier assigned to each ECU supplier Generate a unique supplier encryption key for each supplier or manufacturer of the ECU. Each supplier encryption key can be provided to a specific ECU supplier, and the supplier can encrypt each ECU it manufactures with the ECU identifier and a unique ECU unlock authorization key. For each ECU manufactured, the ECU supplier can generate an ECU identifier that not only uniquely identifies the ECU, but also includes a supplier identifier. The vendor encryption key and key generation algorithm can be used to process the ECU identifier so that the ECU identifier is cryptographically manipulated to create an ECU unlock authorization key that will be stored in the ECU along with the ECU identifier.
[0045] After a particular ECU is manufactured or installe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com