Virtualization technology based terminal trust enhancement method and system
A virtualization technology and a terminal technology, which are applied in the field of terminal trust enhancement methods and systems, can solve the problems that the internal information leakage or tampering of the terminal operating system cannot be prevented, and achieve the effect of preventing leakage or tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
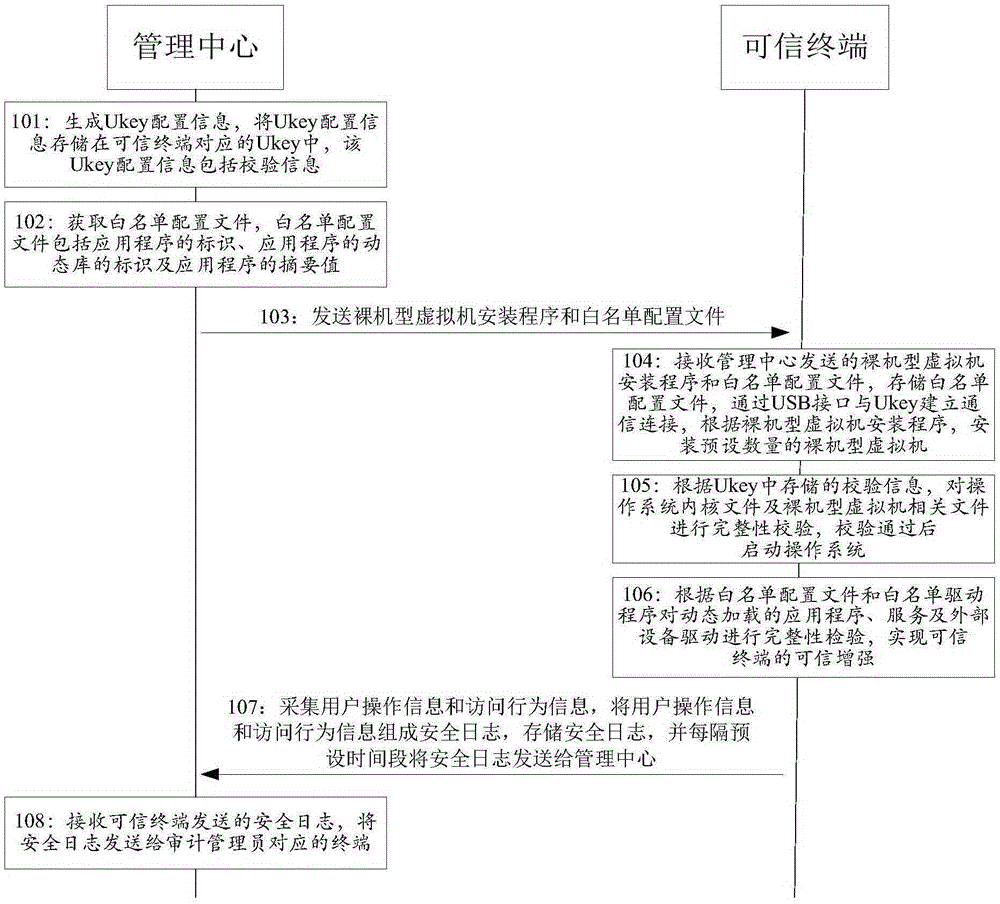
[0050] see Figure 1A , the embodiment of the present invention provides a method for enhancing terminal trustworthiness based on virtualization technology. In the embodiment of the present invention, the trusted terminal is designed and developed based on the bare-bones virtual machine technology and trusted computing technology, and the trusted terminal is managed uniformly through the management center to realize the trusted enhancement of the trusted terminal. In the present invention, the trusted terminal may be a terminal device such as a computer, a gateway, or a PAD (Portable Android Device, tablet computer). The method specifically includes the following steps:
[0051] Wherein, when realizing the trust enhancement of the trusted terminal, the management center first performs the initial configuration on the trusted terminal through the following steps 101-104.
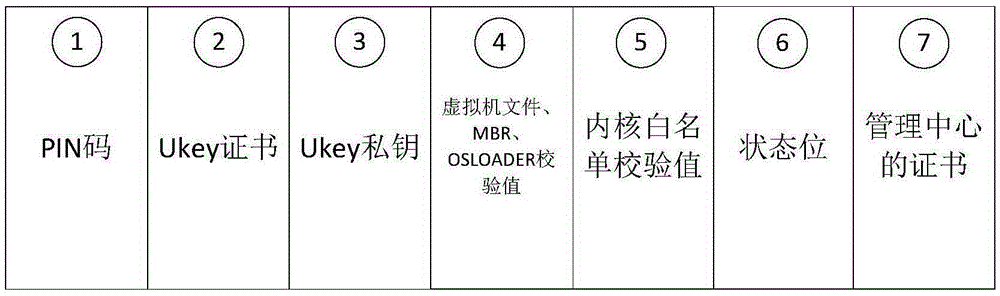
[0052] Step 101: the management center generates Ukey (small storage device) configuration information, s...
Embodiment 2
[0098] see figure 2 , an embodiment of the present invention provides a virtualization technology-based terminal trust enhancement system, the system is used to implement the above virtualization technology-based terminal trust enhancement method. The system specifically includes: a management center 201 and a trusted terminal 202;
[0099] The management center 201 is used to generate Ukey configuration information, store the Ukey configuration information in the Ukey corresponding to the trusted terminal 202, obtain the whitelist configuration file, and send the bare-model virtual machine installation program and the whitelist configuration file to the trusted terminal 202. The Ukey configuration information includes verification information, and the whitelist configuration file includes the identification of the application, the identification of the dynamic library of the application, and the summary value of the application;
[0100] The trusted terminal 202 is used to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com