Method and device carrying out path backtracking for system attack
A technology for systems and paths, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems affecting the timeliness of attack response processing, analysis of paths that cannot attack traffic, etc., to improve emergency response processing efficiency and high intelligence , Solve the effect of low degree of automation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present disclosure will be described below with reference to the accompanying drawings. It is to be noted that the following description is merely explanatory and exemplary in nature, and in no way serves as any limitation of the present disclosure, its application or uses. Relative arrangements of components and steps and numerical expressions and numerical values set forth in the embodiments do not limit the scope of the present disclosure unless otherwise specifically stated. Additionally, techniques, methods and devices known to those skilled in the art may not be discussed in detail but are intended to be part of the description where appropriate.
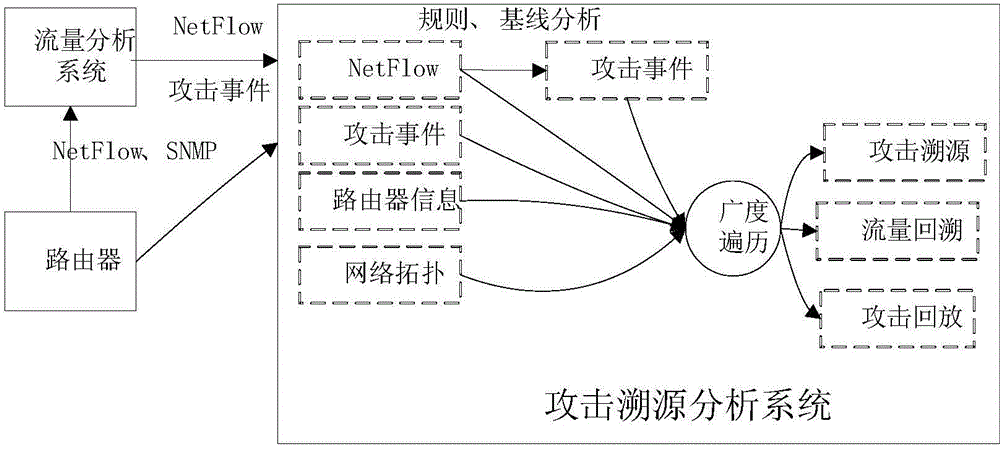
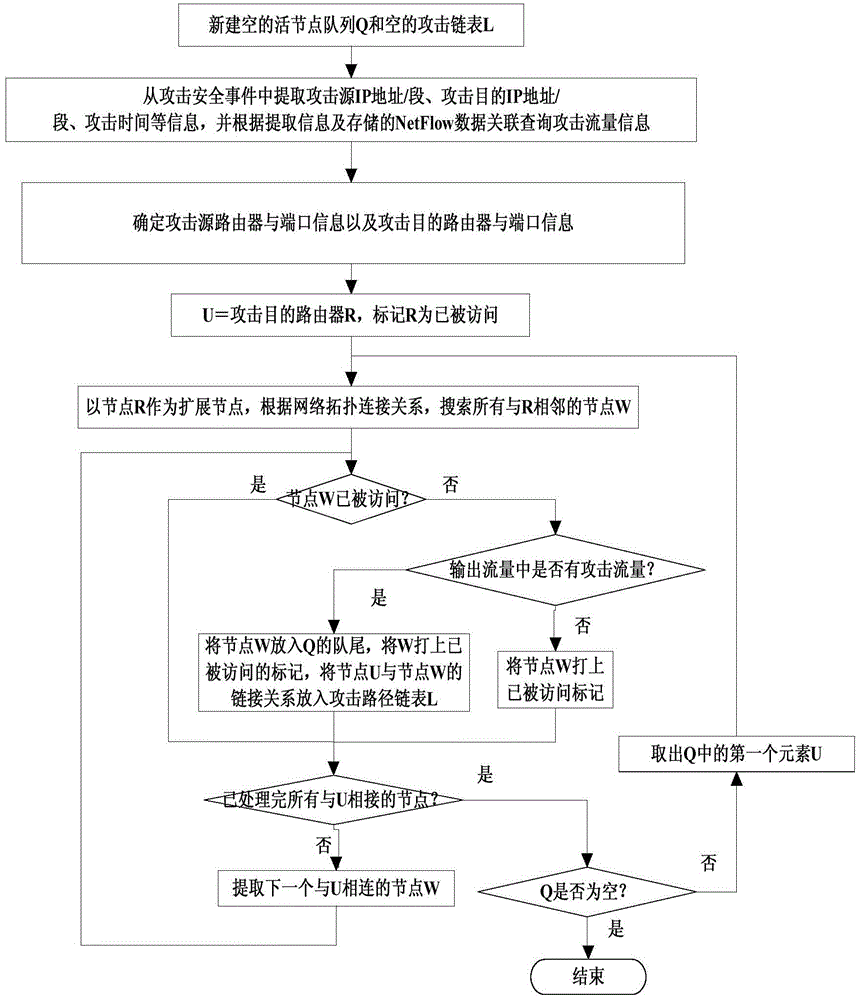
[0040] The following embodiments of the present disclosure address the problems of insufficient attack traceability and the inability to analyze the path of attack traffic in the existing technical means, and propose a technical solution for system attack path backtracking, which can effectively improve Internet a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com