Single processing system and network security isolation method based on hardware data conversion technology
A technology of data conversion and single processing, which is applied in transmission systems, electrical components, etc., can solve the problems of network data transmission efficiency reduction, CPU resource occupation, and complicated maintenance operations, so as to eliminate penetrating links, improve efficiency, and operate reliably Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
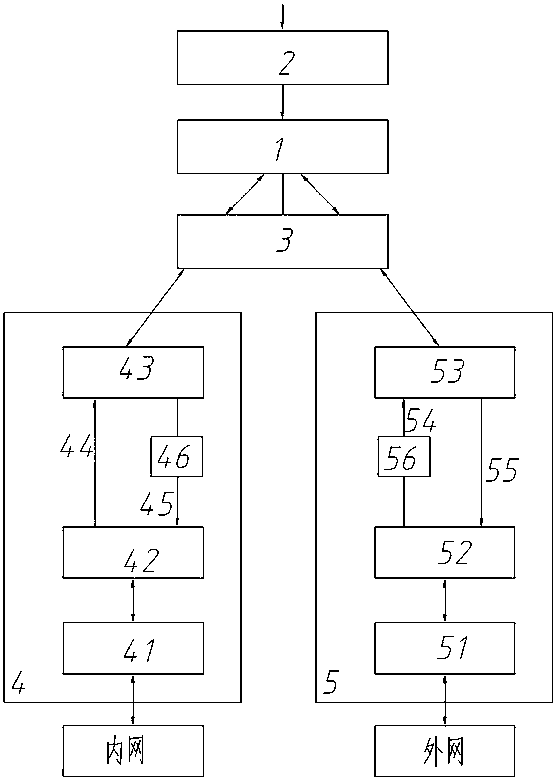
[0027] Such as figure 1 As shown, the single processing system based on the hardware data conversion technology of the present invention includes a main processing system 1, a parameter configuration interface 2, a data bus 3, an intranet network interface unit 4 containing multiple network ports, and a network interface unit containing multiple network ports. External network network interface unit 5 . The main processing system 1 may be composed of a CPU and related peripherals, or may be composed of an FPGA and related peripherals. The internal network interface unit 4 and the external network interface unit 5 can be composed of dedicated ASIC chips, or can be composed of FPGA and related peripherals that have been solidified and whose parameters cannot be changed online. Both the internal network interface unit 4 and the external network interface unit 5 have TCP / UDP network protocol offloading and hardware data conversion capabilities, and the hardware data conversion me...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com