File encryption method and electronic device
An electronic device and file encryption technology, which is applied in the electronic field, can solve the problems of low encryption security, long time-consuming encryption, and low efficiency, so as to increase the difficulty of decryption, improve encryption efficiency, and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] In an embodiment of the present invention, a file encryption method is provided, and the method is applied to a first electronic device. The first electronic device involved in the present invention includes various types of computers (such as desktop computers, notebook computers, tablet computers, all-in-one computers, etc.) ), mobile terminals (such as smart phones) and other devices with data processing functions.
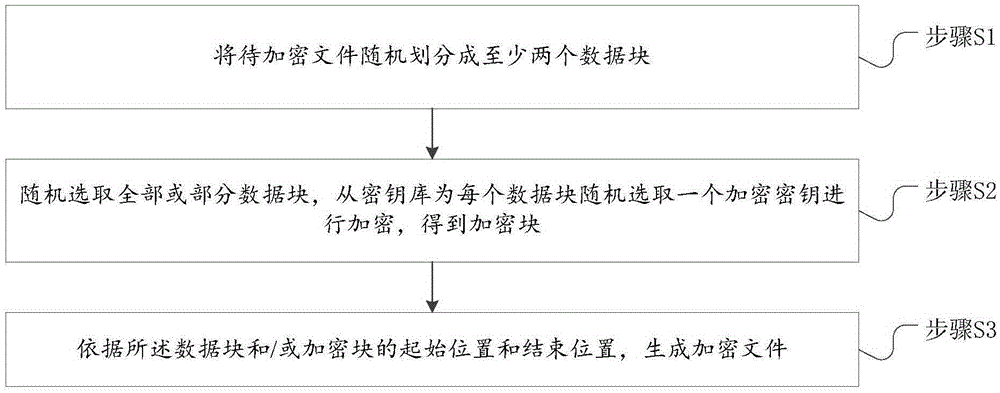
[0055] See below figure 1 , which is an implementation flowchart of the file encryption method in the embodiment of the present invention, the method specifically includes:
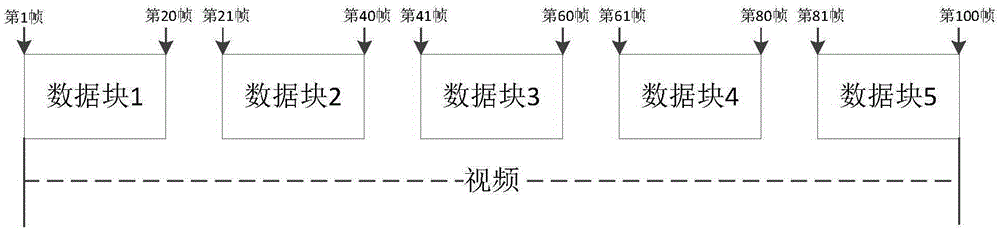
[0056] Step S1, the first electronic device randomly divides the file to be encrypted into at least two data blocks.
[0057] Specifically, the files to be encrypted involved in the present invention may include various types of data files (such as documents, pictures, audio, video, etc.) or folders.
[0058]Before dividing the data blocks, a strategy analysis may be performed on ...
Embodiment 2
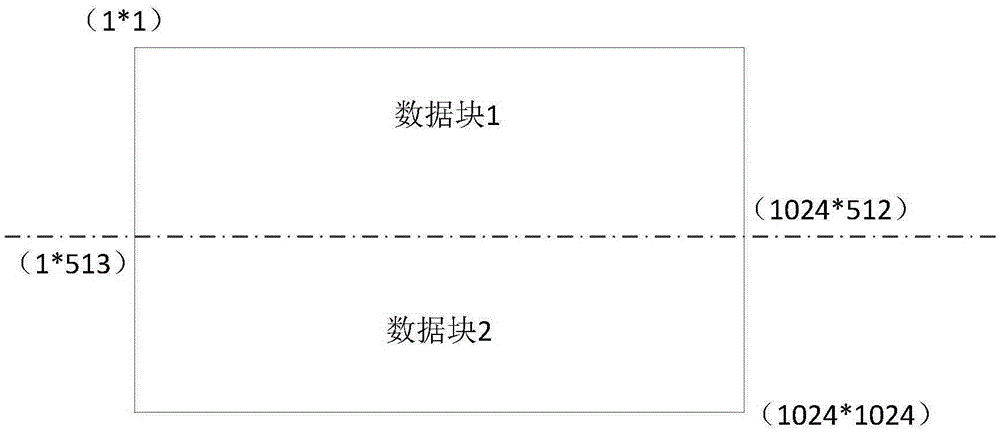
[0132] Embodiment 2: In the embodiment of the present invention, an electronic device is provided, please refer to image 3 , the electronic device includes: a division module 31 , an encryption module 32 , a first generation module 33 , and a key store 34 .
[0133] The division module 31 is used to divide the file to be encrypted randomly into at least two data blocks; the data block stores its own start position and end position in the file to be encrypted.
[0134] The encryption module 32 is used to randomly select all or part of the data blocks, and randomly selects an encryption key for each data block from the key storehouse 34 to encrypt to obtain an encrypted block; the initial block of the corresponding data block is stored in the encrypted block. position and end position.
[0135] The first generating module 33 is configured to generate an encrypted file according to the start position and end position of the data block and / or the encrypted block.
[0136] Furth...
Embodiment 3
[0151] In an embodiment of the present invention, a decryption method is provided, and the method is applied in a second electronic device, and the second electronic device involved in the present invention includes various types of computers (such as desktop computers, notebook computers, tablet computers, all-in-one computers) , mobile terminals (such as smart phones) and other devices with data processing functions.
[0152] See below Figure 4 , is a flowchart of a file decryption method in an embodiment of the present invention, including:
[0153] Step 1, the second electronic device receives the encrypted file sent by the first electronic device.
[0154] Specifically, the encrypted file is an encrypted file obtained by using the file encryption method described in Embodiment 1.
[0155] And because the first electronic device may be maliciously intercepted by other electronic devices when transmitting the encrypted file to the second electronic device, and the encryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com