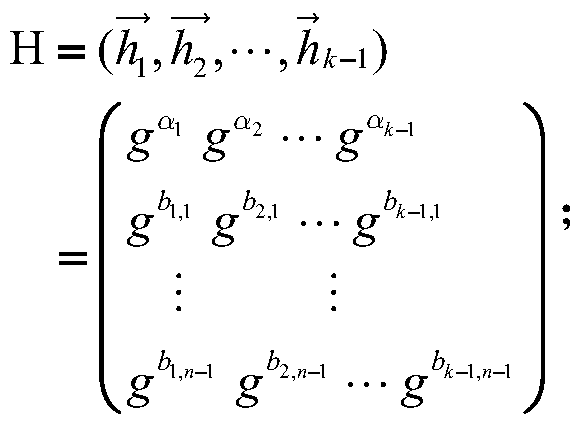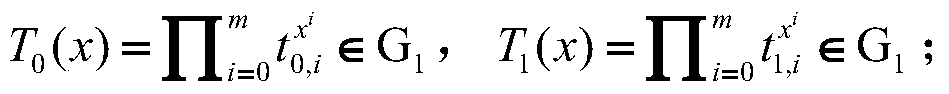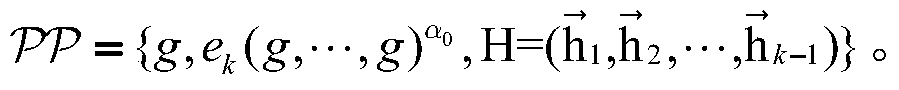Attribute Encryption Method Based on Reversible Partial Authoritative Key Strategy Based on Multilinear Mapping
An attribute encryption, multi-linear technology, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0056] The present invention will be described in detail below in combination with specific embodiments.
[0057] The attribute encryption method based on the revocable sub-authoritative key strategy of multi-linear mapping is characterized in that it is specifically implemented according to the following steps:
[0058] Step 1. System parameter initialization:
[0059] The process is assuming that there are m attributes in the system, denoted as {1,...,m}, the maximum number of revoked users in the revocation list is n, the ID of the user, and the revocation list R j , where R j Indicates that the attribute ω is revoked j The user's identity list, divided into two cases or ID ∈ R j , ω is the attribute set, and the message is The access policy is transformed into a matrix (M, ρ) through the linear secret sharing technique LSSS, and it is implemented according to the following steps:
[0060] Step (1.1), let G 1 , G k-1 , G k is a group whose order is a prime number...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com