Identity authentication improving method for pattern puzzle password in Android system
A graphic unlocking and Android system technology, applied in the computer field, can solve the problems of low utilization rate of graphic passwords, uneven distribution of graphic passwords, unapplied patterns, etc., increase the difficulty of dictionary attacks and brute force cracking, and overcome usage habits , high security effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Example 1, enter the graphic to be authenticated on the graphic unlock password interface for identity verification:
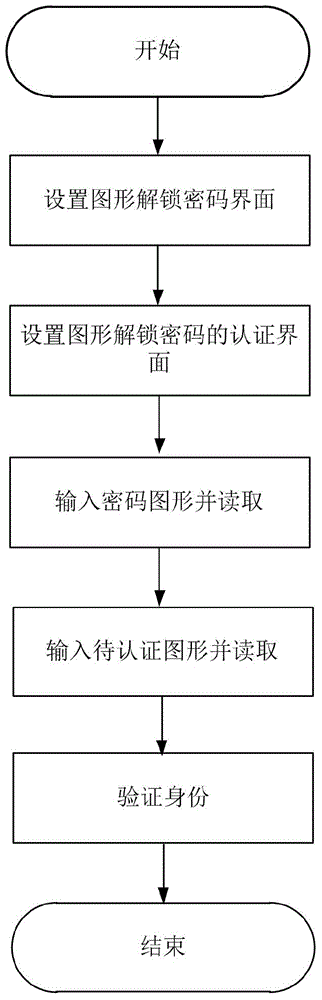
[0057]Step 1, set the graphic unlock password interface.
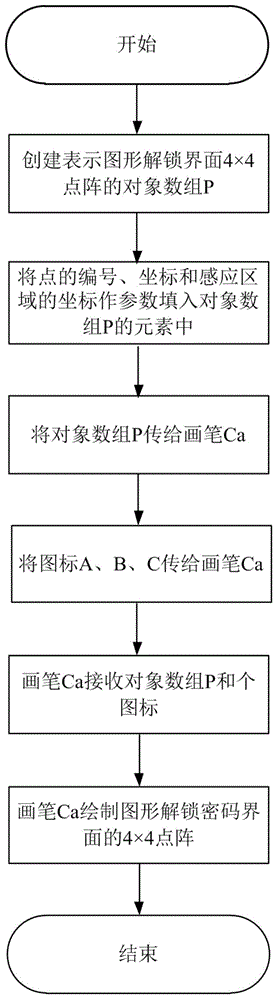
[0058] refer to figure 2 , the specific implementation of this step is as follows:
[0059] 1a) Create an object array P representing a 4×4 dot matrix of the graphic unlocking password interface;
[0060] 1b) Fill in the elements of the object array P with the number id, abscissa pX, ordinate pY of the point in the lattice, abscissa pX, ordinate pY, and the abscissa sX and ordinate sY of the sensing area as parameters, and pass the object array P to the brush Ca;
[0061] 1c) Set three icons A, B, and C for representing points, and pass these three icons to the brush Ca through the decodeResource function;
[0062] 1d) After the brush Ca receives the object array P and each icon, draw the 4×4 dot matrix of the graphics unlocking password setting interface through the drawBitmap function in t...
Embodiment 2
[0081] Example 2, enter the graphic to be authenticated on the authentication interface of the graphic unlock password for identity verification:
[0082] Step 1, set the graphic unlock password interface.
[0083] refer to figure 2 , the specific realization of this step is the same as step 1 of embodiment 1.
[0084] Step 2, setting the authentication interface of the graphic unlock password.
[0085] The specific implementation of this step is the same as that of step 2 in Embodiment 1.
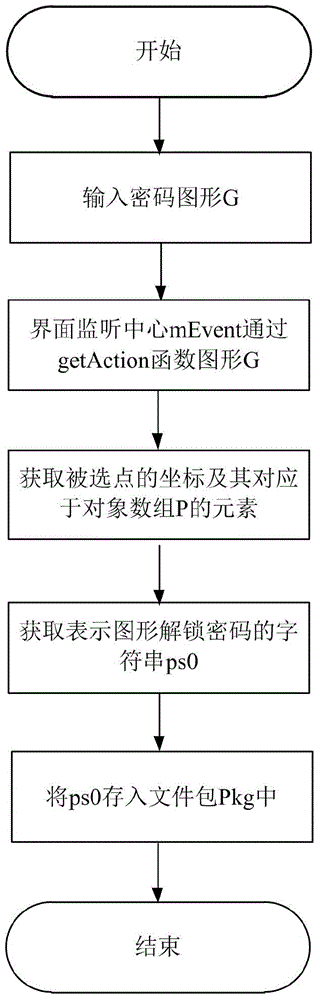
[0086] Step 3: Input the password graphic G on the graphic unlock password interface and read it.
[0087] The specific implementation of this step is the same as step 3 of Example 1.
[0088] Step 4: Input and read the graphic to be authenticated G1 on the graphic unlock password authentication interface.
[0089] refer to Figure 4 , this step is specifically implemented as follows:
[0090] 4a) Select any point from the 16 points on the graphic unlock password authentication int...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com