Image Encryption Method Based on Dynamic Key Selection of Hyperchaotic System
An encryption method and hyper-chaotic technology, which can be used in image data processing, image data processing, instruments, etc., and can solve problems such as poor randomness, image security loopholes, and dynamic key selection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
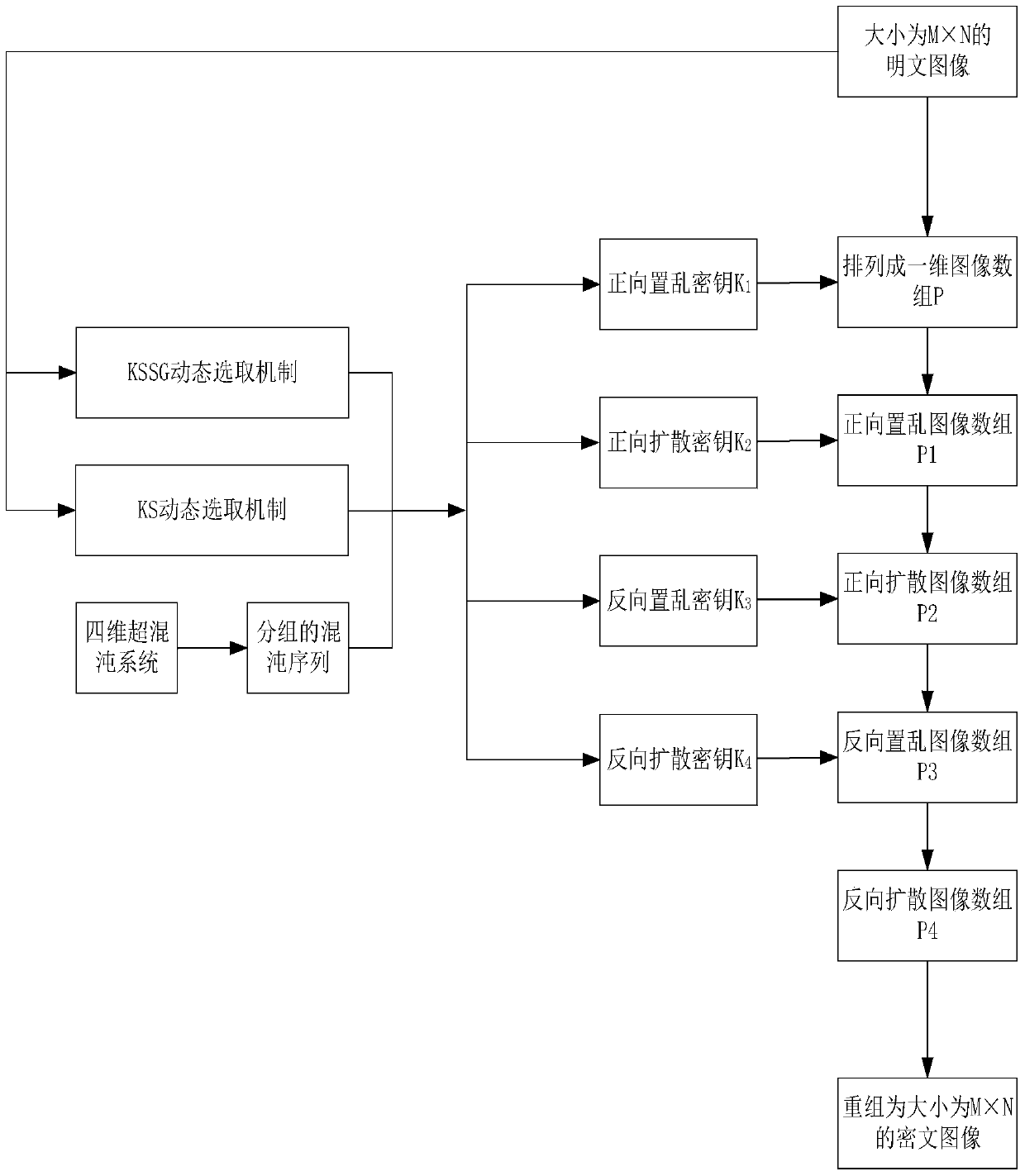
[0062] Embodiment one, a kind of image encryption method based on the key dynamic selection of hyperchaotic system, comprises the following steps:
[0063] Step 1. Input a grayscale image with an image size of M×N, and arrange the pixels of the grayscale image into a one-dimensional image array P from left to right and from top to bottom;
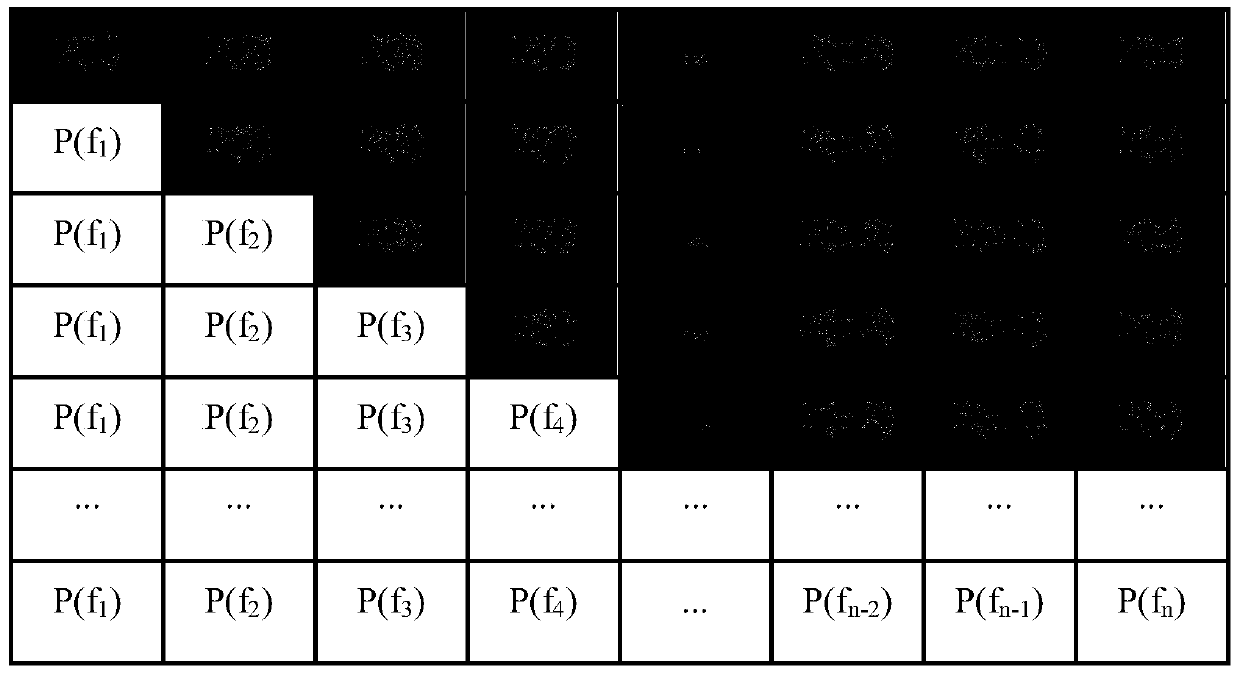
[0064] Step 2. Use the hyperchaotic system to generate chaotic sequences, and group the chaotic sequences to obtain the grouping vector A i , i∈[0,5];
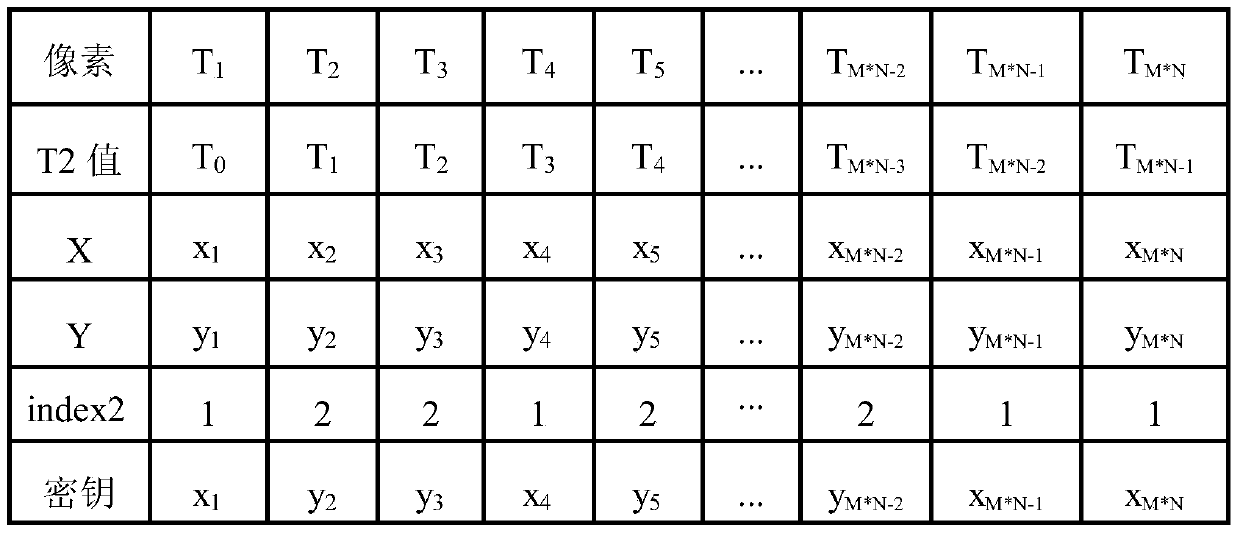
[0065] Step 3. In combination with the KSSG dynamic selection mechanism dependent on the plaintext, according to the variable index1=T1%6, i=index1, dynamically select A for generating the scrambling key i , T1 is the calculation formula based on plaintext pixels T1=mod(floor(y 0 ×10 8 ),M×N) calculated non-negative integers, where, a i Indicates the i-th element of the original image array P, max(a i ) means to take the maximum value in the array P, floor(x) means the largest intege...
Embodiment 2
[0070] Embodiment 2: To further introduce the technical solution of the present invention in combination with specific images, see figure 1 As shown, the programming software adopted in this embodiment is Matlab R2014a, select the attached Figure 8 The lena grayscale image shown in (a) with a size of 512×512 is the experimental object, and the process of encrypting the lena grayscale image is as follows:
[0071] 1. Input the lena grayscale image with the original size of 512×512, use I 0 =imread('lena.bmp') read image information. Then the image I 0 According to the order from left to right and from top to bottom, they are arranged into a one-dimensional image array, denoted as P.
[0072] 2. In this paper, Chen's hyperchaotic system is used to generate the encryption key, and its equation expression is as follows:
[0073]
[0074] Here a, b, c, d and k are the control parameters of the hyperchaotic system, when a=36, b=3, c=28, d=-16 and when k is in the interval [-...
Embodiment 3
[0180] Embodiment three: in the present embodiment, the programming software that adopts is Matlab R2014a, selects the attached Figure 11 The grayscale image of boats with a size of 256×205 shown in (a) is the experimental object, and the process of encrypting the image is as follows:
[0181] (1) Input the boats grayscale image with the original size of 256×205, use I 0 =imread('boats.bmp') read image information. Then the image I 0 According to the order from left to right and from top to bottom, they are arranged into a one-dimensional image array, denoted as P.
[0182] (2) Use the hyperchaotic system to generate chaotic sequences, and then group the chaotic sequences.
[0183] (3) Combining the plaintext-dependent KSSG dynamic selection mechanism and KS dynamic selection mechanism to generate a scrambling key, and perform forward scrambling encryption on the original plaintext image array P to obtain an image array, denoted as P1.
[0184] (4) Combining the KSSG dyna...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com