Cross site request forgery vulnerability detection method and device
A technology for forging requests and vulnerability detection, applied in electrical components, transmission systems, etc., can solve problems such as false positives, false negatives, and token validity verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
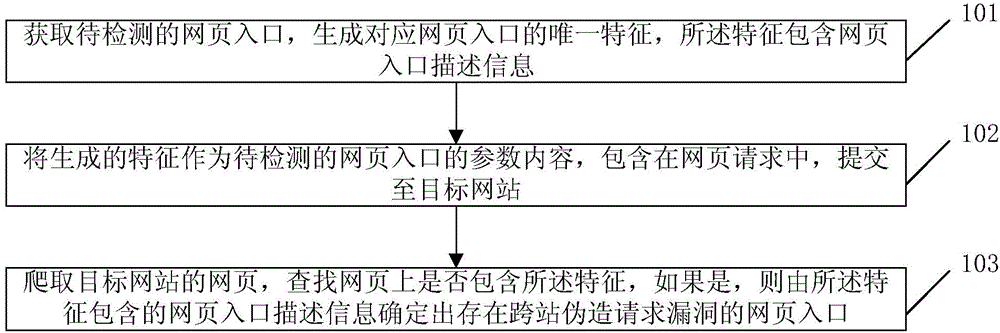
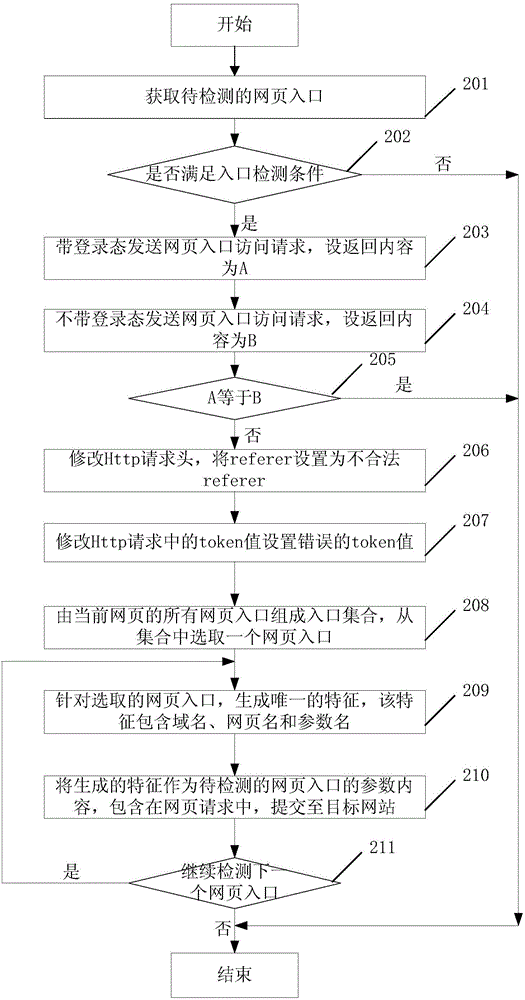
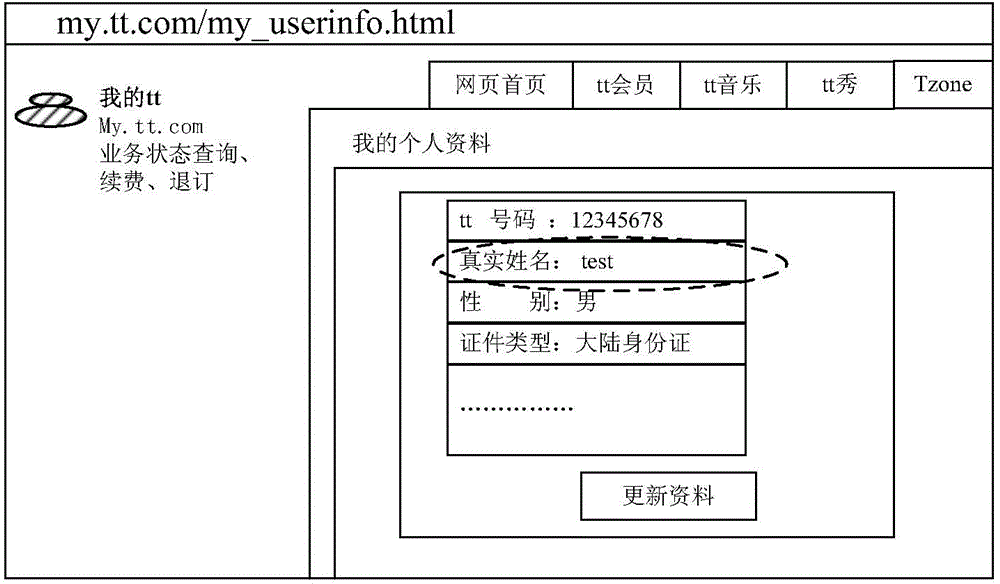
[0050] Pass below figure 2 with Figure 5 The process of the present invention will illustrate the method of CSRF vulnerability detection. See figure 2 , Is an example of a flowchart for feature setting of the present invention, which includes the following steps:
[0051] Step 201: Obtain a webpage entry to be detected.
[0052] Step 202: It is judged whether the webpage entry to be detected meets the entry detection condition, if yes, then step 203 is executed; otherwise, the process ends.
[0053] Step 203: Send a webpage entry access request with login status to the target website, and receive the webpage entry content returned by the target website, denoted as content A.
[0054] That is, the user first logs in and stores the login authentication information in the browser cookie; then, with the login authentication information, sends an access request about a certain webpage entry to the target website; the target website will process the access request and return the abou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com