Security routing method for internet of things based on topological quick check
An Internet of Things and routing technology, applied in the field of Internet of Things, can solve problems such as the inability to fully guarantee the privacy and security of terminal data, and the acquisition of sensitive data by malicious organizations, and achieve the effect of reducing route discovery overhead, improving routing efficiency, and high routing success rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to facilitate understanding of the present invention, the present invention will be further described below in conjunction with the accompanying drawings.
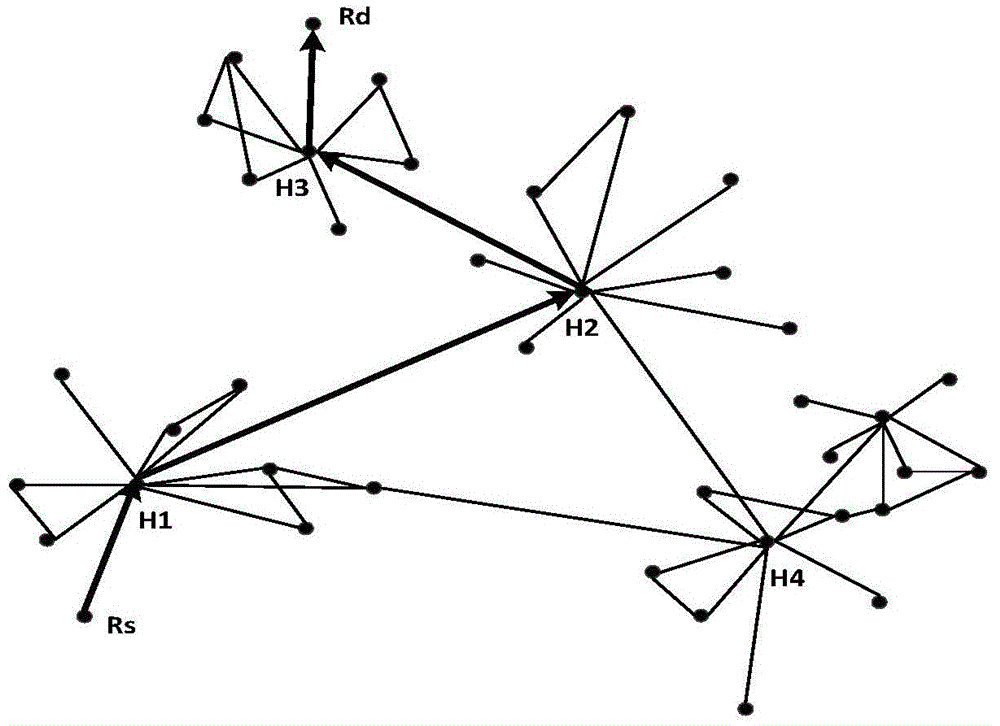
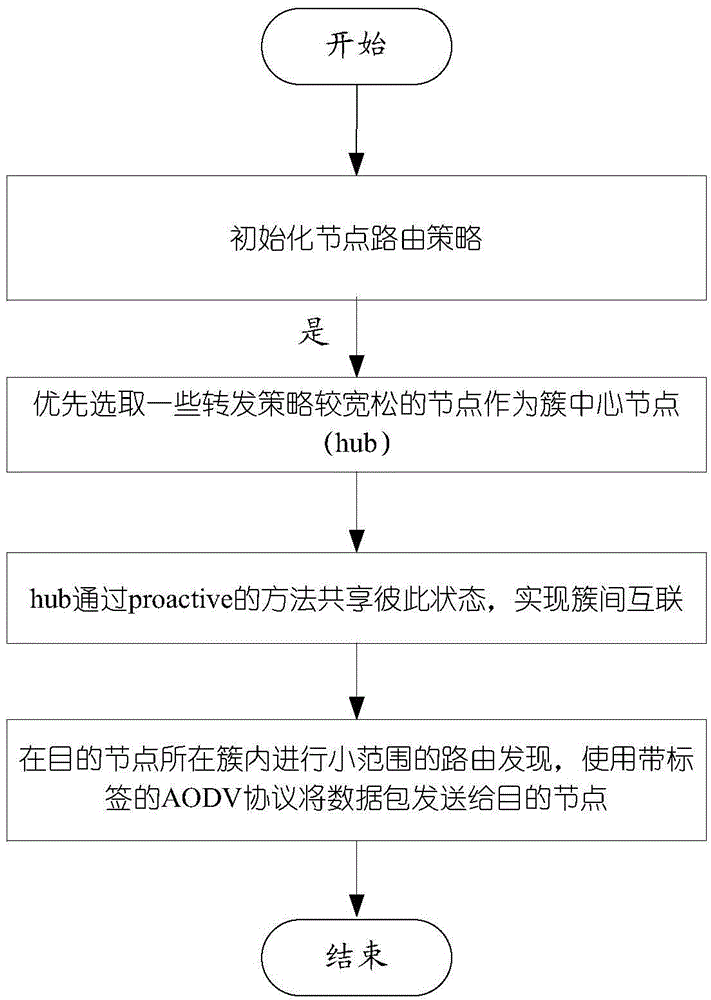
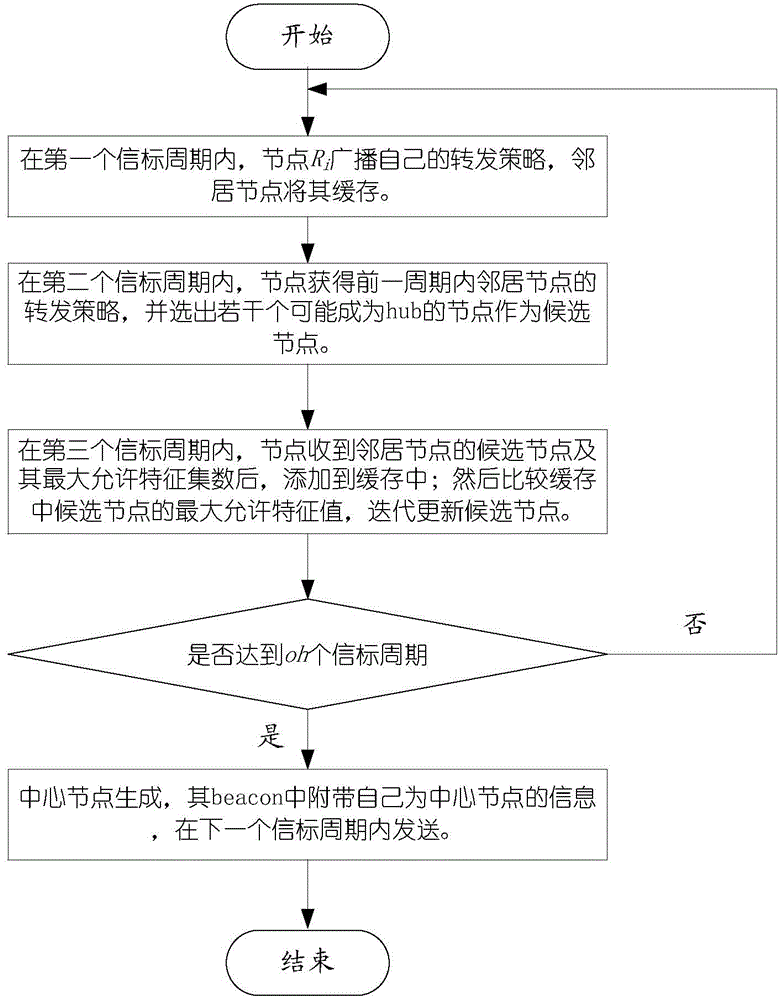
[0028] Assume agency {O 1 ,O 2 ,...,O m}Deployed several sensing nodes in the area R {R 1 , R 2 ,...,R n}, the sensing nodes are equipped with RFID and WIFI devices, and the distribution is random and uniform. Geographically adjacent sensing nodes are connected to each other to form an ad hoc network in a local area. The perception node can relay the data interacted with the terminal through the perception network, and finally transmit it to the upper layer service, see figure 1 . The IoT security routing method based on topology quick verification includes the following four steps, see figure 2 :
[0029] 1) Each organization Oi and a given application Aj also have a preset forwarding strategy. While the sensing node inherits the corresponding strategy of the organization, it also converts the st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com