Digital smart security system and method, and program
An intelligent security, digital technology that can be used in connection management, instrumentation, location-based services, etc. to solve problems such as troubles or accidents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
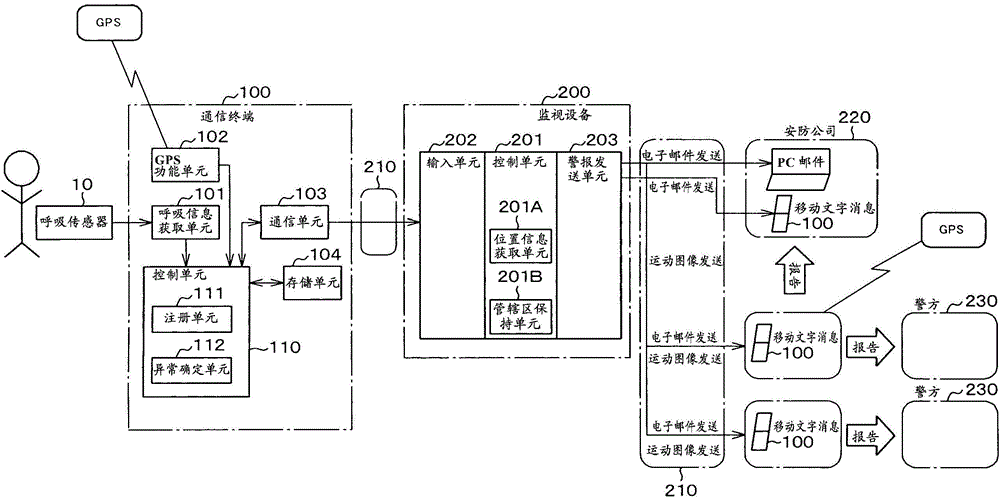
[0039] figure 1 is a block diagram showing the configuration of a digital smart security system according to the first embodiment of the present invention.
[0040] This digital intelligent security system includes a communication terminal 100 worn on the user (personnel), which can receive breathing information from a breathing sensor 10 that detects people's breathing so as to output respiratory information, and a monitoring device 200 as the main body of the digital intelligent security system equipment. , the monitoring device 200 communicates with the communication terminal 100 via the telephone line 210 .
[0041] In addition, when the digital smart security system provides security contract services to the communication terminal 100, from the perspective of the digital smart security system, the user of the communication terminal 100 may be referred to as a user.
[0042] Also, the configuration may be such that monitoring device 200 is incorporated into communication ...
example 1
[0096] Figure 7 is a flowchart showing the reporting control operation of the monitoring device 200 of the digital smart security system. This process mainly consists of the control unit 201 of the monitoring device 200 ( figure 1 )implement.
[0097] First, in step S41, the control unit 201 waits until the input unit 202 receives abnormality determination information from the communication terminal 100 through an electronic mail message. Alternatively, it may be determined whether abnormality determination information and latest position information of communication terminal 100 have been received. In this embodiment, communication terminal 100 is constituted by a mobile phone, a smart phone, etc., is capable of mobile communication, and is used at each person's location (ie, existing location). The monitoring device 200 receives the normal notification every predetermined time (for example, one hour) to store the position of the communication terminal 100 at the normal t...
example 2
[0104] Reporting Example 2 is an example of application to buildings for service operations such as shops, banks, corporate offices, stations / terminals, currency exchanges, cash vans, buses or taxis, and individuals' homes (below called stores, etc.).
[0105] A plurality of monitoring cameras are installed in the above-mentioned shops, etc., and predetermined monitoring areas can be photographed. Moreover, surveillance cameras can follow specific people or shooting locations. Even if the surveillance camera does not follow the shooting position, by installing multiple surveillance cameras, people etc. can be photographed from various angles.
[0106] A digital smart security system in a store or the like will be described.
[0107] Figure 8 is a flowchart showing the report control operation of the monitoring device 200 of the digital smart security system in a store or the like. This process mainly consists of the control unit 201 of the monitoring device 200 ( figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com