Vulnerability scanning method and device
A vulnerability scanning and vulnerability scanner technology, applied in the field of network security, can solve the problem of not being able to detect the security of the network environment, and achieve the effect of realizing security detection and increasing analysis.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
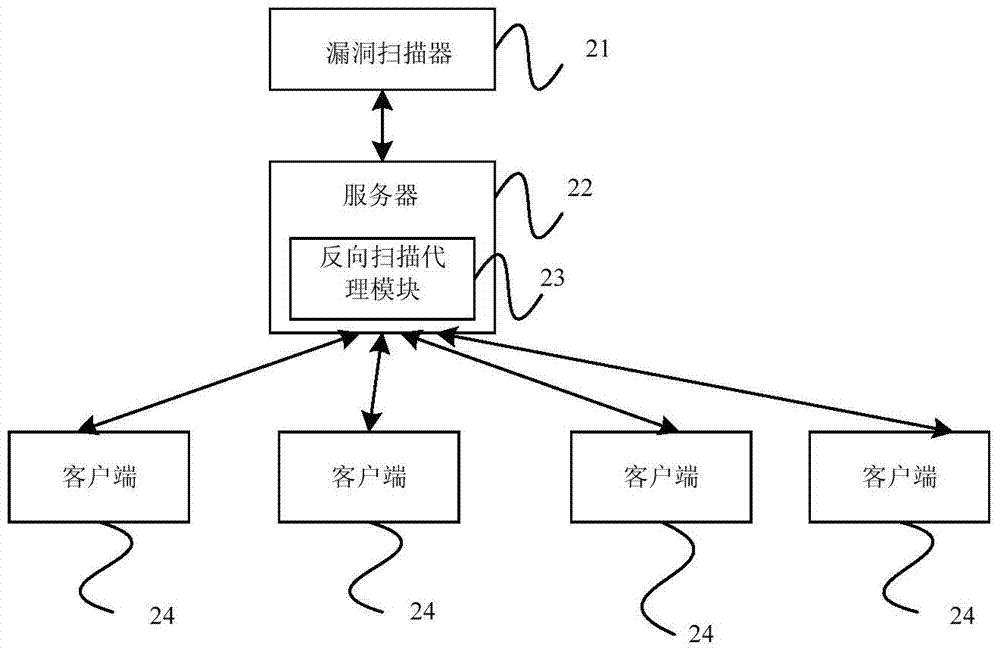
[0029] figure 1 The flowchart of the vulnerability scanning method provided by the embodiment of the present invention; figure 2 The network topology diagram provided for the embodiment of the present invention. The specific steps of the vulnerability scanning method provided by the embodiment of the present invention are as follows:
[0030] Step S101, the reverse scanning proxy module obtains the client message;
[0031] The reverse scanning proxy module is installed on the server; the reverse scanning proxy module obtains the client message including: the reverse scanning proxy module obtains the information sent by the client during the interaction process between the client and the server. or the reverse scan proxy module sends a construction test message to the client, and obtains a response message from the client to the construction test message.
[0032] Such as figure 2 As shown, after obtaining the consent of the server management side, the reverse scanning pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com