A data forwarding method with black hole attack detection
A forwarding method and black hole attack technology, applied in electrical components, transmission systems, etc., can solve the problems of accuracy discount and lack of comprehensive consideration, and achieve the effect of reducing the impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
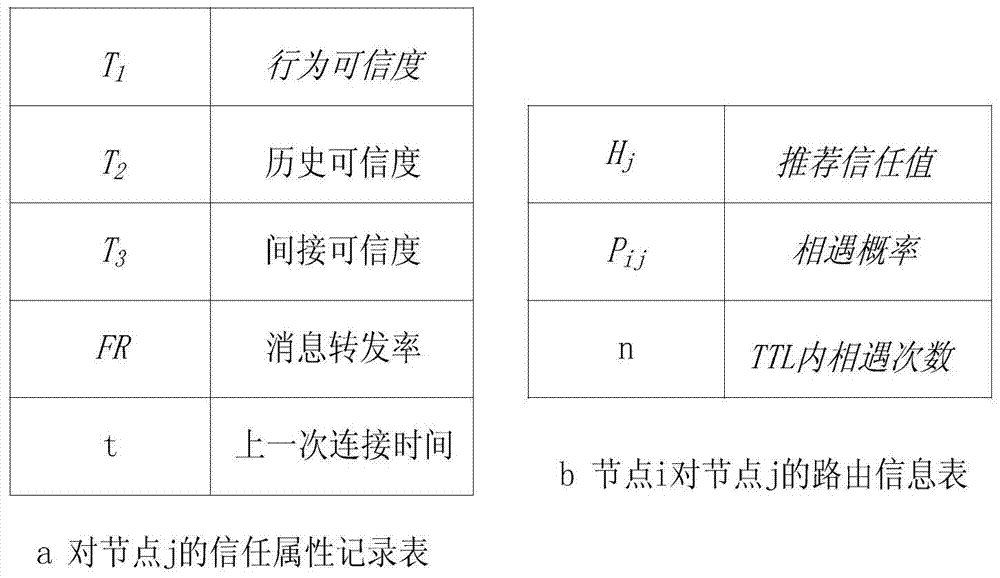
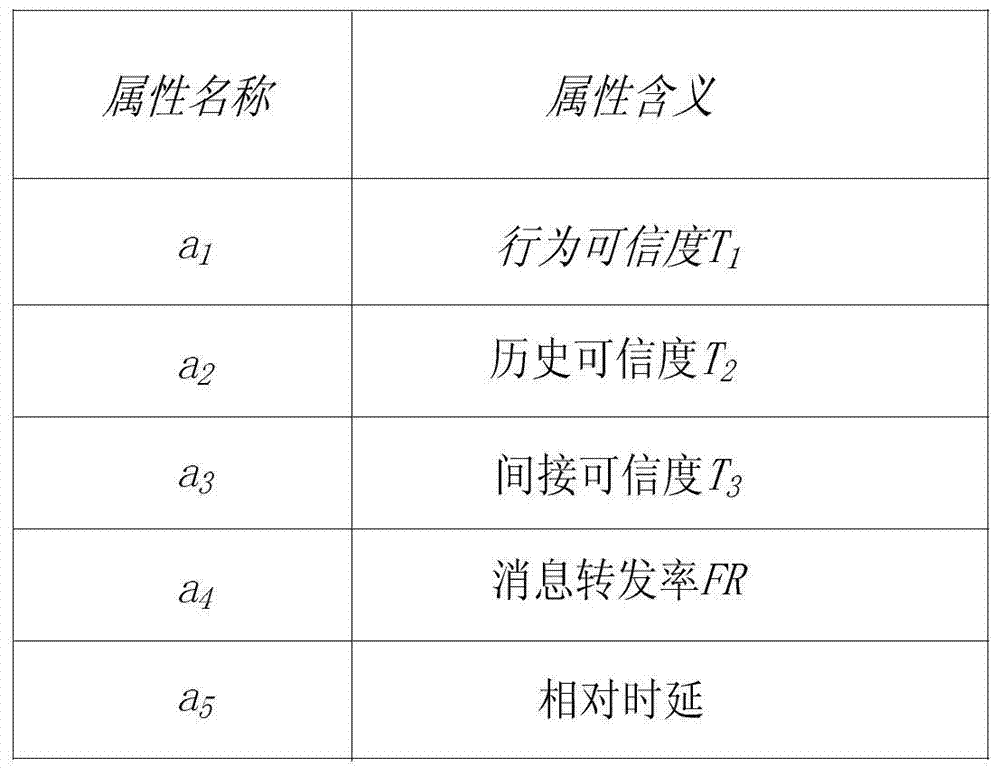
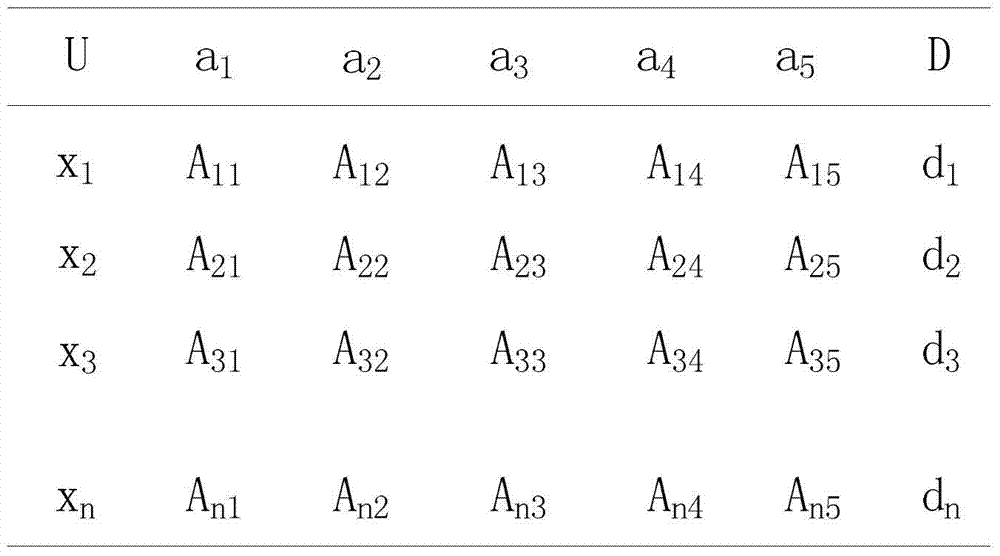
[0023]The technical solution adopted by the present invention to solve the technical problem is: according to the behavior of the nodes in the network and the characteristics of black hole attacks, when two nodes meet, the node trust value evaluation will be performed for the following attributes of the nodes: 1) each node When meeting other nodes, they will exchange summary tables, and the accuracy of the summary table is the trustworthiness of the node's behavior T 1 ; 2) The credibility of the node evaluated by this node last time is the historical credibility T of the node 2 , to measure whether the node has misbehaved in the past; 3) The node collects the evaluation of the detected node from other nodes in the network, and obtains the indirect credibility T of the node by integrating these evaluations of the node 3 ; 4) The message fo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com