Smart phone user identity authentication method based on gyroscope behavior characteristics
A user identity authentication and smart phone technology, applied in the field of smart phone user identity authentication using mobile phone sensor data, can solve the problems of touch screen traces and finger movement guessing attacks, easy to be forgotten or stolen, etc., to achieve extensive security and applicability, easy large-scale promotion, and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
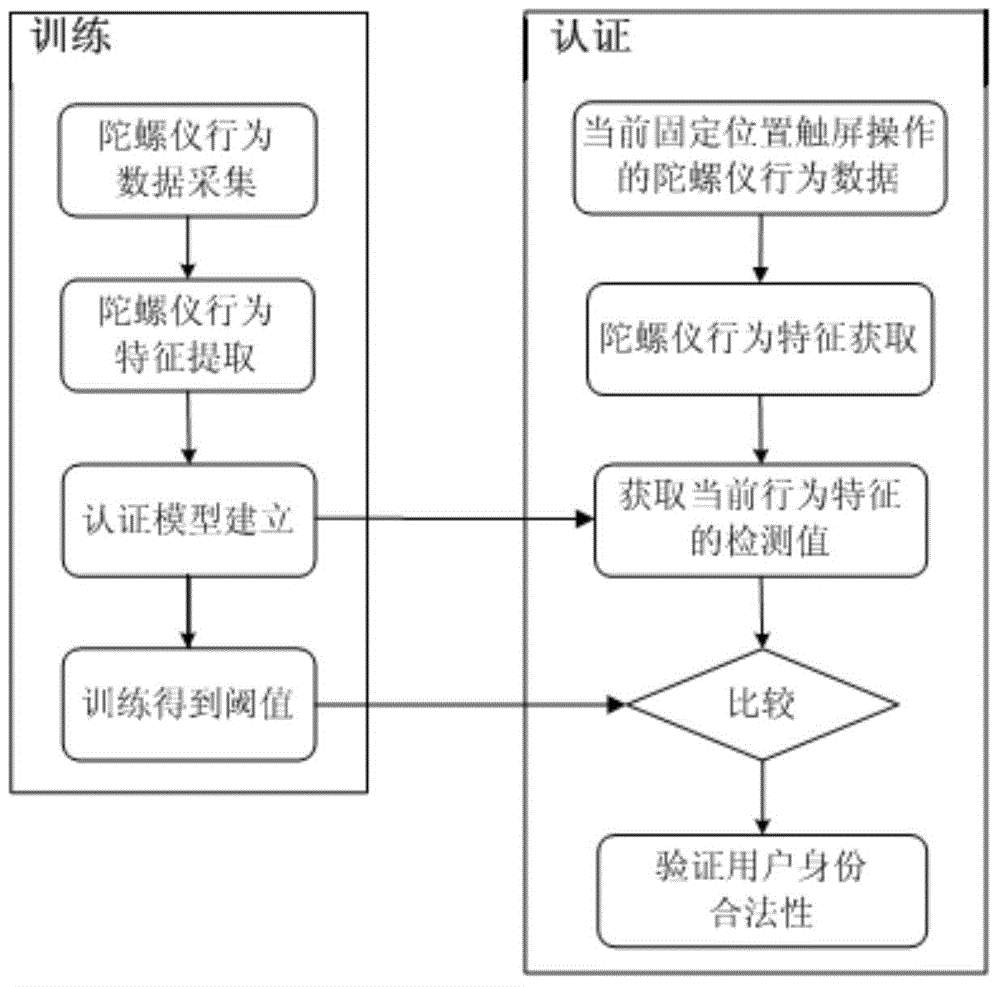
[0034] see figure 1 , a smart phone user identity authentication method based on gyroscope behavior characteristics, which can be used to authenticate the legality of the operator of the touch screen device, and realize the security protection of personal and sensitive information stored inside the touch screen device. The present invention includes two parts of identity authentication model training and operator identity authentication, and the specific implementation steps are as follows:
[0035] 1) The identity authentication model training part includes the following steps:
[0036] (1) The gyroscope collects and records the gyroscope behavior data during the user's multiple clicks and slide operations (touch screen operations) at a fixed touch screen position to obtain a training data set; the format of the gyroscope behavior data is: {horizontal direction Angular velocity in the right direction (X axis), angular velocity in the vertical upward direction (Y axis), angul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com