Method and terminal for message verification
A terminal and message technology, applied in the field of message verification, can solve the problems that affect the timeliness of PWS message verification, user terminals cannot know implicit certificates, and do not know PWS verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
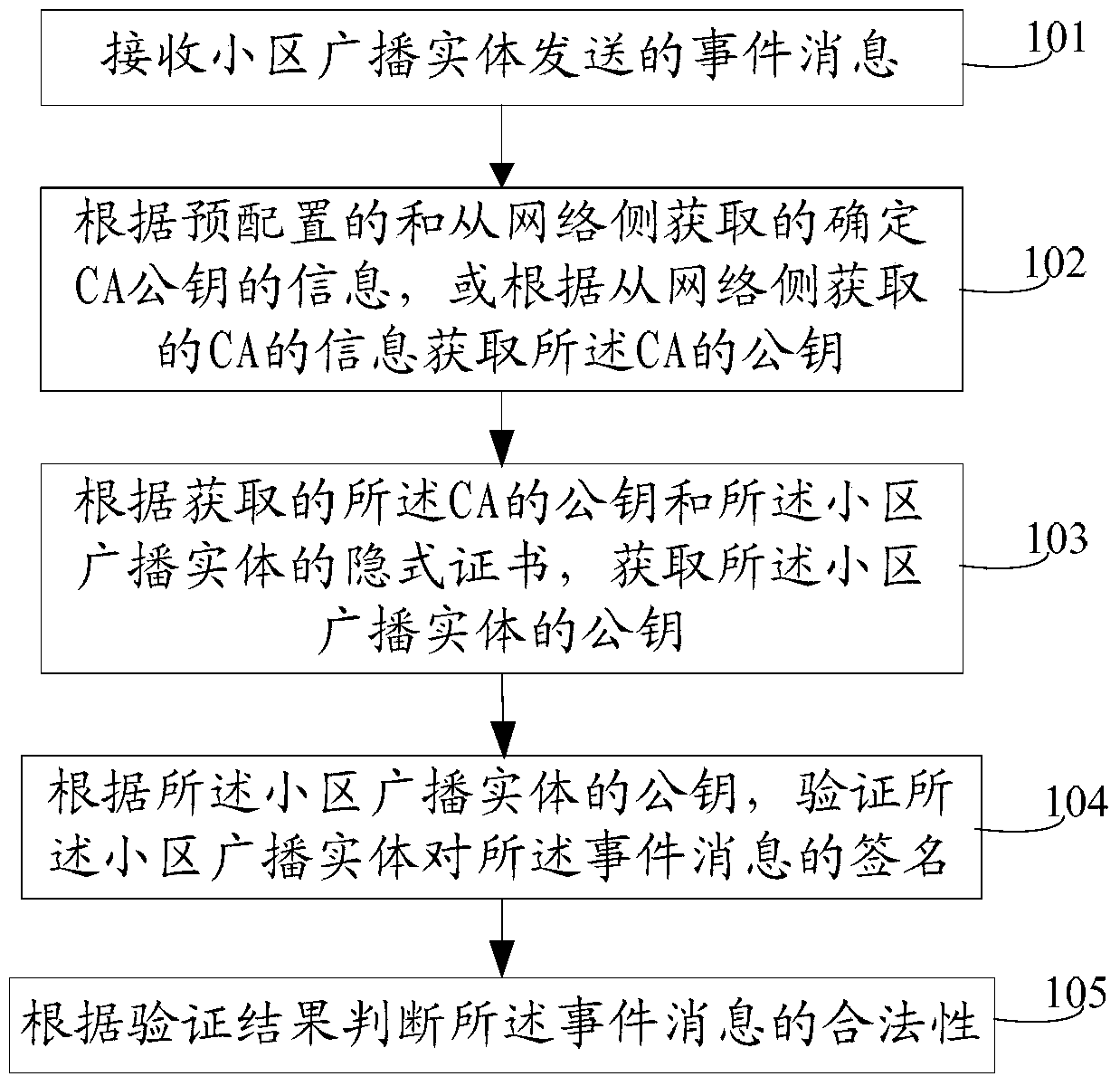
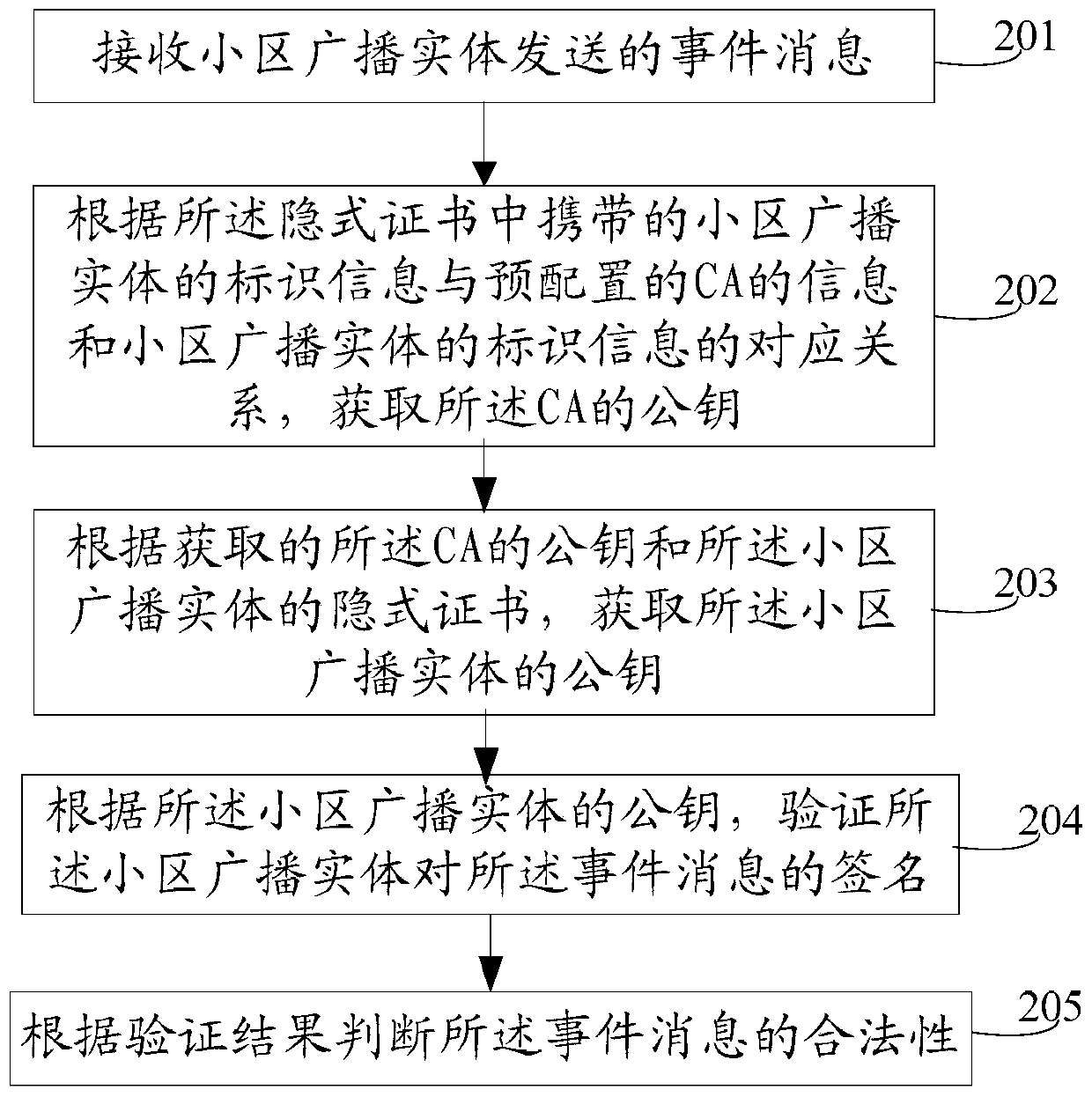
[0091] The embodiment of the present invention also provides a message verification method, which is described by using the pre-configured information for determining the CA public key as the corresponding relationship between the identity information of the cell broadcast entity and the information of the CA, specifically as figure 2 As shown, the method includes:
[0092] 201. Receive an event message sent by a cell broadcast entity, where the event message carries the signature of the cell broadcast entity on the event message and the implicit certificate issued to the cell broadcast entity by a certificate center CA, wherein the implicit The certificate carries the identification information of the cell broadcast entity.
[0093] The identification information of the cell broadcast entity is used to obtain the public key of the CA in combination with the pre-stored information for determining the CA public key; the implicit certificate issued by the CA to the cell broadca...
Embodiment 3
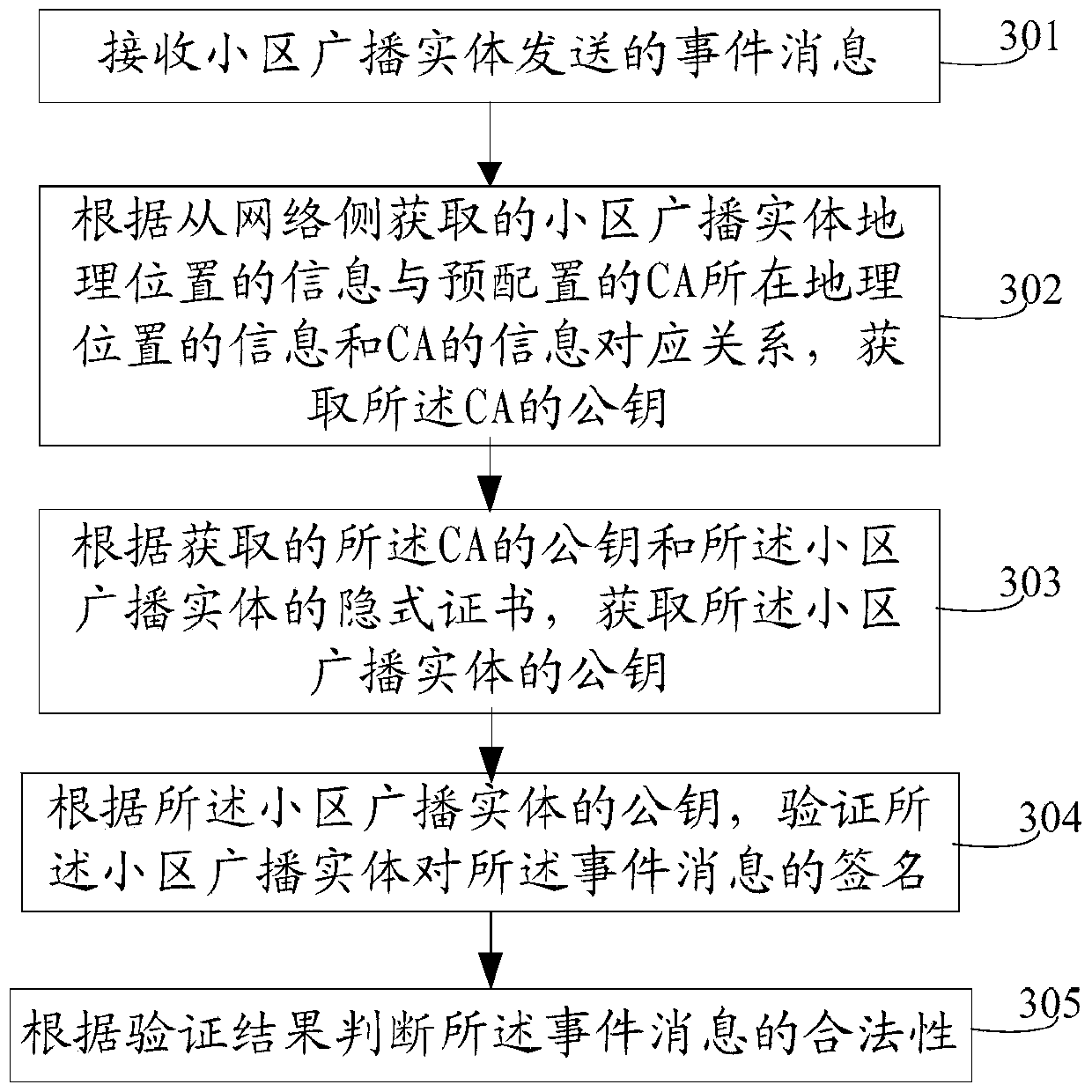
[0197] The embodiment of the present invention provides a terminal 90 for message verification, specifically as Figure 9 As shown, the terminal includes a receiver 91 and a processor 92 .
[0198] The receiver 91 is configured to receive an event message sent by a cell broadcast entity, and send the event message to the processor 92, where the event message carries a signature of the cell broadcast entity on the event message And the implicit certificate issued by the certificate authority CA to the cell broadcast entity.
[0199] The event message may be a public alarm message or other messages carrying implicit certificates, which is not specifically limited in this embodiment of the present invention.
[0200] The implicit certificate issued by the CA to the cell broadcast entity is used to obtain the public key of the cell broadcast entity; the signature of the cell broadcast entity to the event message is used to verify the legitimacy of the event message .
[0201] T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com