Pirate application identification method and device
A recognition method and application recognition technology, applied in the field of information processing, can solve the problems of limited manual matching ability, long matching time, low matching accuracy, etc., to shorten the recognition time, reduce the number, and improve the recognition efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
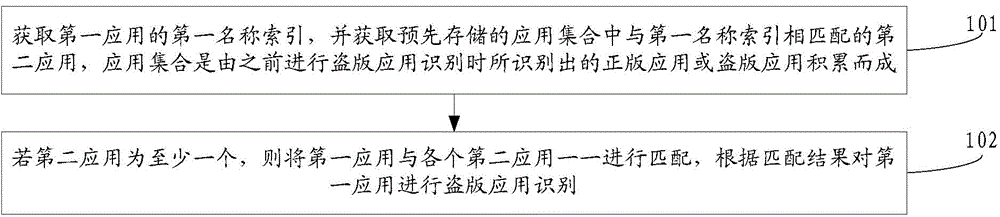
[0031] In combination with the above implementation environment, this embodiment provides a method for identifying pirated applications, see figure 1 , the method flow provided by this embodiment is specifically as follows:
[0032] 101: Obtain the first name index of the first application, and obtain the second application that matches the first name index in the pre-stored application collection, where the application collection is a genuine application or a pirated application identified in the previous identification of pirated applications application accumulated;
[0033] Optionally, acquiring a second application that matches the first name index in the pre-stored application collection includes:
[0034] Obtain the second name index of each application in the pre-stored application collection, and calculate the first similarity between the first name index and each second name index;
[0035] Screening out first similarities greater than a first preset threshold from...
Embodiment 2
[0056] Embodiment two
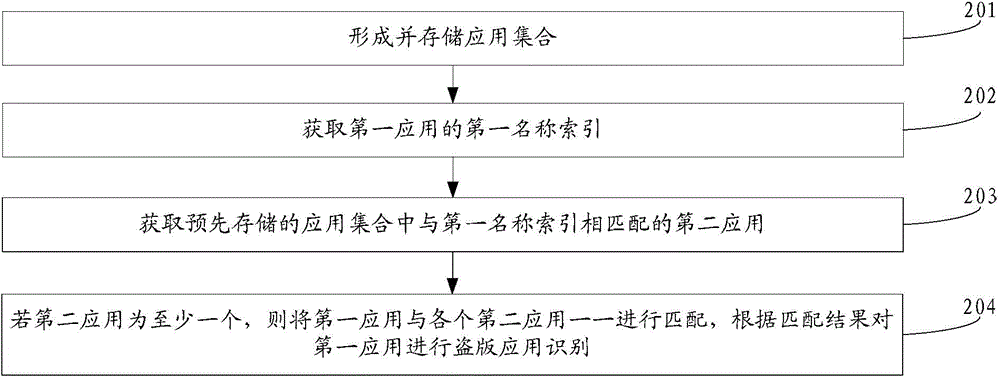
[0057] This embodiment provides a method for identifying pirated applications. For ease of illustration, this embodiment takes the first application as application A and its name as "chat tool" as an example, and describes the method provided by this embodiment in detail. see figure 2 , the method flow provided by this embodiment is specifically as follows:
[0058] 201: Obtain and store an application collection;
[0059] Wherein, the application set is accumulated according to genuine applications or pirated applications identified during the previous identification of pirated applications.
[0060] Specifically, the genuine application collection is formed according to the accumulation of genuine applications identified during the previous identification of pirated applications; or, the collection of pirated applications is formed according to the accumulation of pirated applications identified during the previous identification of pirated applicati...
Embodiment 3
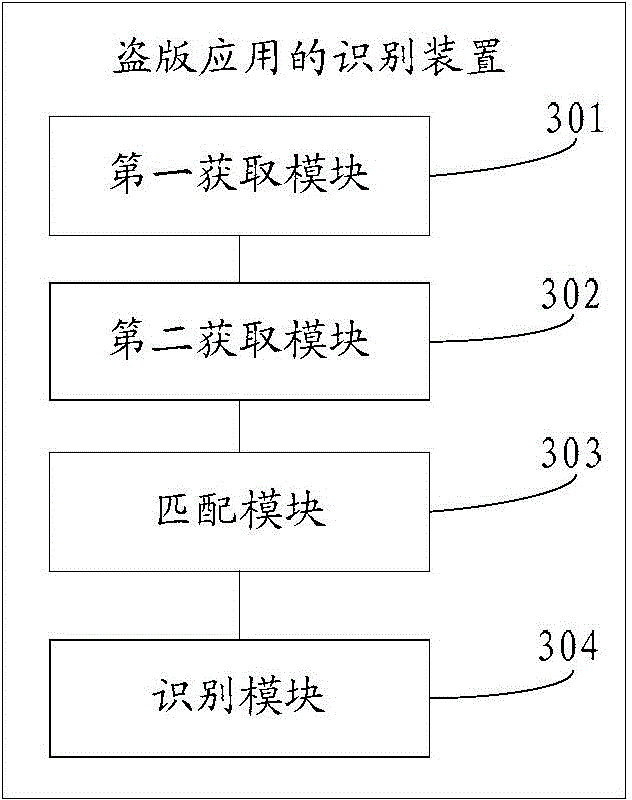
[0117] This embodiment provides a device for identifying a pirated application, which is used to implement the method for identifying a pirated application provided in Embodiment 1 or Embodiment 2 above, see image 3 , the device consists of:
[0118] A first acquiring module 301, configured to acquire a first name index of a first application;
[0119] The second acquiring module 302 is configured to acquire the second application in the pre-stored application set that matches the first name index acquired by the first acquiring module 301, and the application set is a legitimate version identified when the pirated application is identified before Apps or pirated apps are accumulated;
[0120] A matching module 303, configured to match the first application with each second application one by one when the second obtaining module 302 obtains at least one second application;
[0121] The identification module 304 is configured to identify the pirated application of the first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com