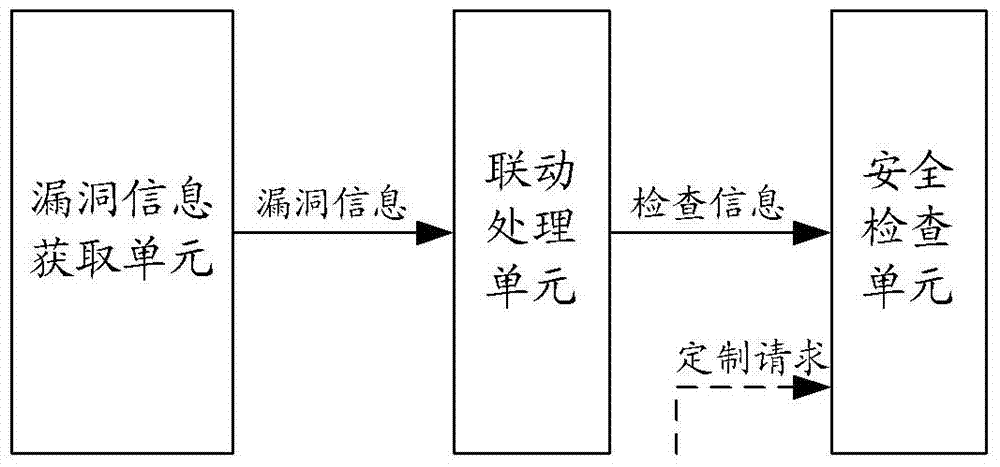
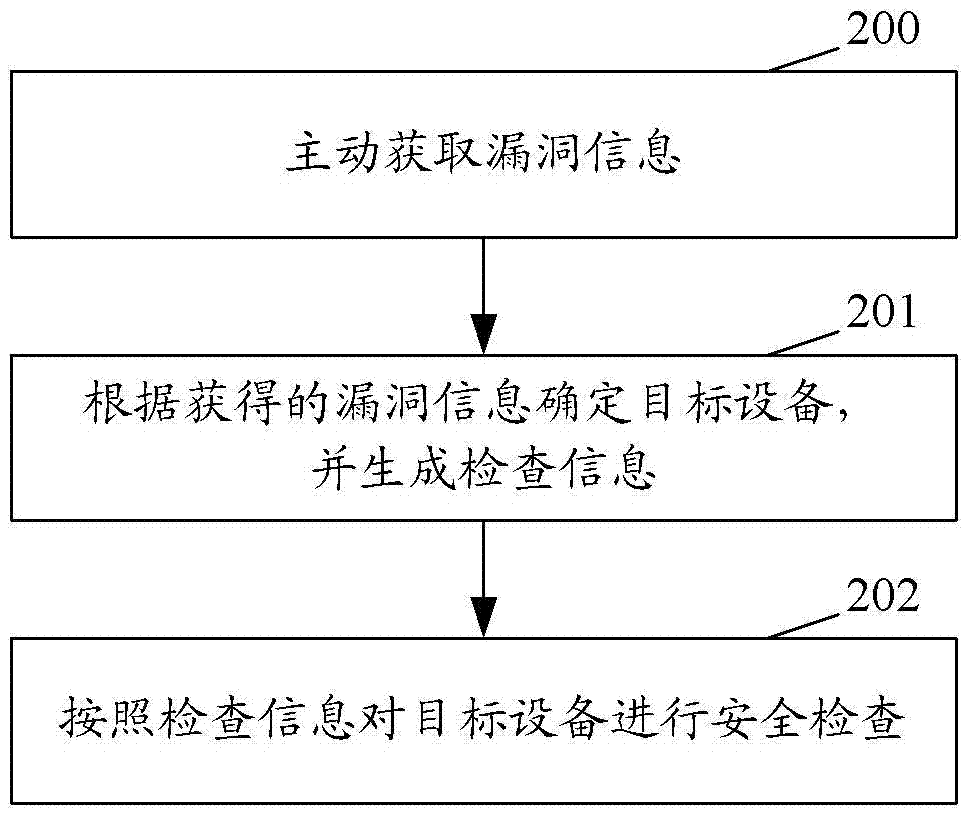
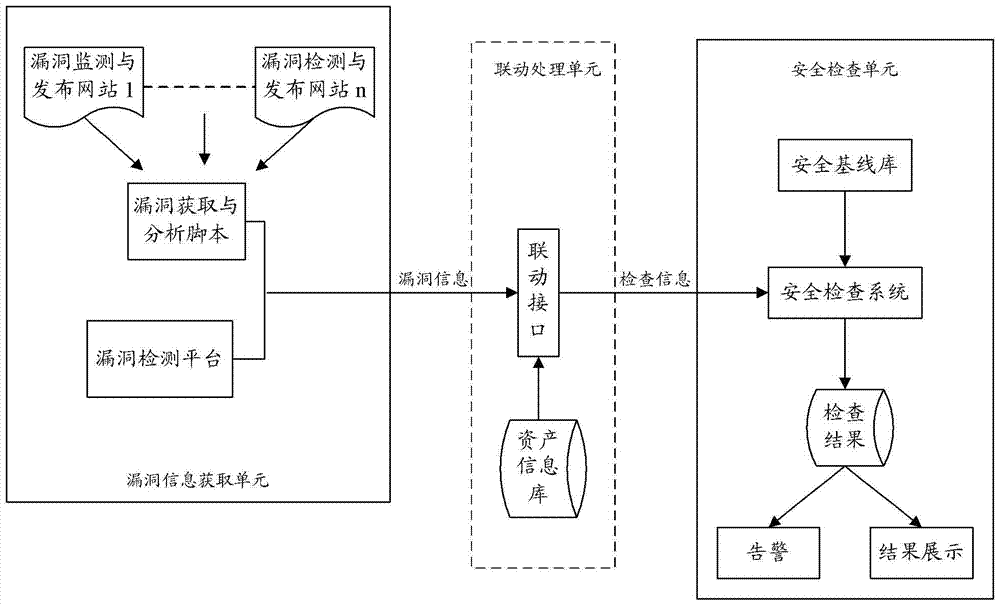
A security baseline system and its method for realizing security inspection
A security baseline and security inspection technology, applied in the field of network security, can solve problems such as inability to respond to vulnerabilities in real time, fixed security baseline database, and inability of business personnel to perform security inspections.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0087] In the first embodiment, it is assumed that the detailed information of the vulnerability includes: the basic software name (name) myname discovers the vulnerability; the affected version number (version) is m.n1, m.n2, m.n3; the cause of the vulnerability is its file (file) a The value (val) of the field (key) b is c; the standard value (std) of the field b is d; the vulnerability CVE ID is 1234; the vulnerability description (info) is xyz; the vulnerability discovery time (time) is YY-MM- DD.
[0088] The vulnerability information received by the linkage processing unit is:
[0089] {name: myname, version: m.n1|m.n2|m.n3, file: a, key: b, val: c, std: d, CVE_ID: 1234, time: YY-MM-DD, info: xyz };
[0090] The linkage processing unit combines three sets of index values (myname,m.n1), (myname,m.n2), (myname,m.n3) according to the name and version fields, and queries in the asset information base based on these conditions Identify the devices that may be affected, as...
no. 2 example
[0095] In the second embodiment, it is assumed that the vulnerability summary information includes: a discovered vulnerability (name), which is represented by a dangerous process p1, and the vulnerability CVE ID is 1234; the vulnerability description (info) is xyz; the vulnerability discovery time (time) is YY-MM- DD.
[0096] The vulnerability information received by the linkage processing unit is: {name:p1, version:null, file:null, key:null, val:null, std:null, CVE_ID:1234, time:YY-MM-DD, info:xyz };
[0097] The linkage processing unit combines the index value (p1, null) according to the name and version fields, and uses this as a condition to query the potentially affected equipment in the asset information database, and the result is empty (null).
[0098] The linkage processing unit assembles the vulnerability information, the target device, and the baseline template identifier (assumed to be tempalte:T1 in the second embodiment) to generate inspection information as: {n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com