Data protection system and method for ibeacon base station
A base station and data interaction technology, applied in the field of communication, can solve problems such as iBecon data fraudulent use, achieve the effect of improving efficiency, reducing the risk of being fraudulently used, and reducing manual intervention
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] This embodiment provides an iBeacon base station, including: a wireless communication module configured to establish a communication connection with a server, and configured to be electrically connected to a control module to realize data interaction between the server and the control module; and a control module, It is configured to change the identification information of the iBeacon base station, and upload the change information including the changed identification information to the server through the wireless communication module.
[0045] The iBeacon base station provided in this embodiment changes the identification information of the iBeacon base station and uploads it to the server, so as to prevent iBeacon data from being fraudulently used.
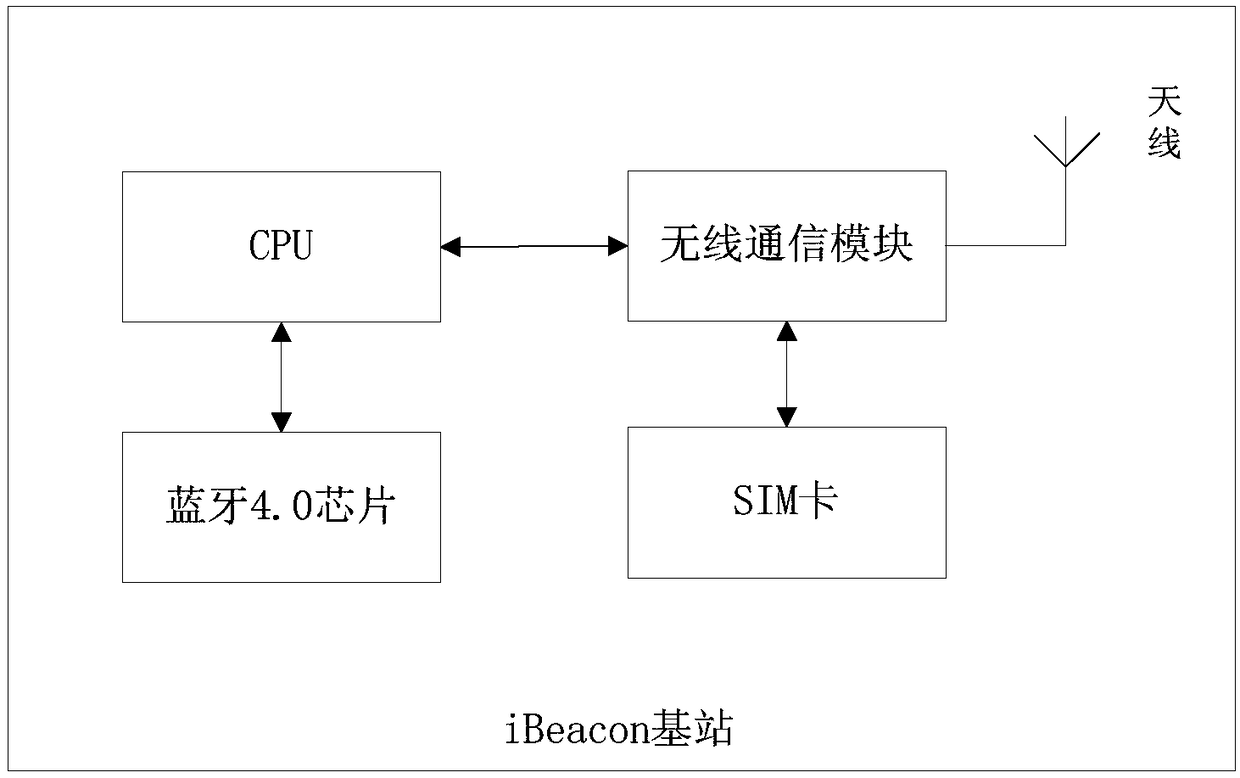
[0046] Specifically, in figure 1 In the schematic structural diagram of the iBeacon base station shown, the control module is implemented by a CPU. In one embodiment, the control module is electrically connected to the w...
Embodiment 2
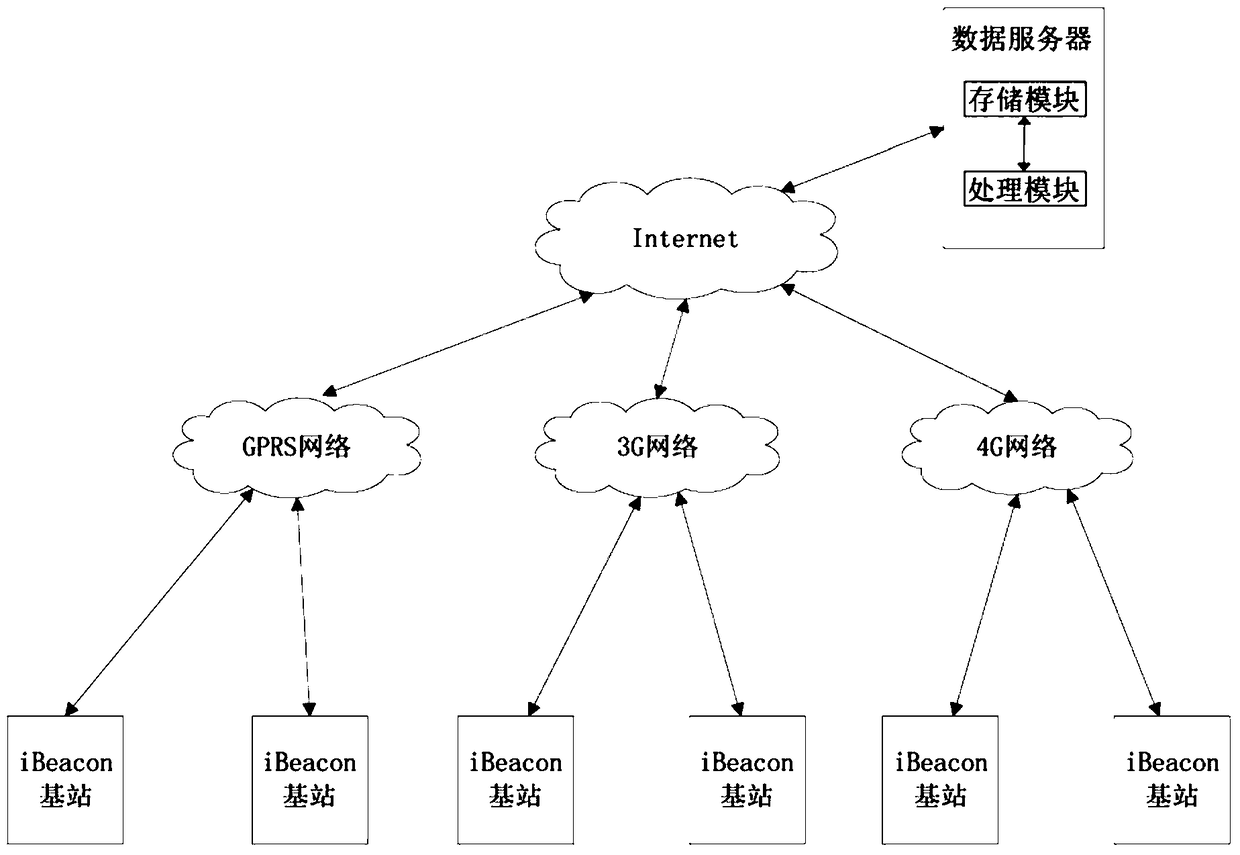
[0054] Such as figure 2 As shown, this embodiment provides a data protection system for iBeacon base stations. The application scenario is set as follows: 6 iBeacon base stations are deployed at different locations in a large store, and the store store map drawn according to the real scene inside the store is stored in the server. The position of the iBeacon base station is marked with three-dimensional coordinates on the corresponding position in the map after measurement (i.e. location information). The correspondence between the location information of the iBeacon base station and identification information (eg, identification information such as UUID, MajorID, and MinorID of the iBeacon base station) is stored in a mapping table. In this embodiment, 2 iBeacon base stations have built-in 3G communication modules, 2 iBeacon base stations have built-in 4G communication modules, and 2 iBeacon base stations have built-in GPRS modules. It should be noted that the number of iB...
Embodiment 3
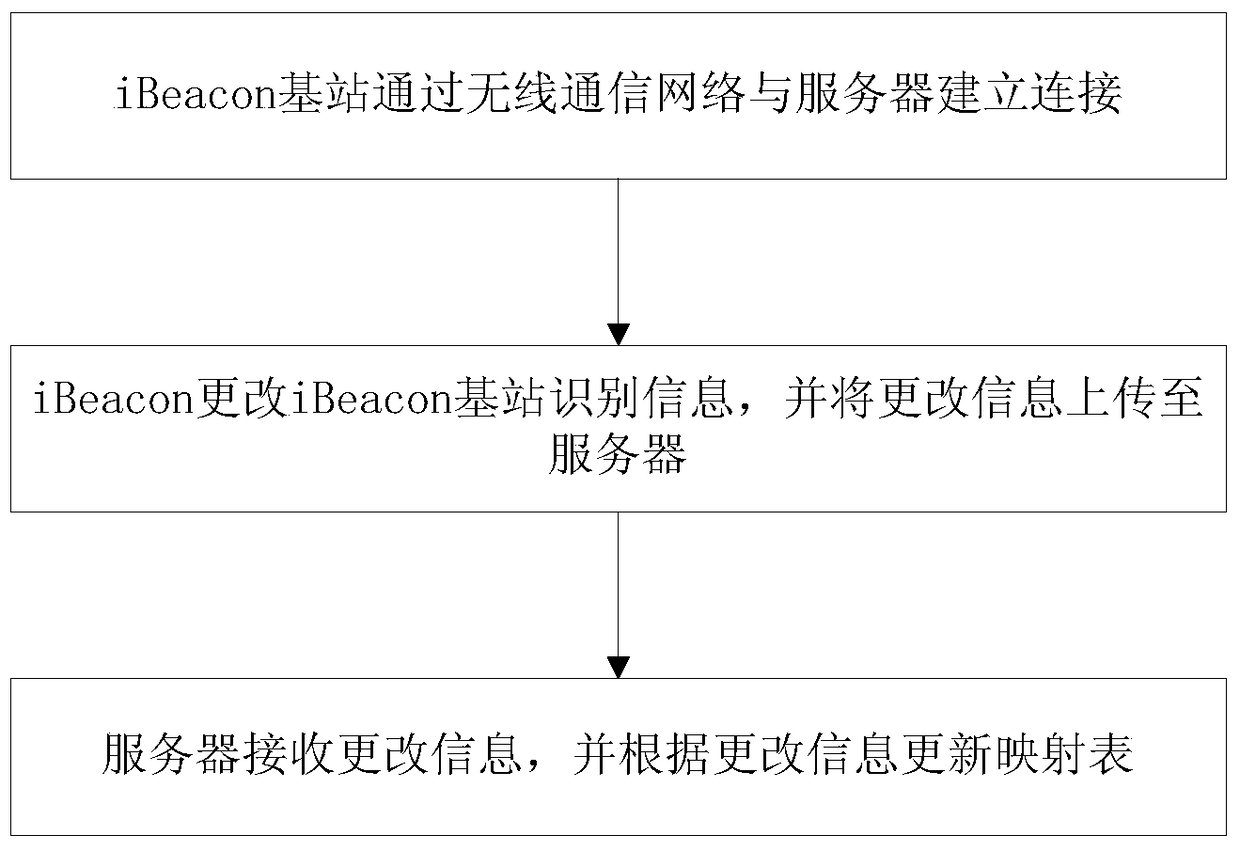
[0064] Such as image 3 As shown, this embodiment provides a data protection method for an iBeacon base station, which specifically includes the following steps:
[0065] Step 1: The iBeacon base station establishes a communication connection with the server through the wireless communication network;
[0066] Step 2: The iBeacon base station changes the identification information of the iBeacon base station, and uploads the change information including the changed identification information to the server;
[0067] Step 3: The server updates the mapping table storing the correspondence between the location information and the identification information of the iBeacon base station according to the change information received from the iBeacon base station.
[0068] Through the above data protection method for iBeacon base stations, the corresponding relationship between the location information and identification information of iBeacon base stations is in a state of constant ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com