Method and system for controlling modification of user's sensitive information
A technology for sensitive information and information modification, applied in the field of Internet applications, can solve problems such as high labor costs, and achieve the effect of improving security and avoiding malicious modification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
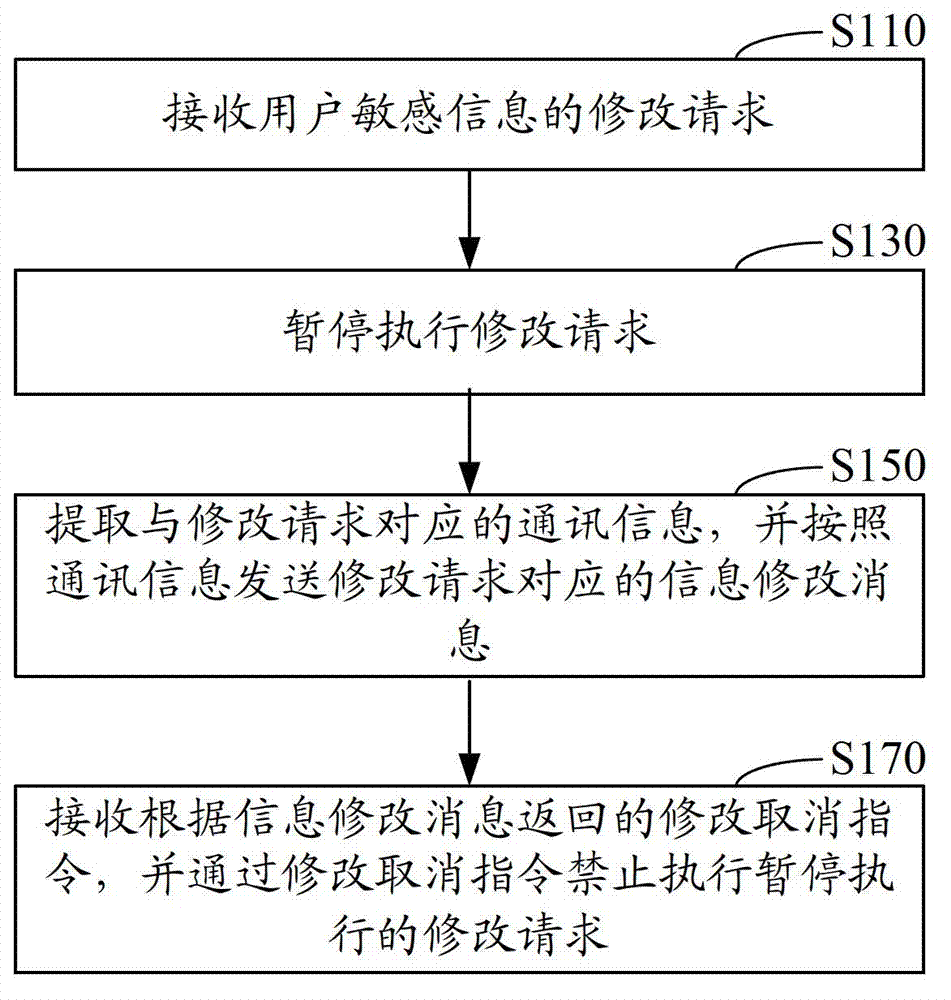
[0025] Such as figure 1 As shown, in one embodiment, a method for controlling modification of user sensitive information includes the following steps:
[0026] Step S110, receiving a modification request of user sensitive information.
[0027] In this embodiment, the modification request is used to modify the sensitive information of the user, and the sensitive information of the user is various private information related to the user stored in the background server.
[0028] When any user sensitive information modification operation is triggered, a modification request will be generated according to the modification content of the user sensitive information. The modification request includes the user ID to which the user sensitive information belongs and the modification content. The information modification request can know which user sensitive information corresponding to the user ID triggers the modification operation, and the content to be modified in the user sensitive ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com