Third-party login information hosting method and system
A technology for login information and successful login, applied in the field of Internet user login, can solve problems such as unfavorable secondary expansion, information leakage, uneven website performance, etc., and achieve the effect of increasing the difficulty of guessing, encryption method security, and hosting information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0090] The specific implementation manners of the present invention will be described in further detail below with reference to the accompanying drawings. In the following description, for purposes of explanation, numerous specific details are set forth in order to provide a thorough understanding of one or more aspects of the embodiments. It may be apparent, however, to one skilled in the art that one or more aspects of the various embodiments may be practiced with a lesser degree of these specific details. Although a particular feature or aspect of an embodiment may be disclosed with respect to only one of several implementations, such feature or aspect may be disclosed in conjunction with other implementations as may be desired and advantageous for any given or particular application. One or more other features or aspects in combination.
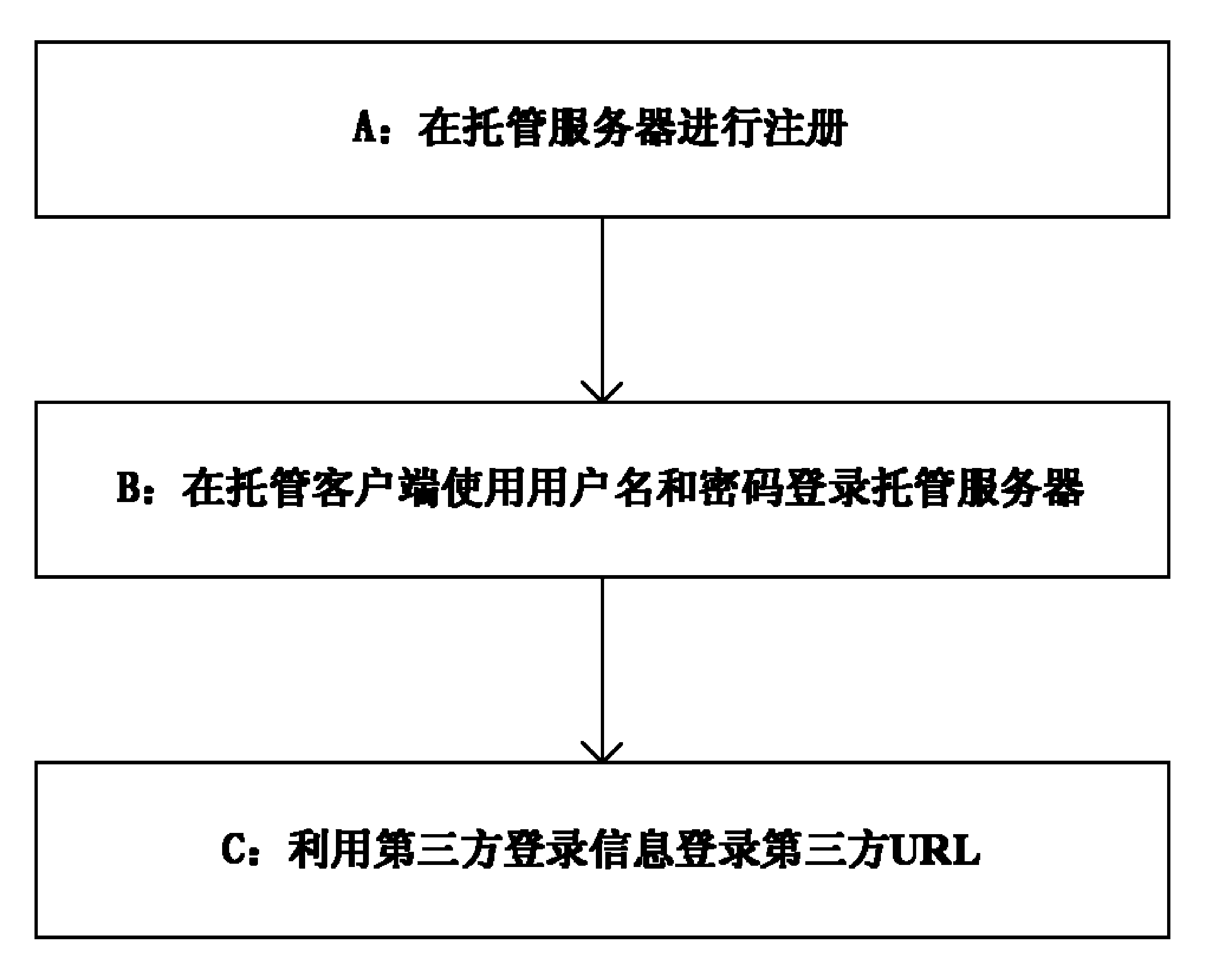
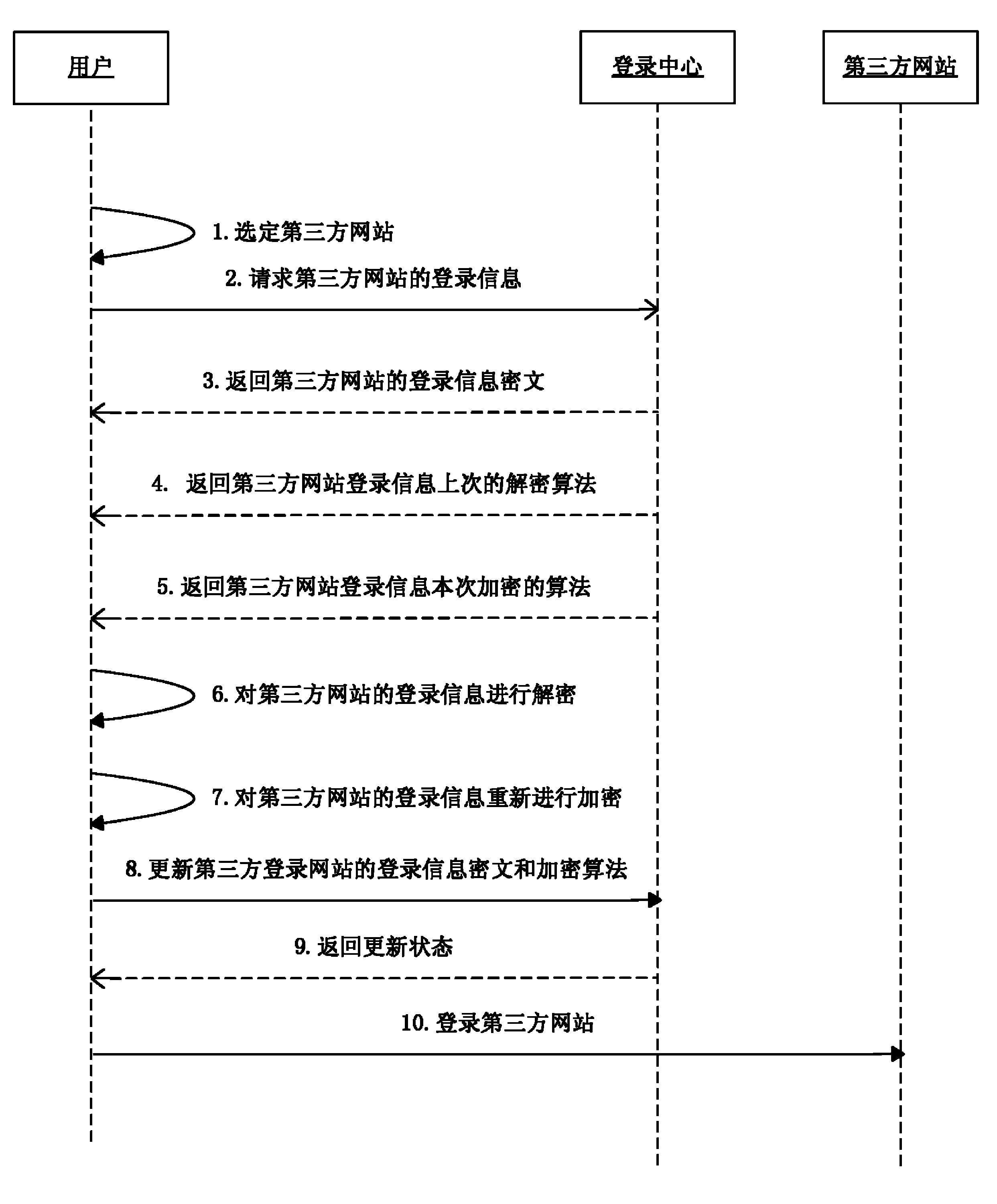
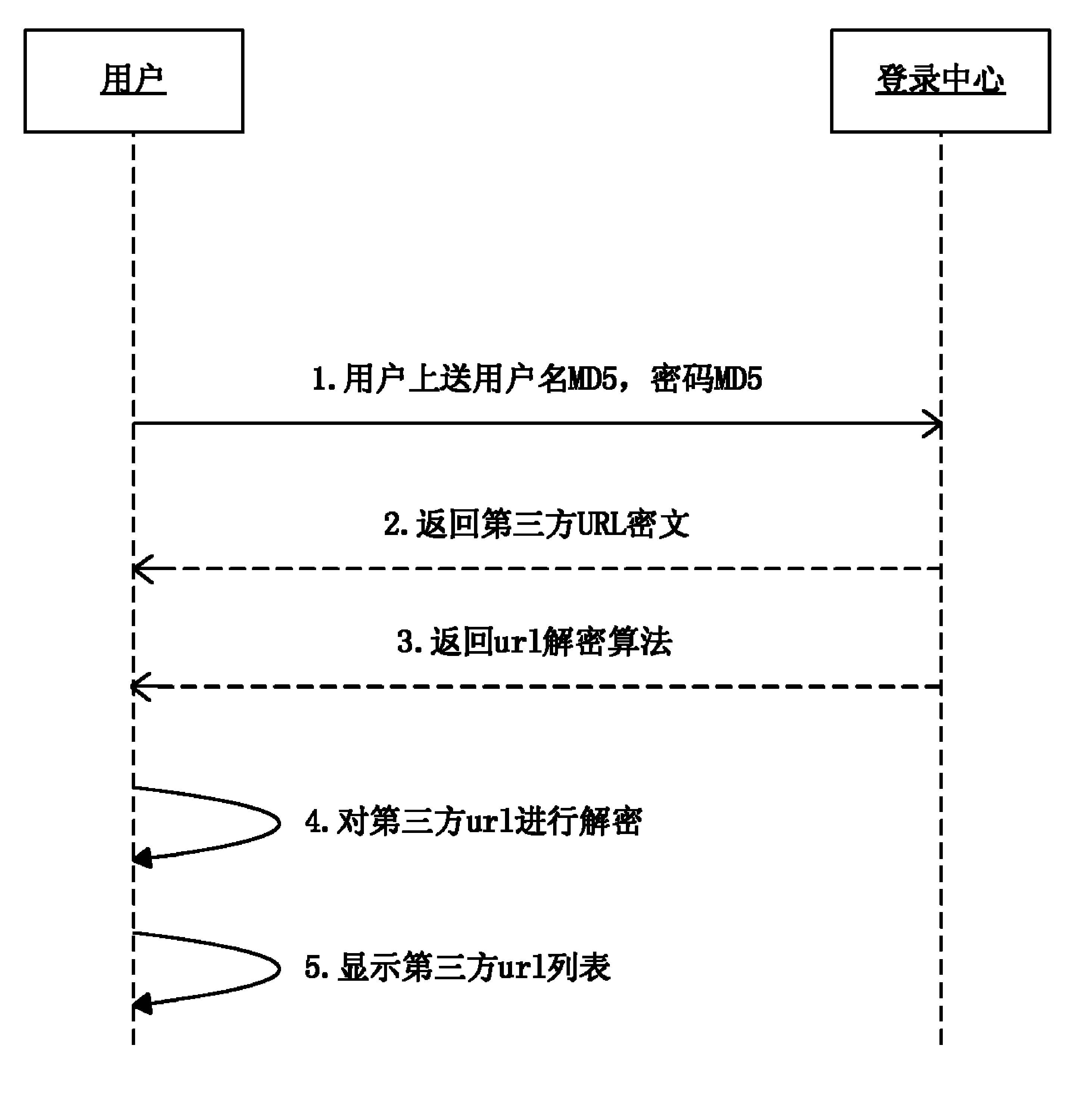
[0091] figure 1 It is a schematic diagram of steps of a third-party login information hosting method according to an embodiment of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com