Safe region recognition method and device, and user terminal
A technology for user terminals and security areas, which is applied in the field of identification equipment, user terminals, and security area identification methods. It can solve the problems of increasing user operation complexity, time limit, and keeping the power on, so as to reduce the chance of password leakage or being deciphered. Prevent and be deciphered, enhance the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
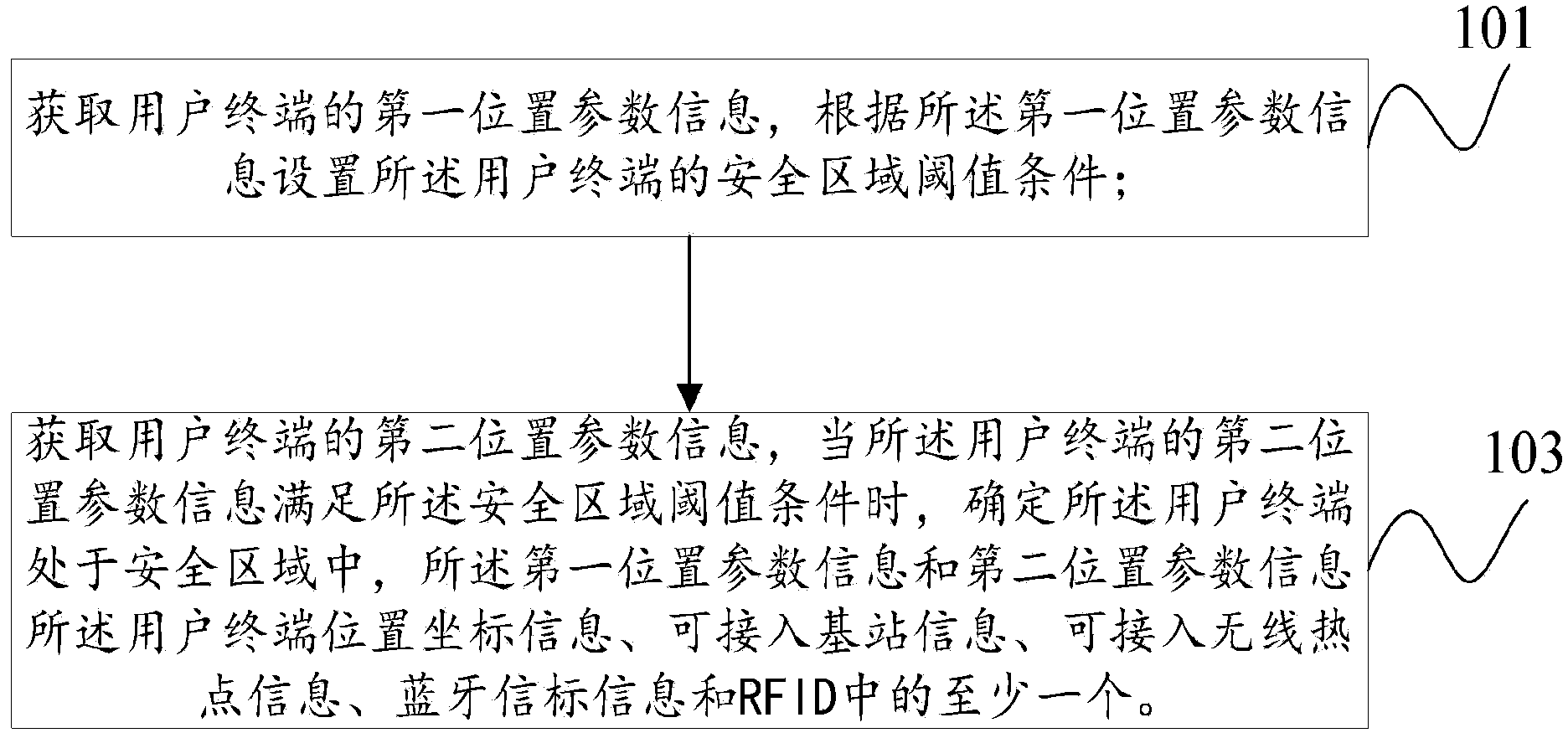
[0047] Such as figure 1 As shown, an embodiment of the present invention provides a security area identification method, wherein the method includes:
[0048] 101. Acquire first location parameter information of the user terminal, and set a security area threshold condition of the user terminal according to the first location parameter information;
[0049] Wherein, the first location parameter information is the location parameter information of the user terminal in the security area. Specifically, when the user terminal needs to set the current area as a security area, the user terminal reports the location parameter information of the current area to the server, and the location of the current area The information is the first location parameter information of the user terminal.
[0050] 103. Acquire second location parameter information of the user terminal, and when the second location parameter information of the user terminal satisfies the safety area threshold conditi...
Embodiment 2
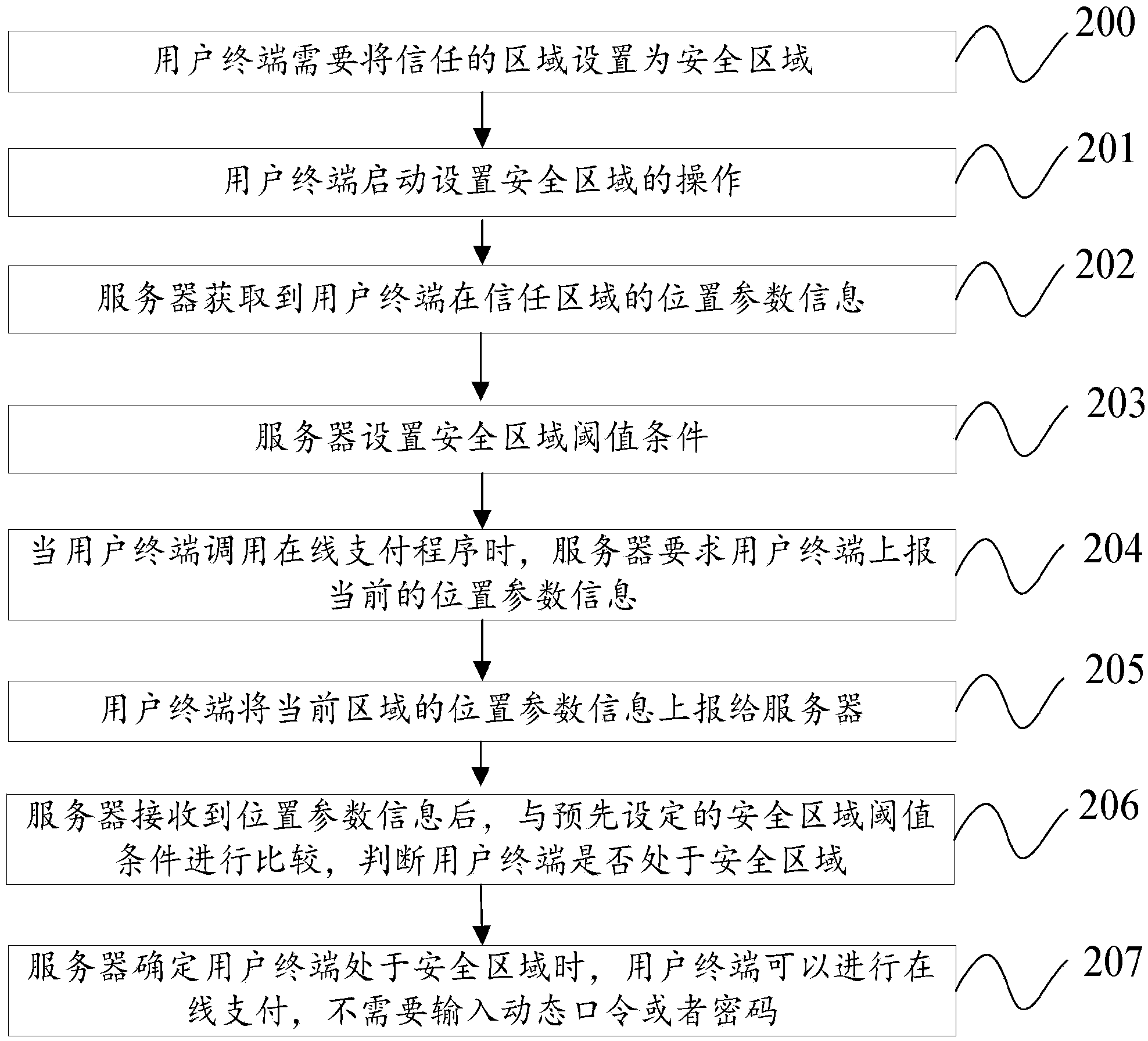
[0088] as attached figure 2 As shown, the embodiment of the present invention also provides a method for identifying a security area. In this embodiment, the mobile application service takes the online payment service as an example, and the location coordinate information of the user terminal is described by taking the GNSS information of the user terminal as an example. The method includes:
[0089] 200. When it is necessary to set the trusted area as a safe area, if it is necessary to set the office, home and other places as a safe area, the user terminal can process online payment business in this safe area, and can pay directly without password or dynamic password.
[0090] 201. The user terminal starts an operation of setting a security area, for example, sends a request message to a server, and starts a program for setting a security area.
[0091] Wherein, in this step, the server or other third-party equipment may also initiate the setting procedure of the security z...
Embodiment 3
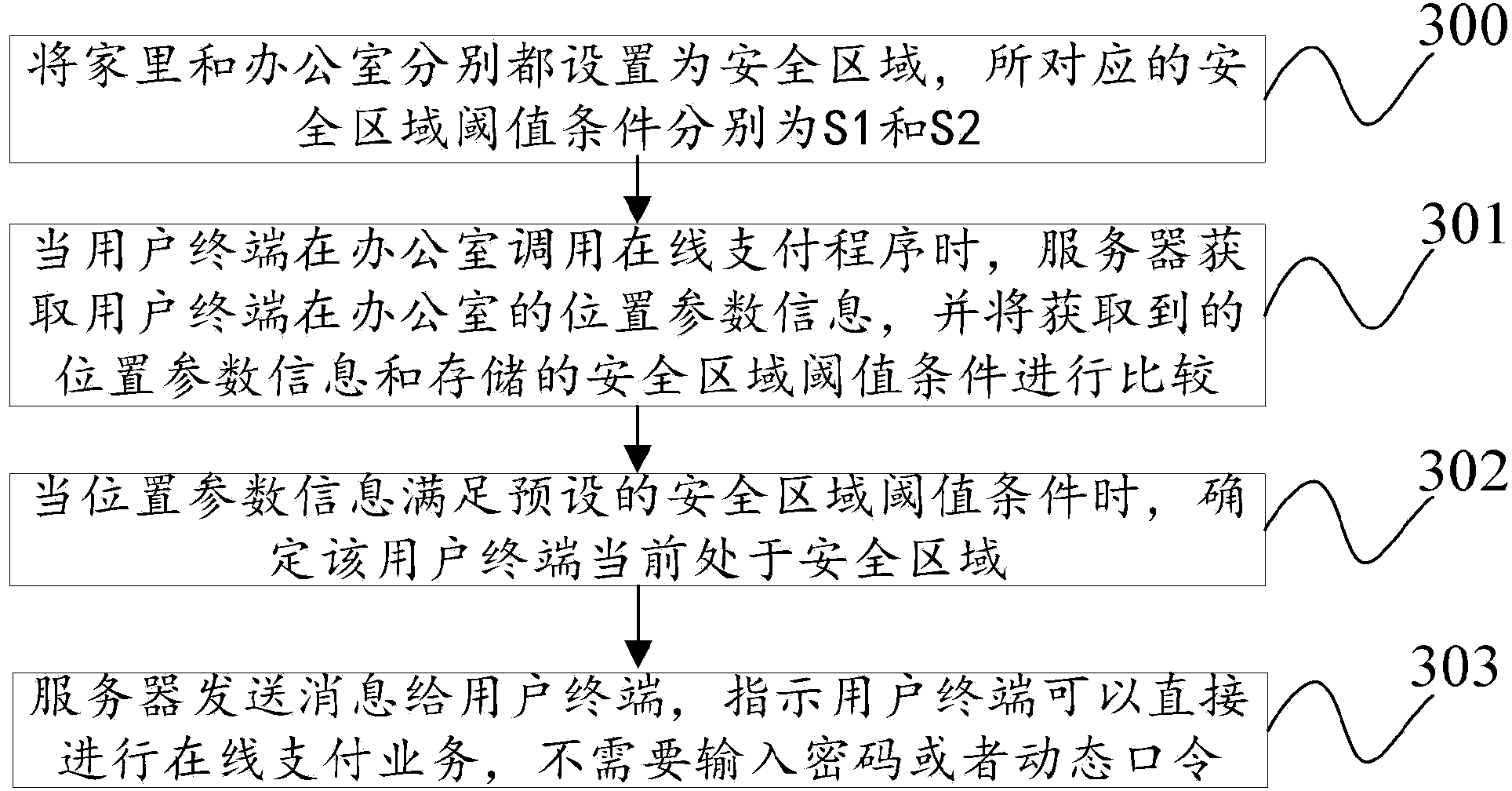
[0101] Refer to attached image 3 , the embodiment of the present invention also provides a safe area identification method. In this embodiment, the mobile application business takes the online payment service as an example, and the location coordinate information of the user terminal is described by taking the GNSS information of the user terminal as an example. The method include:
[0102] 300. Set home and office as safe areas respectively, and the corresponding safe area threshold conditions are S1 and S2 respectively,
[0103] 301. When the user terminal calls the online payment service in the office, the server obtains the location parameter information of the user terminal in the office, and compares the obtained location parameter information with the stored security area threshold condition, specifically:
[0104] 3011. The server finds, according to the obtained location parameter information, that the GNSS information contained in the location parameter information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com