Method for information safety device to achieve multiple applications, and information safety device and system
An information security system and information security technology, applied in the field of information security equipment and systems, can solve the problem that information security equipment cannot support multiple applications, improve portability and hardware compatibility, facilitate development and writing and function expansion, improve The effect of development efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] This embodiment provides a method for an information security device to implement multiple applications. In this embodiment, the terminal may be a personal computer PC, etc., and the information security device may be a smart key device (such as a USB key, an audio key, etc.). By adopting the method provided by the embodiment of the present invention, the information security device can not only realize the signature function, but also realize many different applications.
[0026] figure 1 A flow chart of the method for implementing multiple applications for the information security device provided in Embodiment 1 of the present invention, as shown in figure 1 shown, including the following steps:
[0027] In step 101, the terminal compiles and transforms the written application program to obtain an intermediate code file of the application program.
[0028] Wherein, the application program may be written in a high-level language, such as BASIC language, True BASIC la...
Embodiment 2
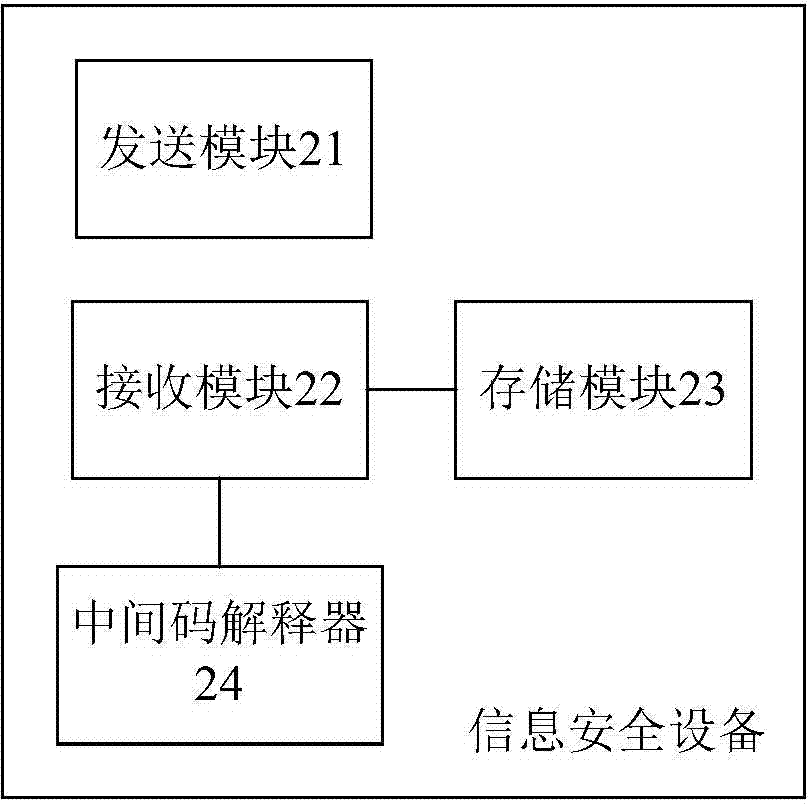
[0055] This embodiment provides an information security device implementing multiple applications, which can be used to implement the operations performed by the information security device in the method described in Embodiment 1. like figure 2 As shown, the information security equipment includes:
[0056] Sending module 21, is used for sending application program download request to terminal;
[0057] The receiving module 22 is configured to receive the intermediate code files of at least two application programs sent by the terminal for download, and the intermediate code files of the application programs are obtained by the terminal after compiling, transforming and safety checking the written application programs;
[0058] The storage module 23 is connected to the receiving module 22, and is used to save the intermediate code files of at least two application programs received by the receiving module 22;
[0059] The receiving module 22 is also configured to receive th...
Embodiment 3
[0067] This embodiment provides an information security system for implementing multiple applications, which can be used to implement the method for implementing multiple applications by an information security device described in Embodiment 1. like image 3 As shown, the system includes: an information security device 20 and a terminal 30, and the information security device 20 may be the information security device as described in Embodiment 2.
[0068] The terminal 30 is used for compiling and transforming the written application program to obtain the intermediate code file of the application program; performing security verification on the intermediate code file; and saving the intermediate code file passing the security verification; An application program download request; obtaining intermediate code files of at least two application programs requested to be downloaded according to the download request; and sending the intermediate code files of at least two application ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com