Terminal and method for preventing sensitive information leakage
A sensitive information and anti-leakage technology, which is applied in the electronic field, can solve the problems of insufficient sensitive information leakage methods, and achieve the effects of reducing the risk of being leaked, improving terminal performance, and reducing load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be further described in detail below through specific embodiments in conjunction with the accompanying drawings.
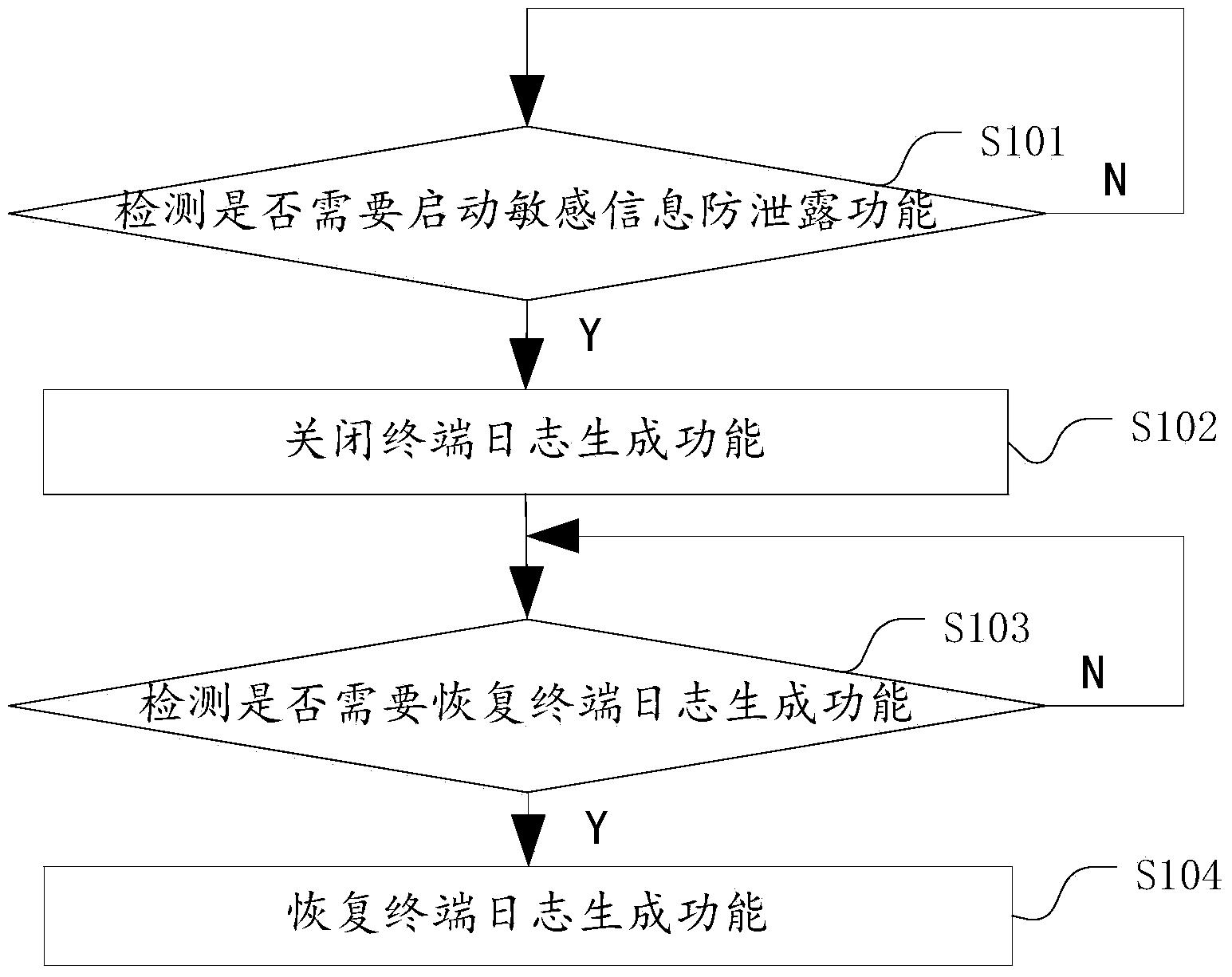
[0033] figure 1 For the flow chart of the method for preventing the leakage of sensitive information provided by an embodiment of the present invention, please refer to figure 1 , including the following processes:
[0034] S101. Detect whether it is necessary to activate the anti-leakage function of sensitive information. If so, proceed to step S102. If not, continue to detect.
[0035] Methods for detecting whether the sensitive information leakage prevention function needs to be activated include but are not limited to methods 1 to 3 listed below:
[0036] Method 1: Detect whether there is a sensitive application program currently running, and if so, the detection result indicates that the sensitive information leakage prevention function needs to be activated.
[0037] Sensitive applications include but are not limited to o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com