A method of computer protection
A computer and program technology, applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve problems such as trouble, leakage of computer login password, illegal login computer password input, etc., and achieve the effect of portability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0013] Hereinafter, embodiments of the present invention will be described with reference to the drawings.
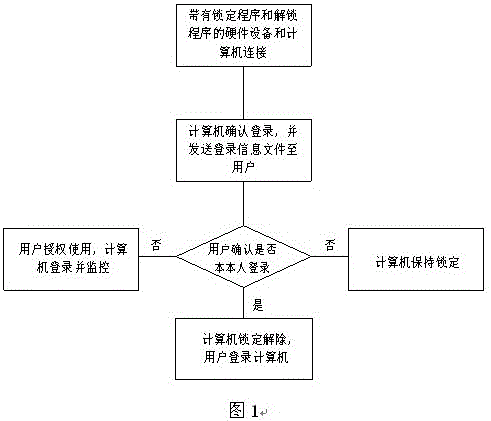
[0014] Such as figure 1 As shown, the method to unlock the computer, the specific steps are as follows:
[0015] In the first step, when connecting the hardware device storing the locking program and decryption program to the computer, first determine whether the locking program is installed in the computer, if the locking program has been installed in the computer, directly perform the second step; program, execute the locking program in the hardware device.
[0016] The second step is to judge whether the computer is locked. If the computer is not locked, it is not necessary to unlock the computer; if the computer is locked, a login information file is generated. The login information file can be sent to Users' handheld mobile terminals, including mobile phones, tablets, smart watches, etc.
[0017] In the third step, the user confirms whether the user is logging i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com