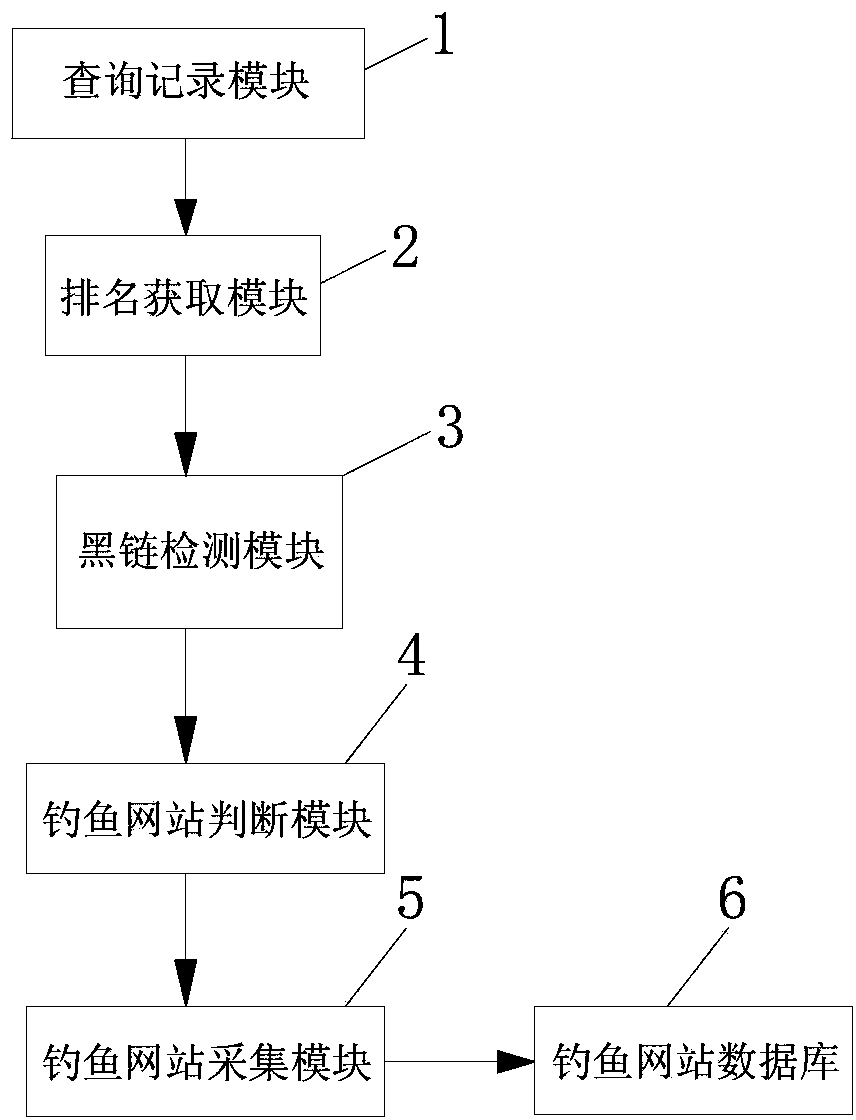
Precise collection method and system based on phishing website spread
A technology for phishing websites and collection systems, applied in transmission systems, electrical components, etc., can solve problems such as failure to prevent and reduce the detection rate of phishing websites, and achieve the effect of narrowing the scope and improving network security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
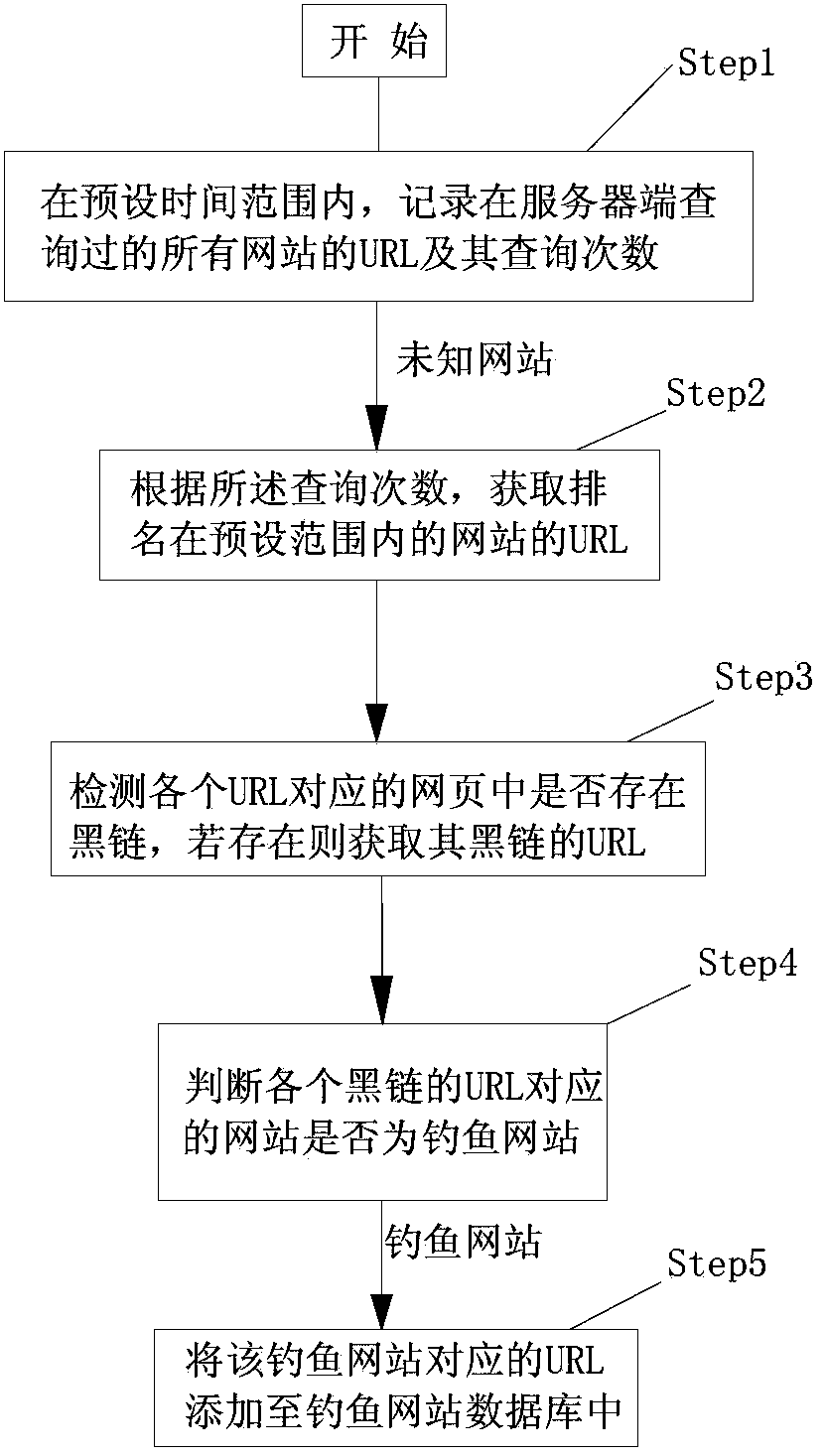
[0033] Such as figure 1 As shown, the present embodiment discloses a precise collection method based on phishing website propagation, comprising the following steps:
[0034] Step1: Within the preset time range, record the URLs of all websites queried on the server side and the number of queries; the server described in this step refers to the existing server used to query whether the website currently visited by the user is a phishing website. This step The purpose of this is to record the activity of URLs queried by the server for a period of time; the specific preset time can be set to different times according to the actual processing capacity of the server, that is, websites with high activity are collected within a certain reasonable time range. The present embodiment selects 24 hours;
[0035] Step2: According to the number of queries, obtain the URLs of websites with rankings within the preset range; the purpose of this step is to find highly active URLs, which are al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com