A Second-Order Side-Channel Energy Analysis Method for Simple Masked SM4 Algorithm
A technology of energy analysis and side channel, which is applied in the field of cryptographic algorithm analysis and detection, can solve problems such as second-order energy analysis without systematic analysis methods, and achieve a highly practical effect
Active Publication Date: 2017-01-04
国家密码管理局商用密码检测中心
View PDF5 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
However, there is no systematic analysis method for the second-order energy analysis of masks
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
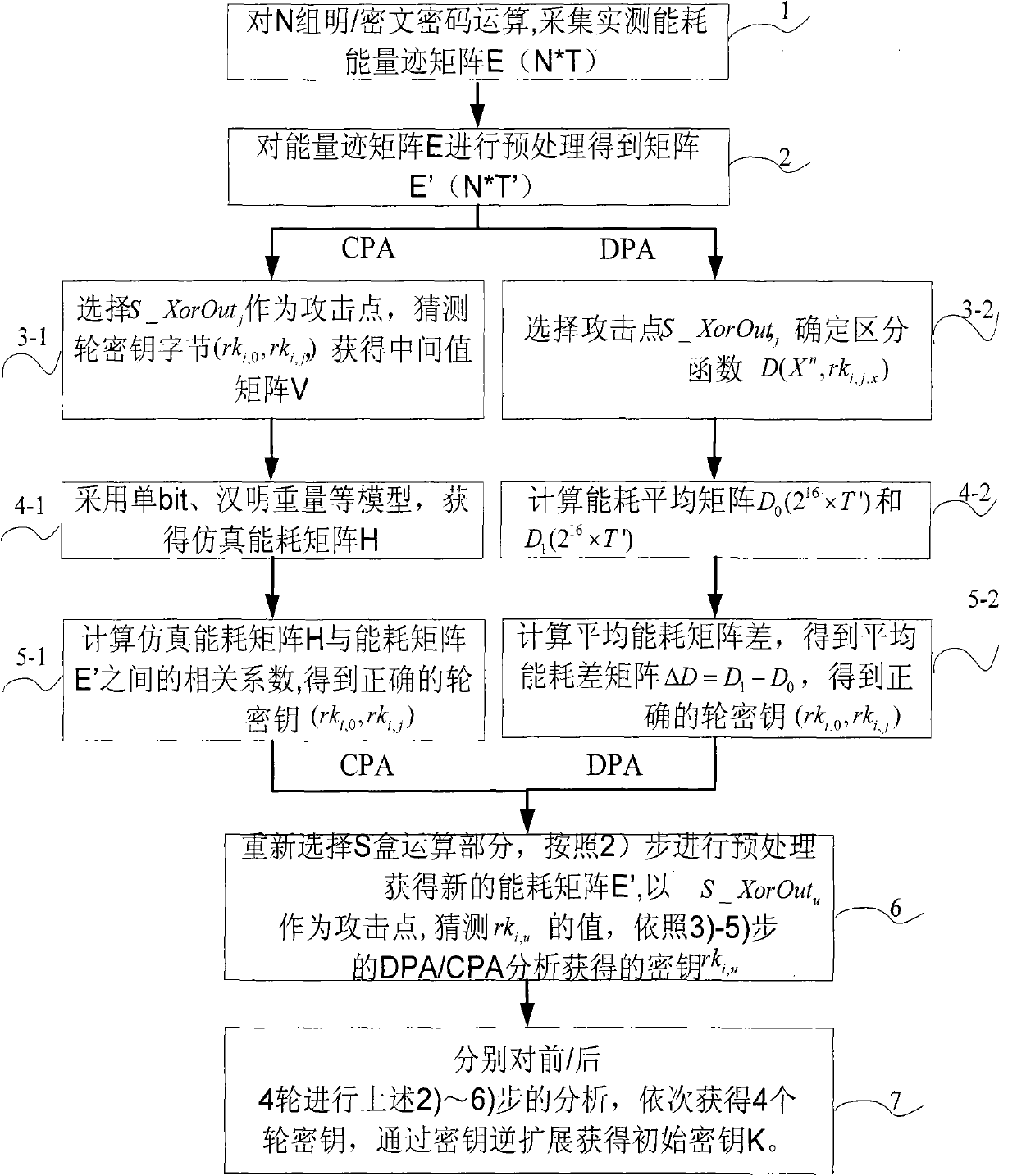
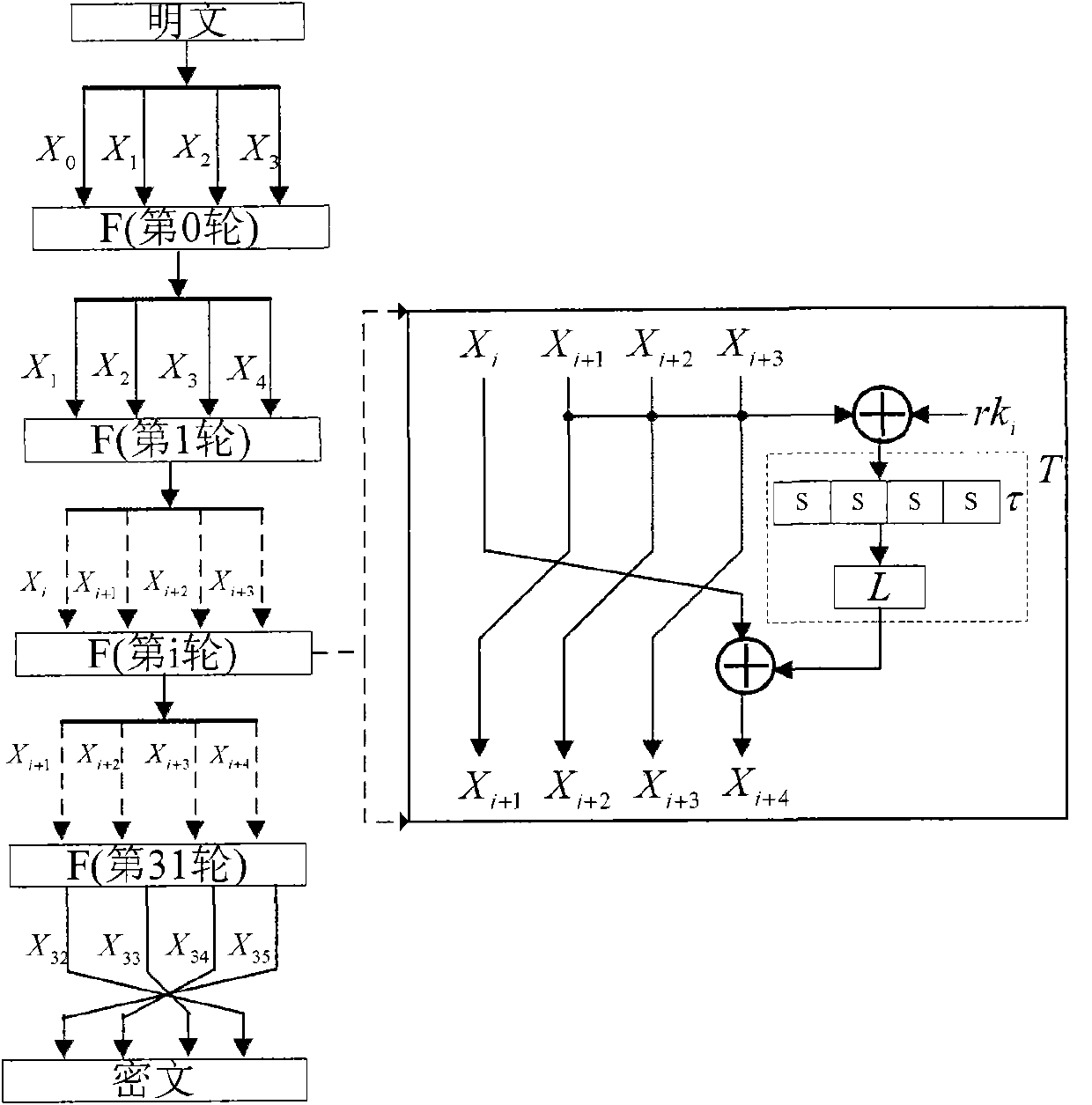
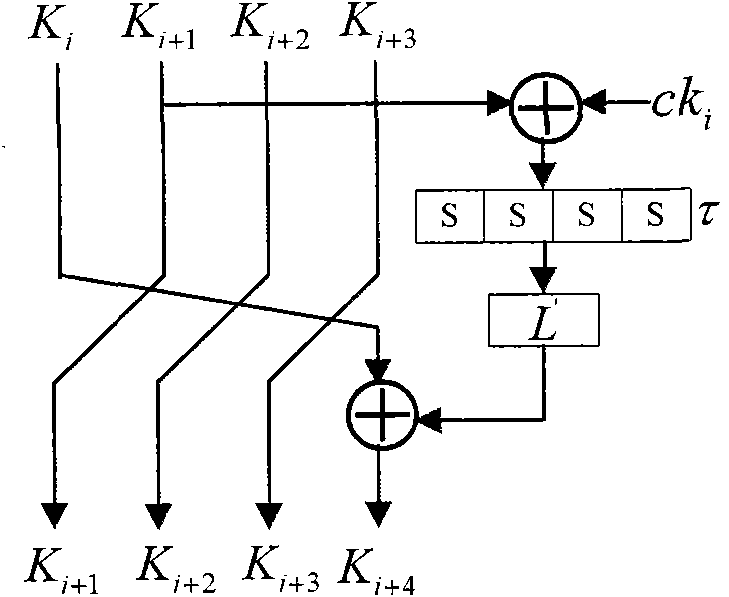
The invention discloses a second-order side channel energy analysis method for an SM4 algorithm of a simple mask. To achieve mask protection for the SM4 algorithm with the output of four S boxes carrying the same mask value, the method comprises the steps of (1) acquiring energy traces and establishing a sampling energy consumption matrix; (2) preprocessing the energy consumption matrix in the previous step; (3) selecting attack points to conduct CPA or DPA to obtain rki, 0; (4) re-selecting an S-box operation part and following the steps (2) and (3) to obtain rki, u through analysis; and (5) carrying out the steps (2), (3) and (4) on previous / next four rounds to obtain a round key and obtaining an initial key through a key inverse expansion operation. The technical scheme of the invention innovatively provides the new second-order energy analysis method, develops a new situation of SM4 cryptographic algorithm attack, extends the side channel power analysis method for the SM4 algorithm, and can fully and effectively conducts side channel energy analysis on the SM4 cryptographic algorithm; and the method of the technical scheme is highly practical for common mask protection measures.
Description
A Second-Order Side-Channel Energy Analysis Method for Simple Masked SM4 Algorithm technical field The invention belongs to the technical field of cryptographic algorithm analysis and detection, and specifically aims at realizing the second-order side channel energy analysis for the SM4 cryptographic algorithm with mask protection measures, and in particular relates to the secondary SM4 cryptographic algorithm with the same input and output intermediate mask of the S box. The first-order side channel energy analysis method. Background technique With the development of information technology, various cryptographic algorithms are being widely used in economic, military, administrative and other important departments to protect the security of information. In view of the importance of cryptographic algorithms, the analysis and research of cryptographic algorithm software and hardware implementation (cryptographic modules) is of great significance to protect information securi...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/06
Inventor 罗鹏李大为曹伟琼
Owner 国家密码管理局商用密码检测中心
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com