Method and device for classifying malicious software
A malicious software and classification method technology, applied in computer security devices, special data processing applications, instruments, etc., can solve the problem of low accuracy and achieve the effect of improving accuracy and classification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
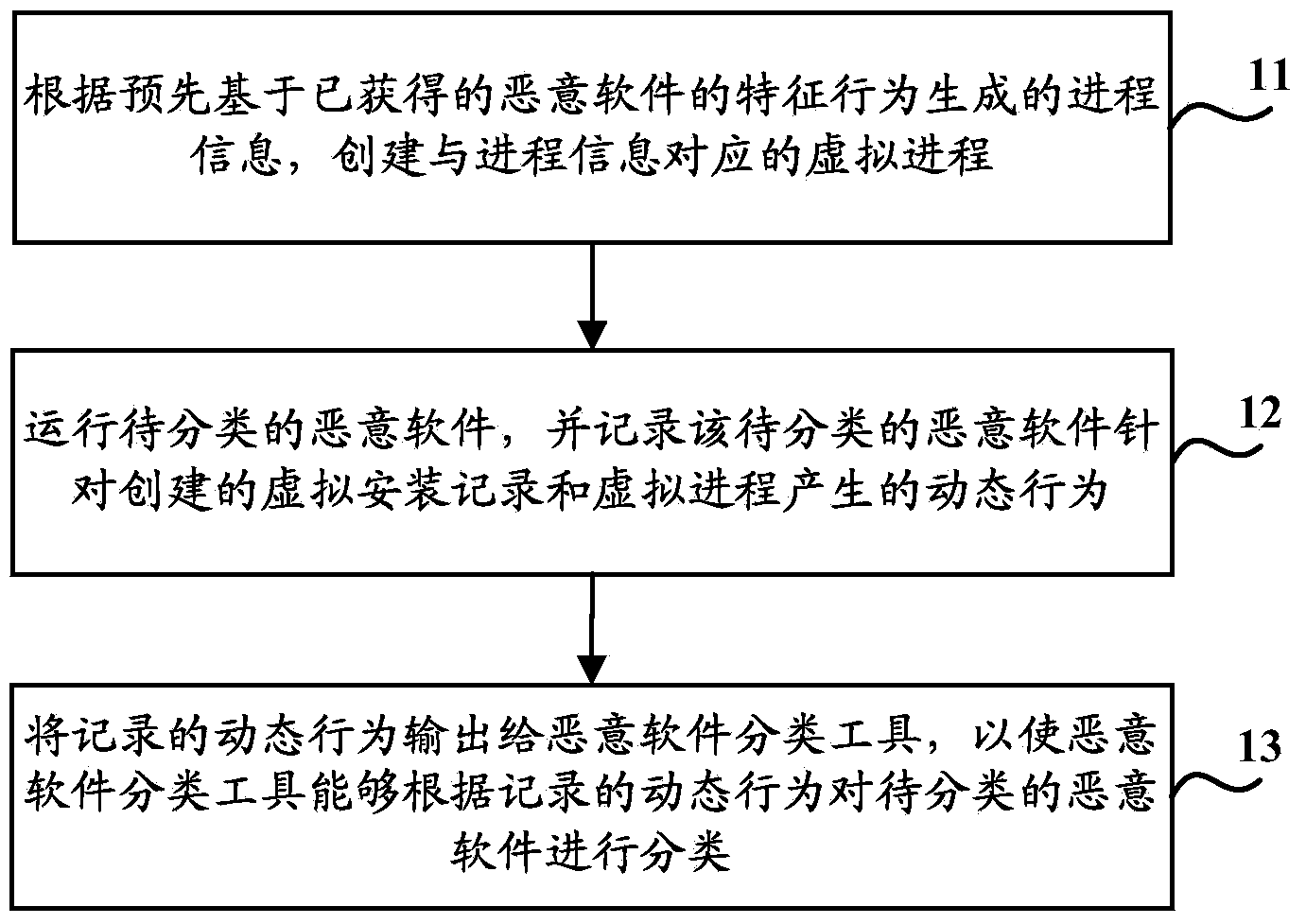
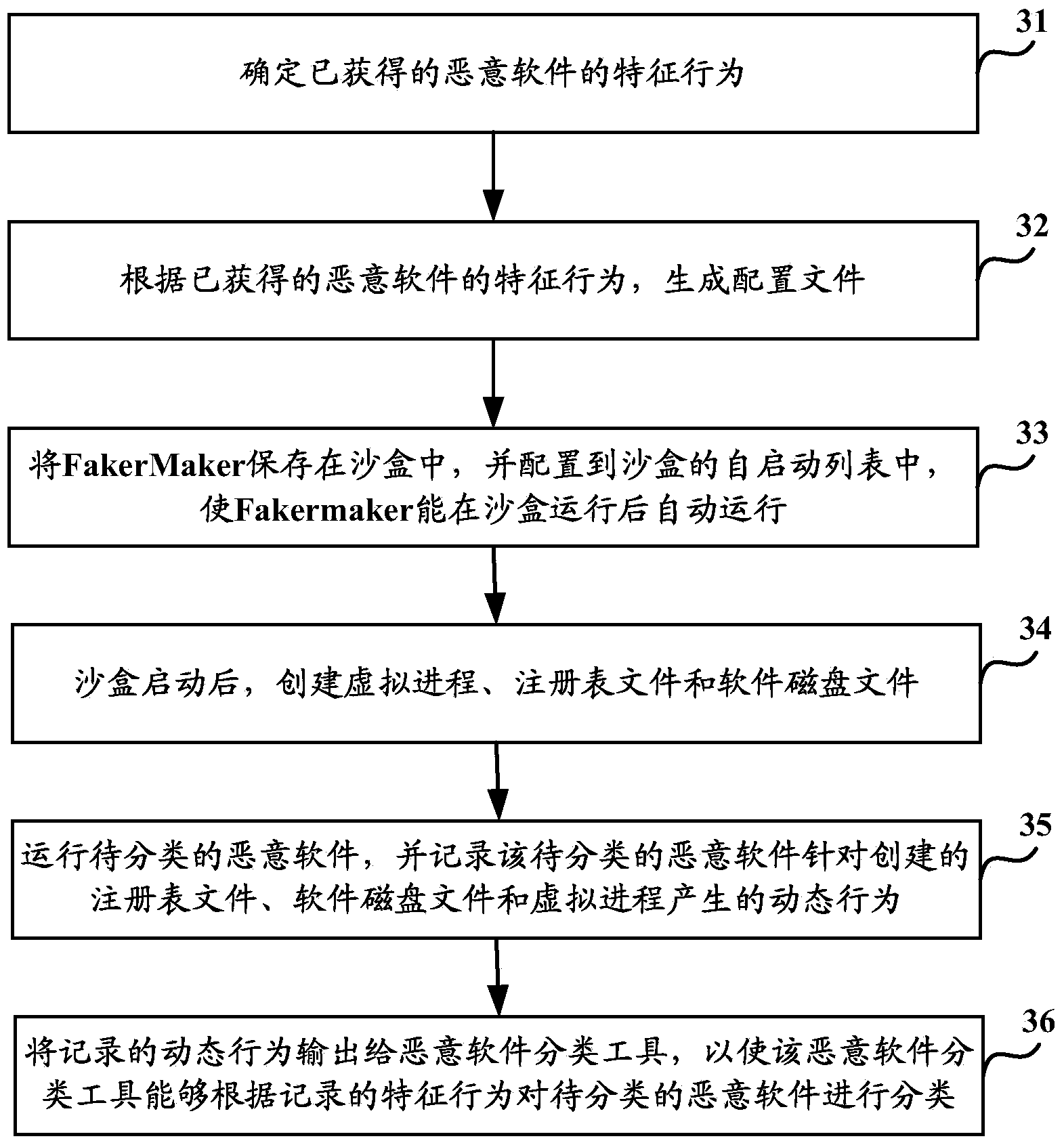
[0065] like image 3 As shown, the specific flow chart of the implementation of the malicious software classification method provided by the embodiment of the present invention mainly includes the following steps:
[0066] Step 31, determining the characteristic behavior of the obtained malicious software;
[0067] Among them, the characteristic behaviors of the acquired malware can include:
[0068] When it is detected that the specified registry file exists, the behavior of stopping the operation;
[0069] When it is detected that the specified registry file exists, the behavior of deleting the specified registry file;
[0070] When it is detected that the specified software disk file exists, the behavior of stopping the operation;
[0071] When it is detected that the specified software disk file exists, the act of deleting the specified software disk file;
[0072] When the specified process is detected, the behavior of stopping the operation;
[0073] When it is dete...
Embodiment 2
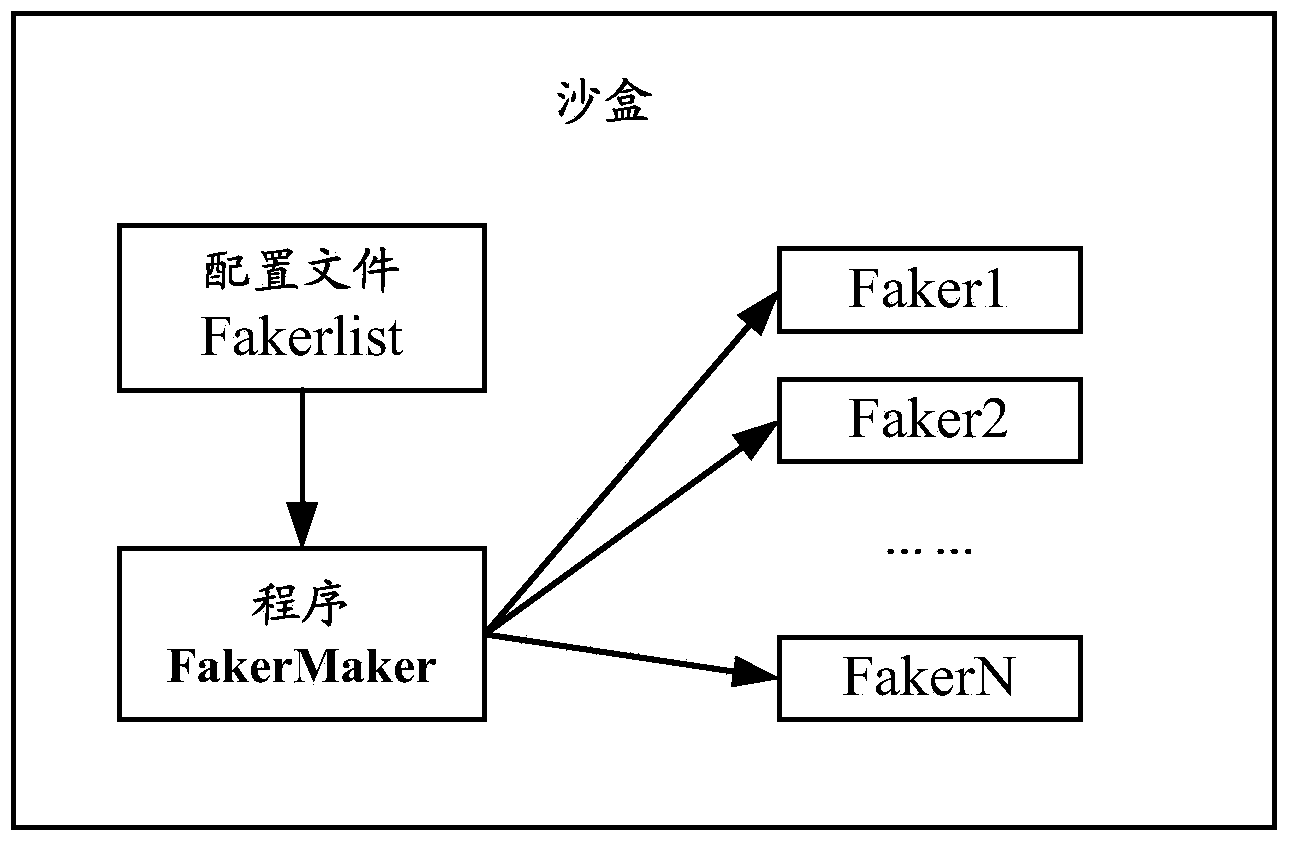
[0086] like Figure 4 As shown, the specific flow chart of the implementation of the malicious software classification method provided by the embodiment of the present invention mainly includes the following steps:
[0087] Step 41, determining the characteristic behavior of the obtained malicious software;
[0088] Among them, the characteristic behaviors of the acquired malware may include:
[0089] When it is detected that the specified registry file exists, the behavior of stopping the operation;
[0090] When it is detected that the specified registry file exists, the behavior of deleting the specified registry file;
[0091] When it is detected that the specified software disk file exists, the behavior of stopping the operation;
[0092] When it is detected that the specified software disk file exists, the act of deleting the specified software disk file;
[0093] When the specified process is detected, the behavior of stopping the operation;
[0094] When it is det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com