A Chinese event information mining method and system
An event information and event technology, which is applied in the fields of instruments, computing, and electrical and digital data processing, etc., can solve the problems of time-consuming and laborious, high event mining cost, and time and energy consumption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0137] Embodiment 1 of the present invention discloses a Chinese event information mining method, please refer to figure 1 , the method includes:
[0138] S1: Analyze and process the sentences in each document of the original text to obtain a set of candidate templates of the original text, the set of candidate templates includes at least one candidate template, and the candidate templates include candidate event anchors of the sentences, A four-tuple consisting of the entity of the sentence, the syntactic path of the candidate event anchoring to the entity, and the dependency path of the candidate event anchoring to the entity.
[0139] It should be noted that the original text in this embodiment refers to the text for which event information needs to be mined, which is a collection of text documents without any tag information.
[0140] Among them, see figure 2 , step S1 specifically includes:
[0141] S11: Perform word segmentation, entity recognition, syntax analysis, ...
example 1
[0143] Example 1: Hezbollah attacked Israel's Qiba Farm with missiles and injured 3 Israeli soldiers.
[0144] Afterwards, an entity recognition tool is called to identify entities from each sentence in the word segmentation sentence set, and mark the recognized entities to obtain a set of entity-tagged sentences. The format of each entity annotation in the entity annotation sentence set is "entity / entity type". For example, the above example 1 is specifically as shown in example 2 after entity annotation:
example 2
[0145] Example 2: Hezbollah / ORG attacked Israel / GPE Chiba Farm / LOC with missiles / WEA and wounded 3 / NUM Israeli / GPE soldiers / PER.
[0146] Among them, the entity types represented by "ORG", "WEA", "GPE", "LOC", "NUM" and "PER" are organization, weaponry, political entity, location, quantity and person respectively. In addition, commonly used entity types include "TIME", "JOB", "FAC" and "VEH", which represent time, job position, place and means of transportation respectively.
[0147] Then, the syntactic analysis tool is used to perform syntactic analysis on each sentence in the entity-labeled sentence set to obtain the syntax tree of each sentence, and the syntax trees corresponding to each entity-labeled sentence in the original text form a syntax tree set.
[0148] Syntactic analysis specifically refers to the analysis of the grammatical function of words in a sentence.
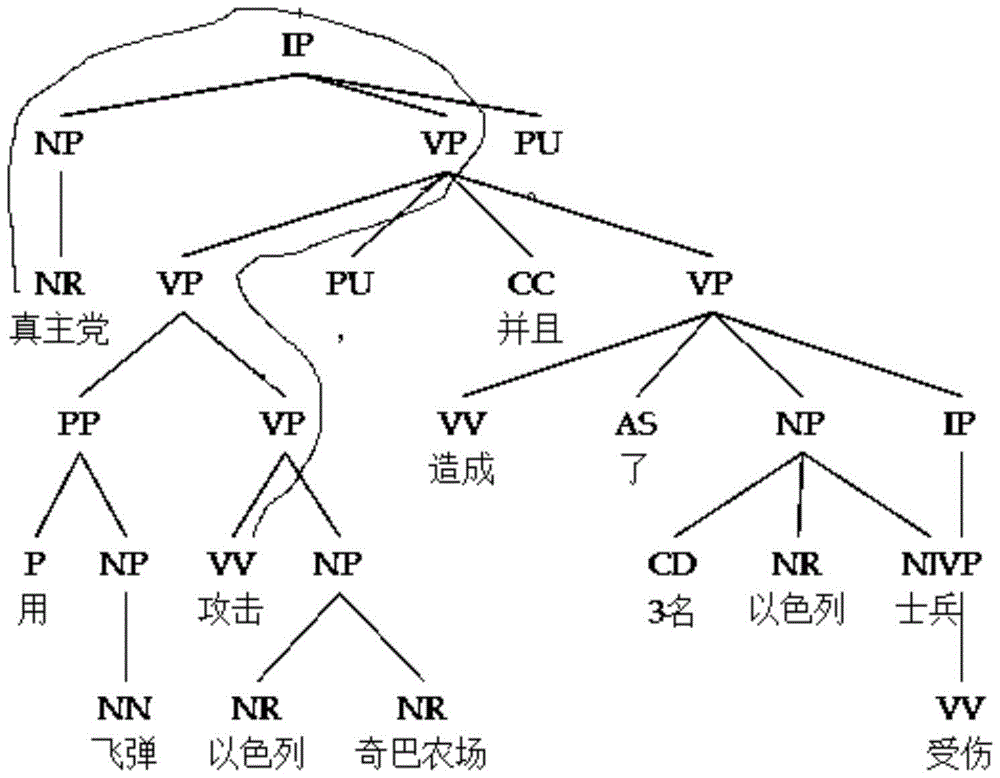
[0149] After using the syntax analysis tool to analyze the syntax of the above example 2, as shown in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com