Object property security on-line verifying method and device
A technology of object attributes and verification methods, applied in the field of information security, can solve the problems of increased business promotion cost and difficulty, and achieve the effect of reliable online verification and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Unless specifically stated otherwise, as will also be appreciated from the following discussion, throughout this specification, discussion using terms such as "filter," "screen," "determine" means using a computer or similar The action or process of a specific device, such as an electronic computing device. In the context of this specification, a computer or similar electronic computing device is capable of manipulating or transforming signals. These signals are typically represented as physical electronic or magnetic quantities in memory, registers, or other information storage, transmission, or display devices of a computer or similar electronic computing device. For example, an electronic computing device may include one or more processors that perform one or more specific functions.
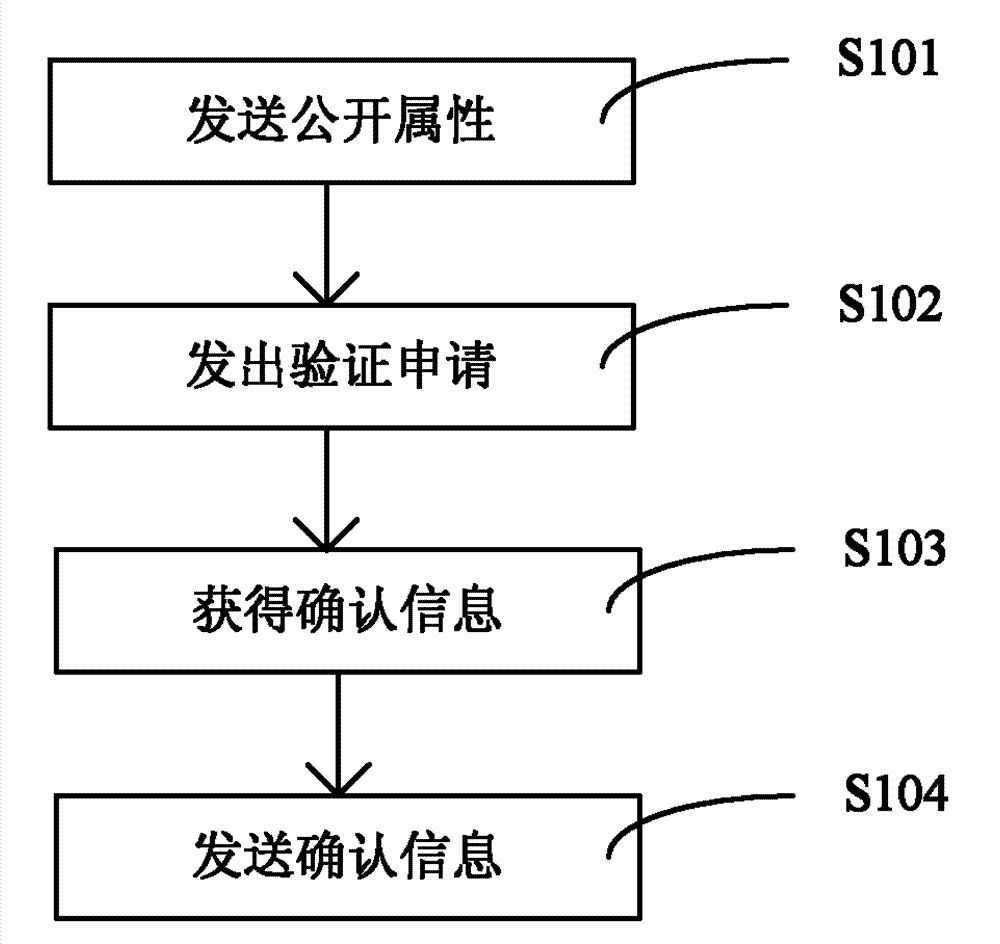
[0023] Such as figure 1 As shown, the first step of the online verification method for object attribute security is to send the public attribute of the object to the object attribute...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com