Implementing a common bootstrap architecture type security association for terminals in a mobile telecommunications network
A security association, telecommunication network technology, applied in the telecommunication field of telecommunication, mobile network
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
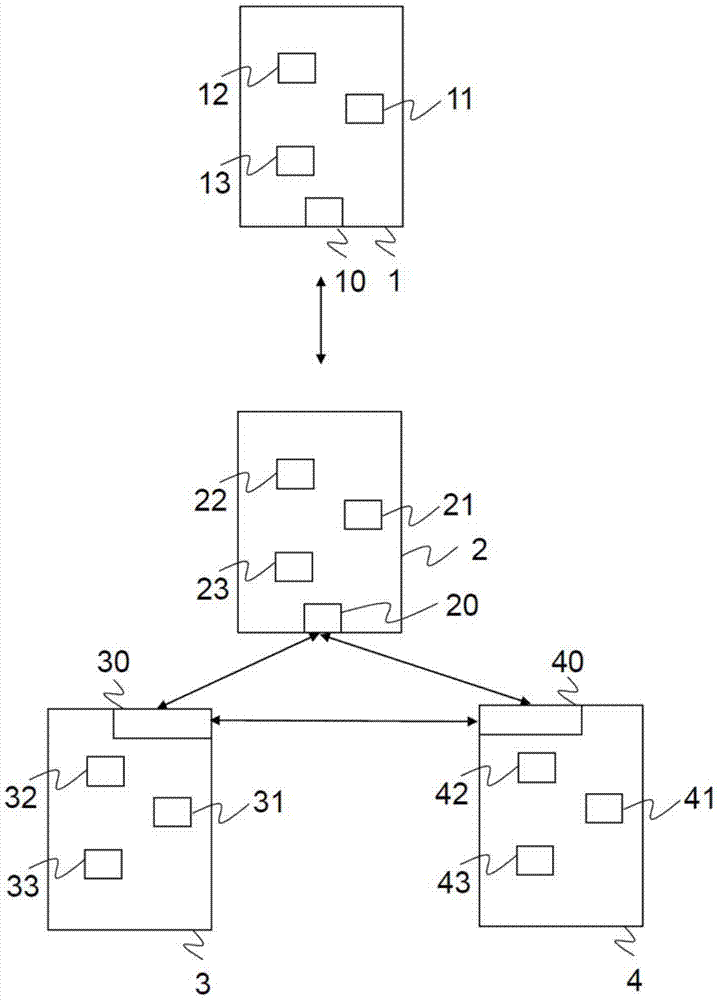
[0045] according to figure 1 An embodiment of the invention is shown, the items of equipment implementing the invention are a mobile terminal 1, a network access server 2, a boot function server 3 called BSF server and a subscriber server called HSS (Home Subscriber Server) 4.
[0046] The invention is implemented for GPRS (General Packet Radio Service) type access. In this case, the network access server 2 is a Serving GPRS Support Node, called SGSN (Serving GPRS Support Node).
[0047] In another embodiment, the invention is implemented in an LTE / EPC (Long Term Evolution / Evolved Packet Core) type network. In this case, the network access server 2 is a server called MIME (Mobility Management Entity).
[0048] The mobile terminal 1 may be, for example, a mobile phone terminal, a laptop computer, a digital personal assistant, or the like. In the example shown, the mobile terminal 1 is a mobile telephone terminal belonging to a user.
[0049] Such as figure 1 As shown, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com