Network user structure disturbance method based on spectral constraint and sensitive area partition
A network user and disturbance method technology, applied in the field of Internet information security, can solve problems such as poor network availability and insufficient privacy protection, and achieve the effects of improving availability, eliminating invalid disturbances, and maintaining structural characteristics.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The present invention is further described below in conjunction with specific embodiment, but protection scope of the present invention is not limited thereto:
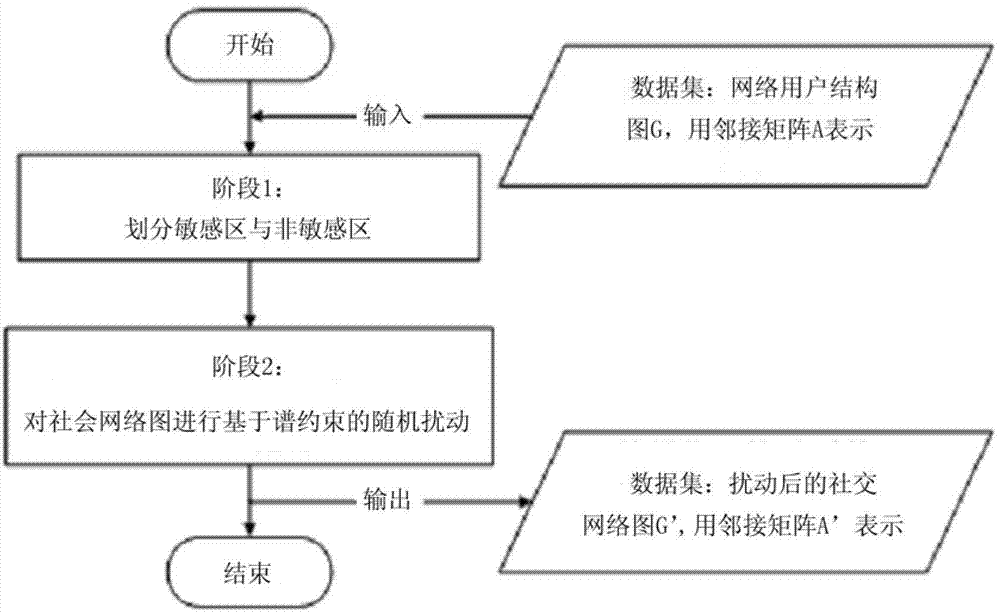
[0020] Such as figure 1 As shown, a network user structure perturbation method based on spectral constraints and sensitive area division includes the following steps:
[0021] 1. A network user structure perturbation method based on spectral constraints and sensitive area division, comprising the following steps:
[0022] 1) Input the network user structure graph G and represent it with the adjacency matrix A, and find the Laplacian matrix L=D-A corresponding to A, where D is the degree sequence of graph G;
[0023] 2) Find the largest eigenvalue of the adjacency matrix A and its corresponding eigenvector λ 1 , e 1 ={x 1 ,x 2 ,...,x n} T ;
[0024] 3) Find the second smallest eigenvalue of the Laplacian matrix L and its corresponding eigenvector μ 2 ,q 2 ={y 1 ,y 2 ,...,y n} T ;
[0025] 4) Divid...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com