Method and system for determining risk value of security incident
A value-at-risk and event technology, applied in the computer field, can solve the problem of not determining the risk value of security incidents, no one determining the risk value of security incidents, etc., to achieve the effect of improving basic security and reducing losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
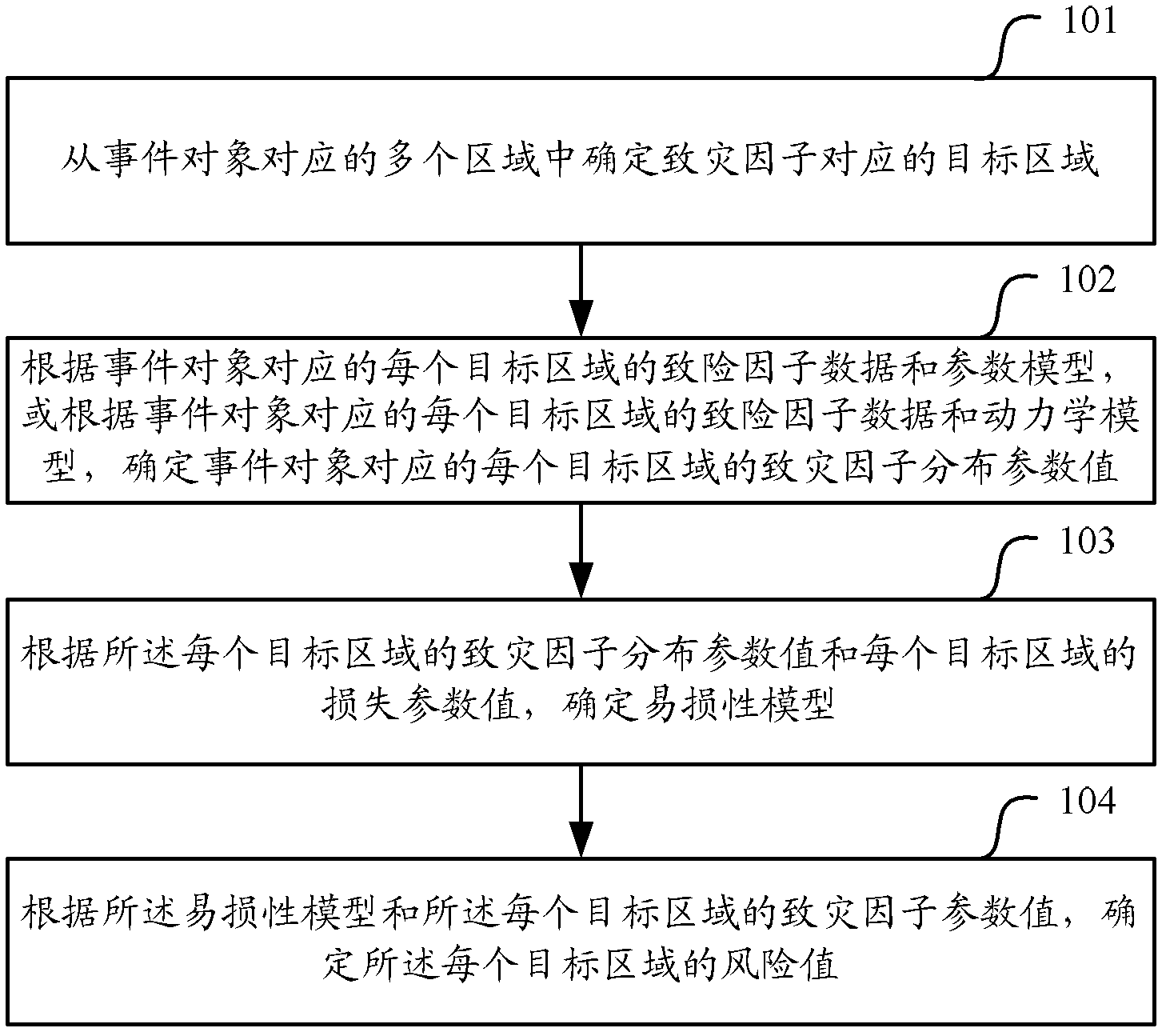
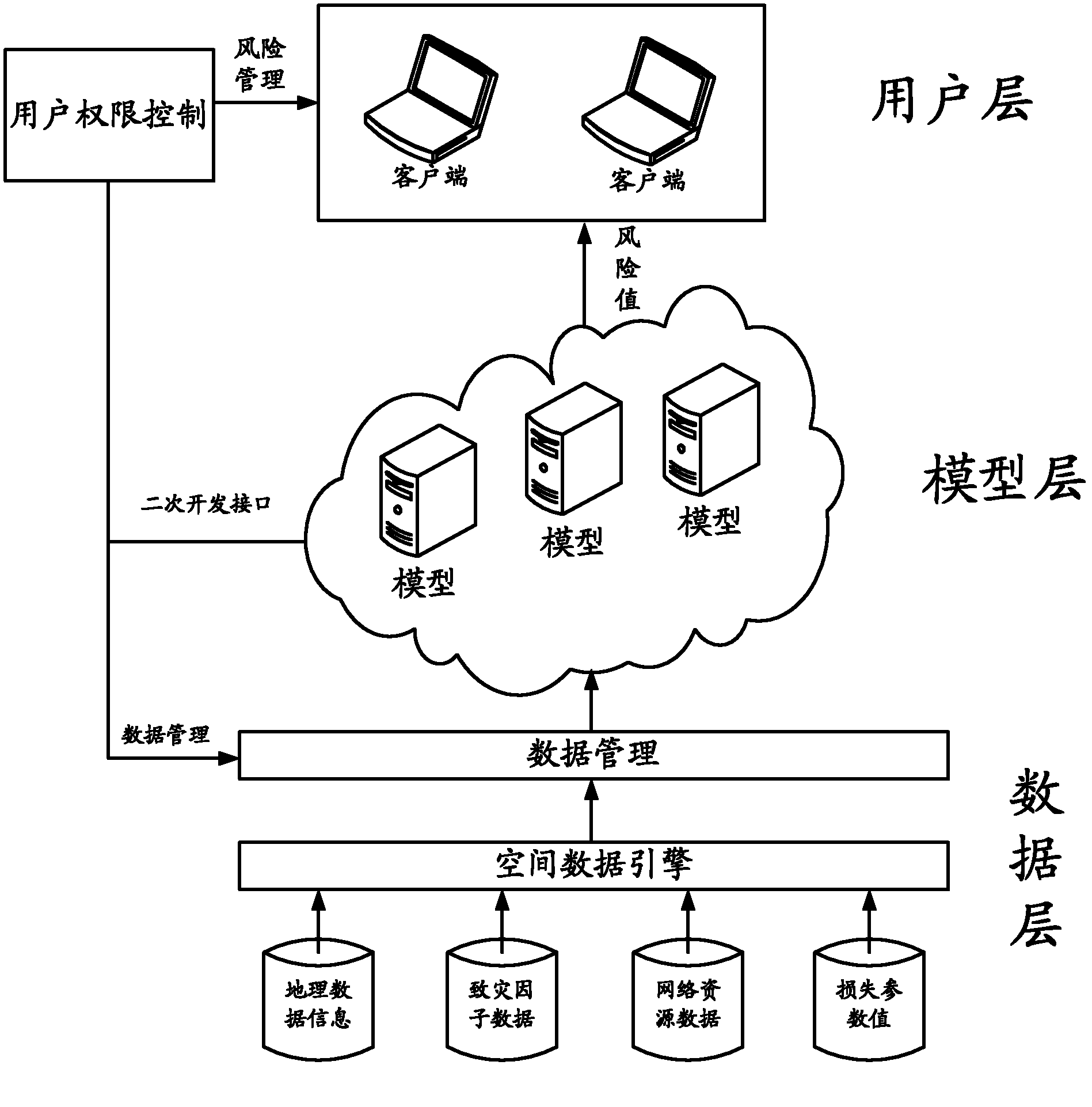
[0021] According to the hazard factor data and parameter model of each target area corresponding to the event object, or according to the hazard factor data and dynamic model of each target area corresponding to the event object, the embodiment of the present invention determines each target corresponding to the event object The risk factor distribution parameter value of the area, and then according to the risk factor distribution parameter value of each target area and the loss parameter value of each target area, the vulnerability model is determined, and finally according to the vulnerability model and each target area Hazard parameter value, which determines the risk value for each target area. Because the risk value of security incidents can be determined, the broadband network resources can be controlled to improve the basic guarantee, so that personnel can formulate corresponding preventive measures and construction methods according to the risk distribution, and minimi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com