Port scanning method
A technology of port scanning and waiting to be scanned, applied in the field of port scanning, can solve problems such as prolonging scanning time, taking a long time, disturbing judgment, etc., and achieve the effect of improving concealment, avoiding detection, and improving scanning efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
[0021] see figure 1 , the first embodiment of the present invention provides a port scanning method, which can avoid being detected by an intrusion detection system, and the port scanning method includes the following steps:
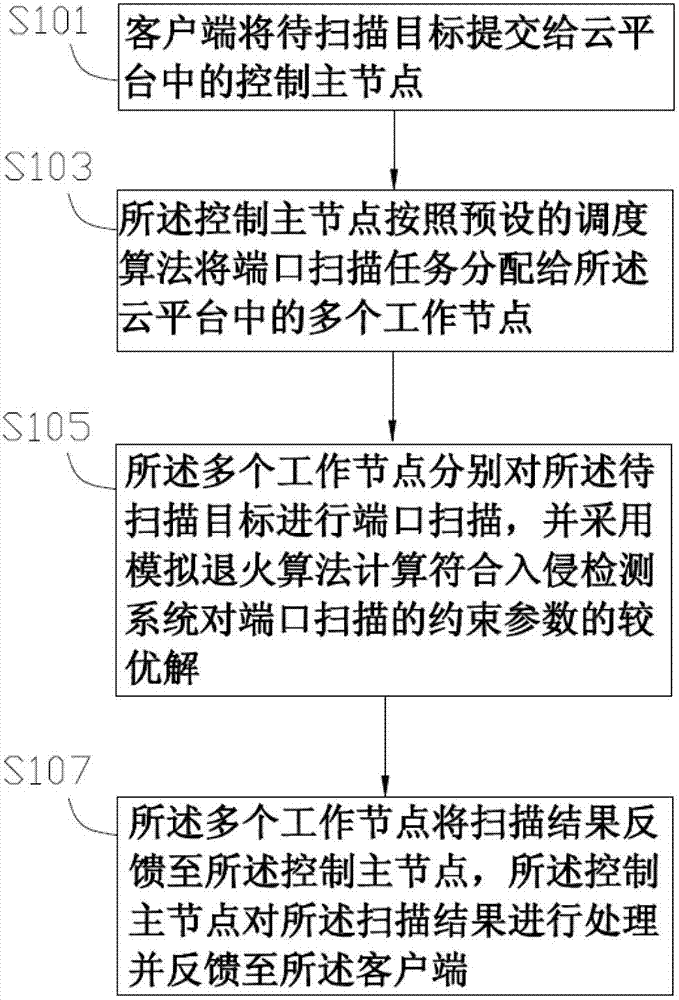
[0022] Step S101, the client submits the object to be scanned to the control master node in the cloud platform.
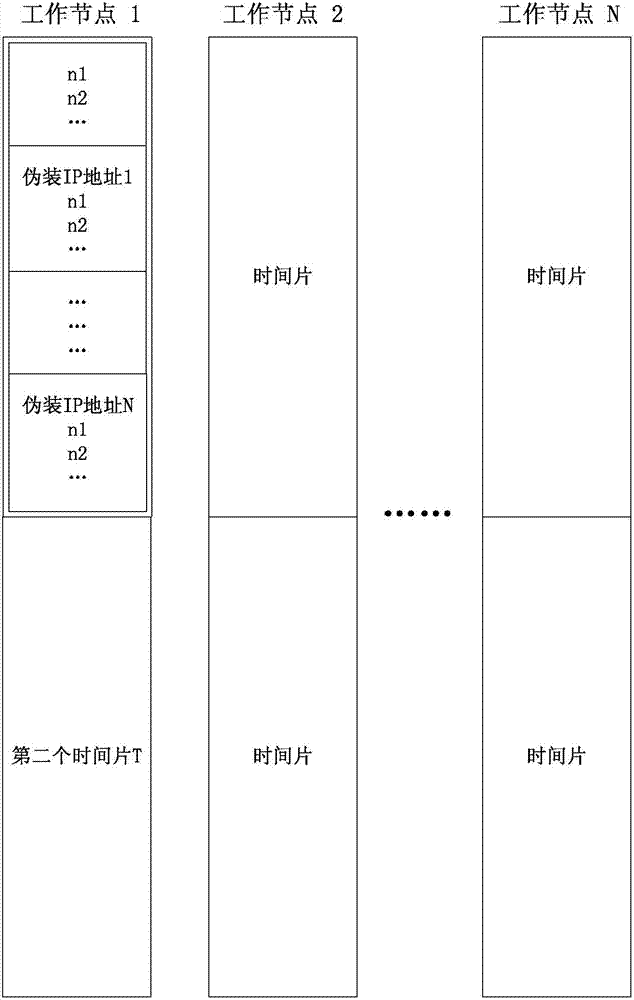
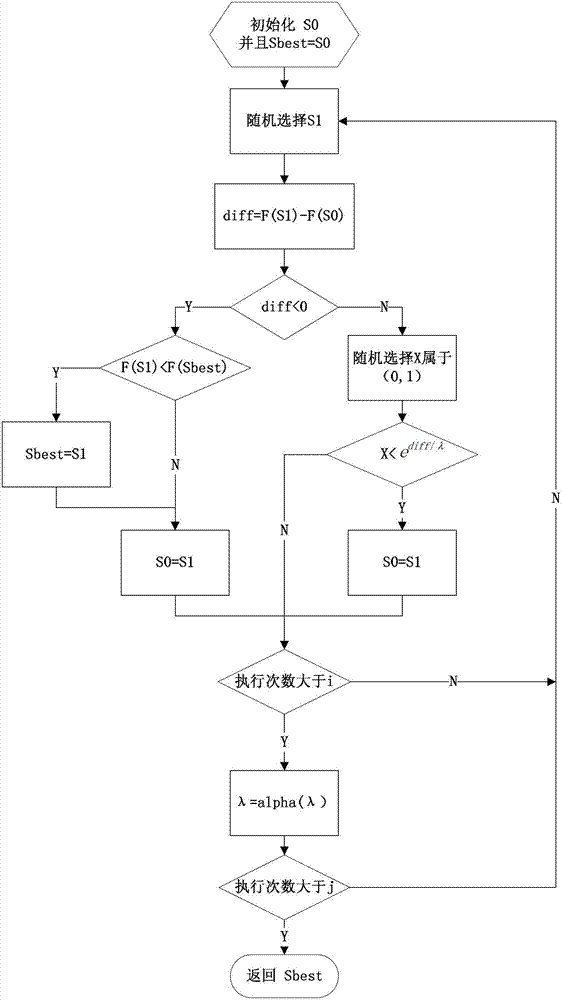
[0023] Step S103, the master control node distributes the port scanning task to multiple working nodes in the cloud platform according to the simulated annealing algorithm.
[0024] In this embodiment, the simulated annealing algorithm includes the following content:
[0025] 1. Determine the scanning methods for the target to be scanned of the plurality of working nodes, such as TCP connection scanning, TCP Syn scanning, TCP FIN scanning, TCP Ack scanning, TCP Null scanning, Xmas scanning, UDP sca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com