CSP (chip scale package) module of TSPI (telephony service provider interface) based on TSM (tivoli storage manager) and CSP implementation method
A technology of interface and connection interface, which is applied in the direction of instrumentation, calculation, electrical digital data processing, etc., and can solve problems such as resource consumption by application manufacturers and resistance to TCM application promotion.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
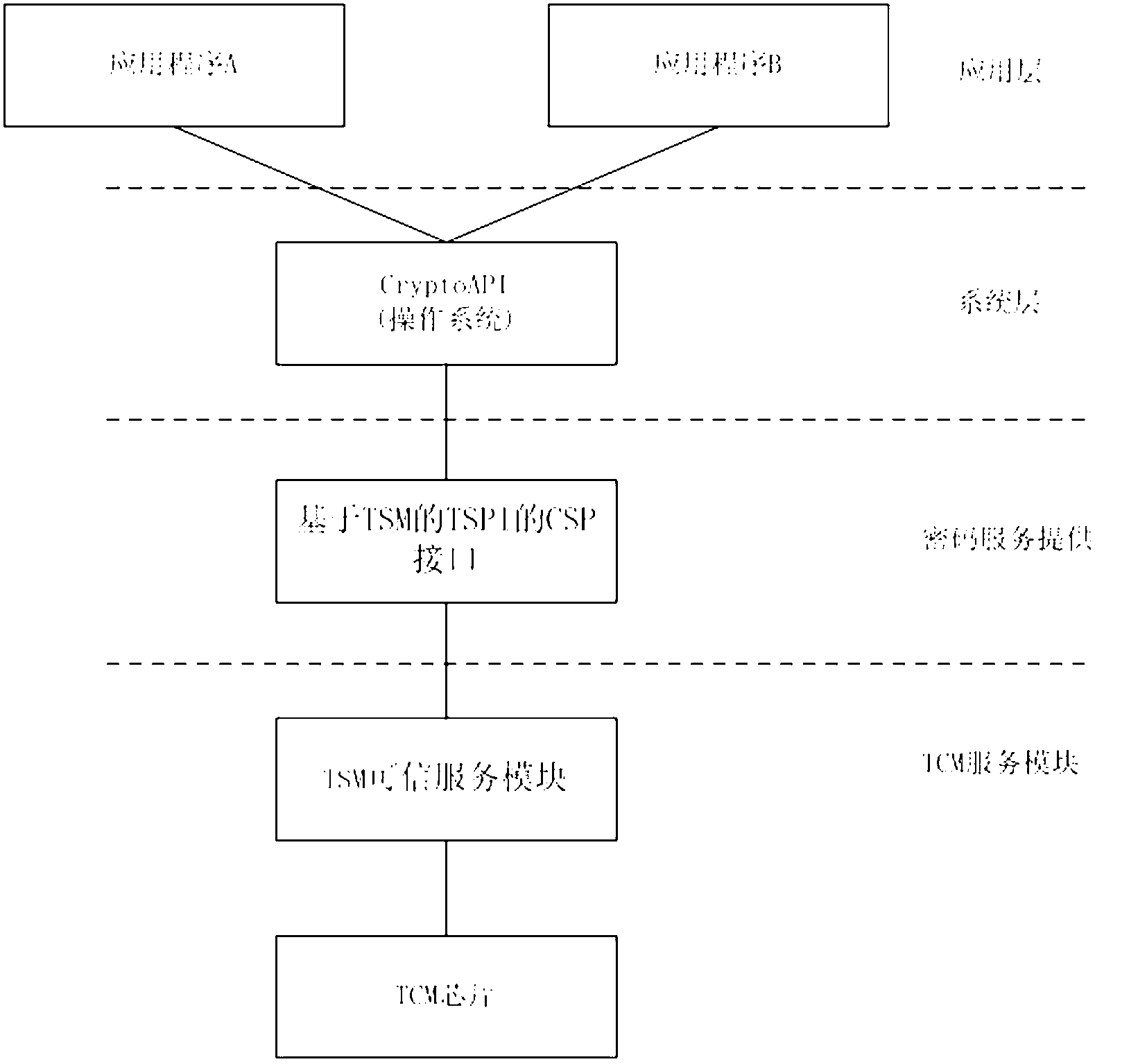
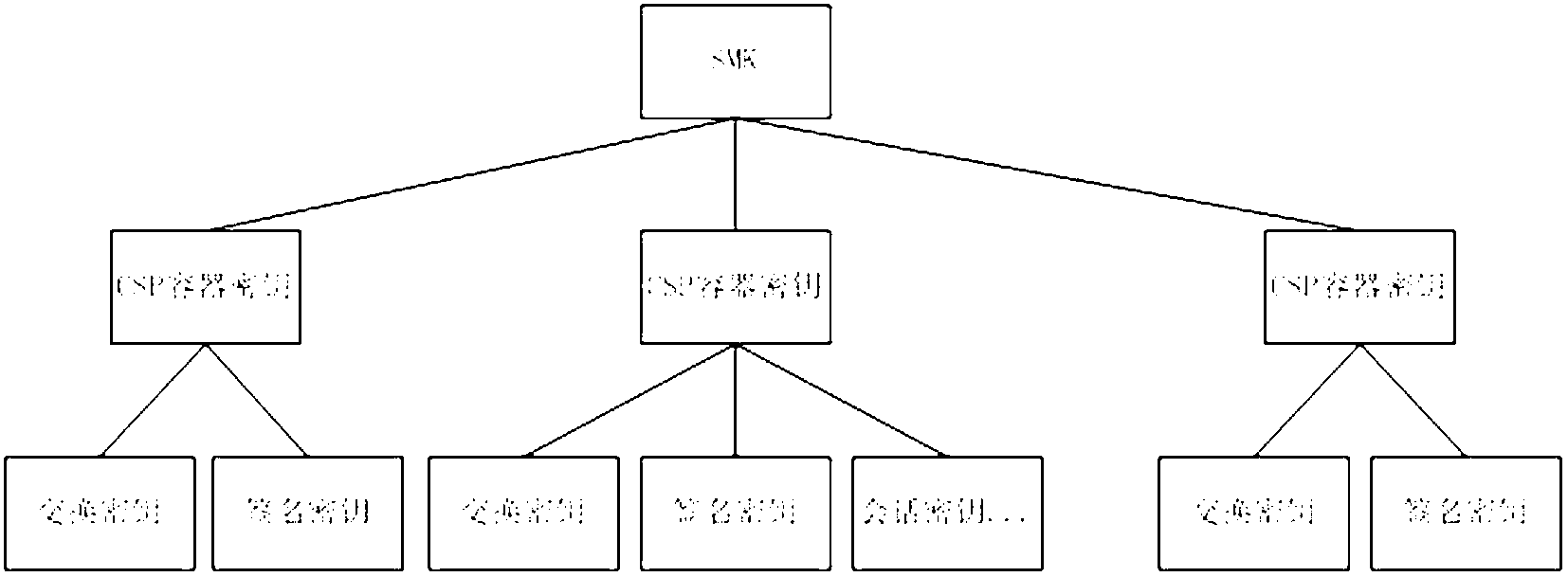
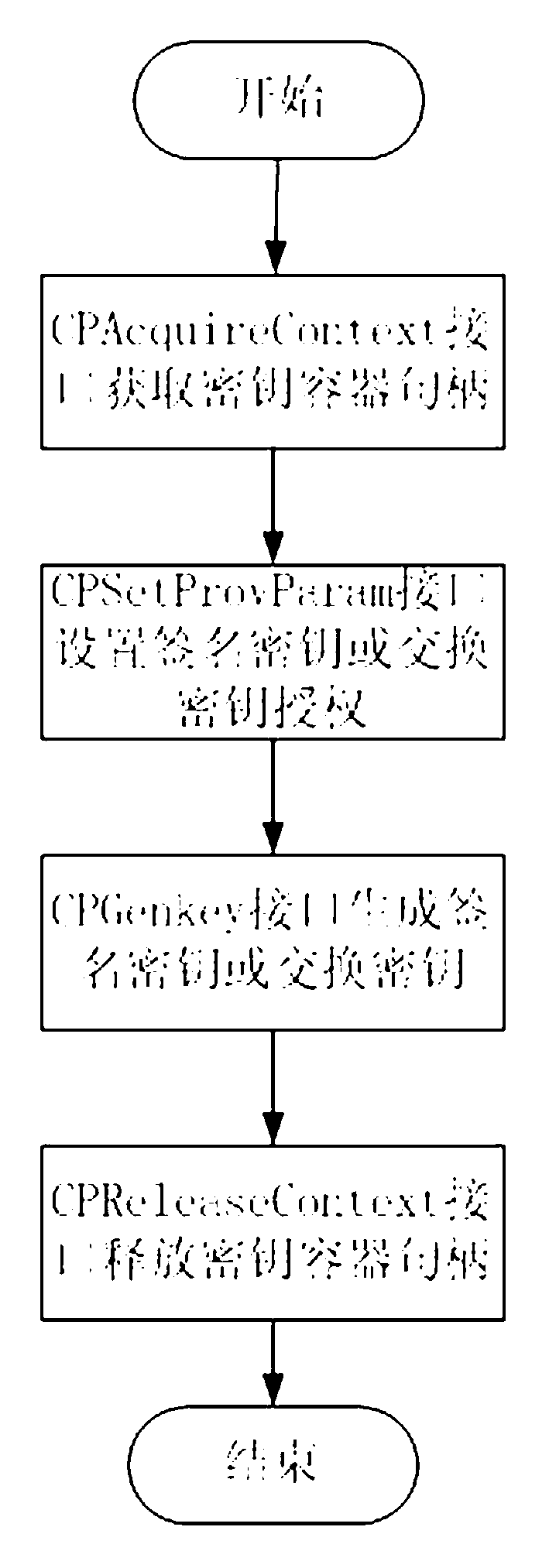
[0073] Such as figure 1 As shown, the CSP cryptographic service system based on the TSPI interface of TSM of the present invention, on the basis of the TSM of the TCM module, utilizes the TCM service call interface TSPI to develop a new set of CSP interface, through this CSP interface, program developers develop The application program can directly utilize the CryptoSPI of Microsoft Corporation to use the encryption service of the CSP provided by the present invention. Program developers do not need to re-learn the TCM cryptographic service call interface system (TSPI), and traditional security applications can be directly transplanted to the TCM module without code modification. It saves a lot of program developme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com