Node authentication method for avoiding authentication congestion
An authentication method and node technology, applied in the computer field, can solve problems such as the system cannot work normally, and achieve the effects of fast recovery of cluster head failure, fast authentication speed and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
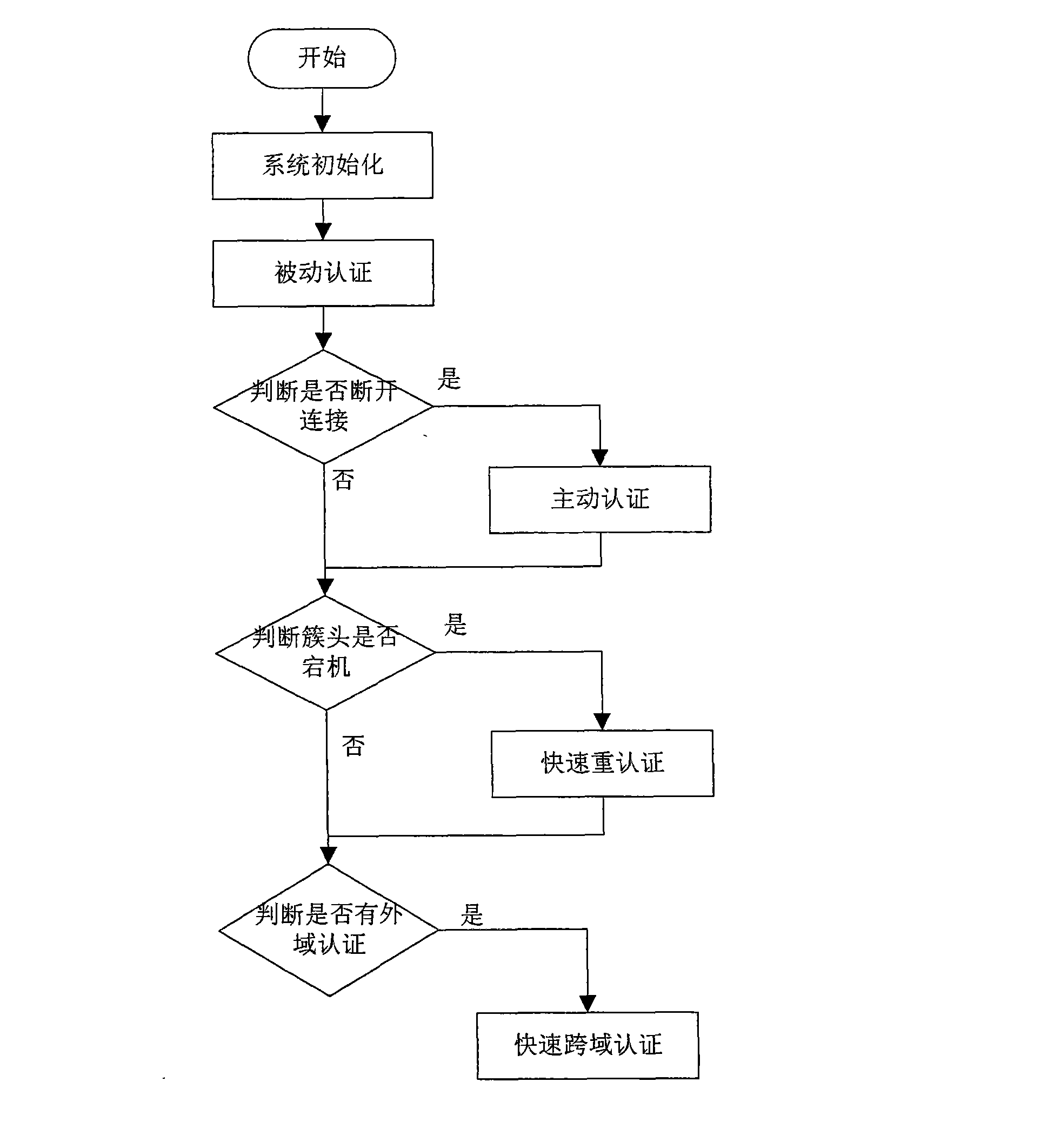
[0042] Below in conjunction with accompanying drawing, the present invention will be further described:
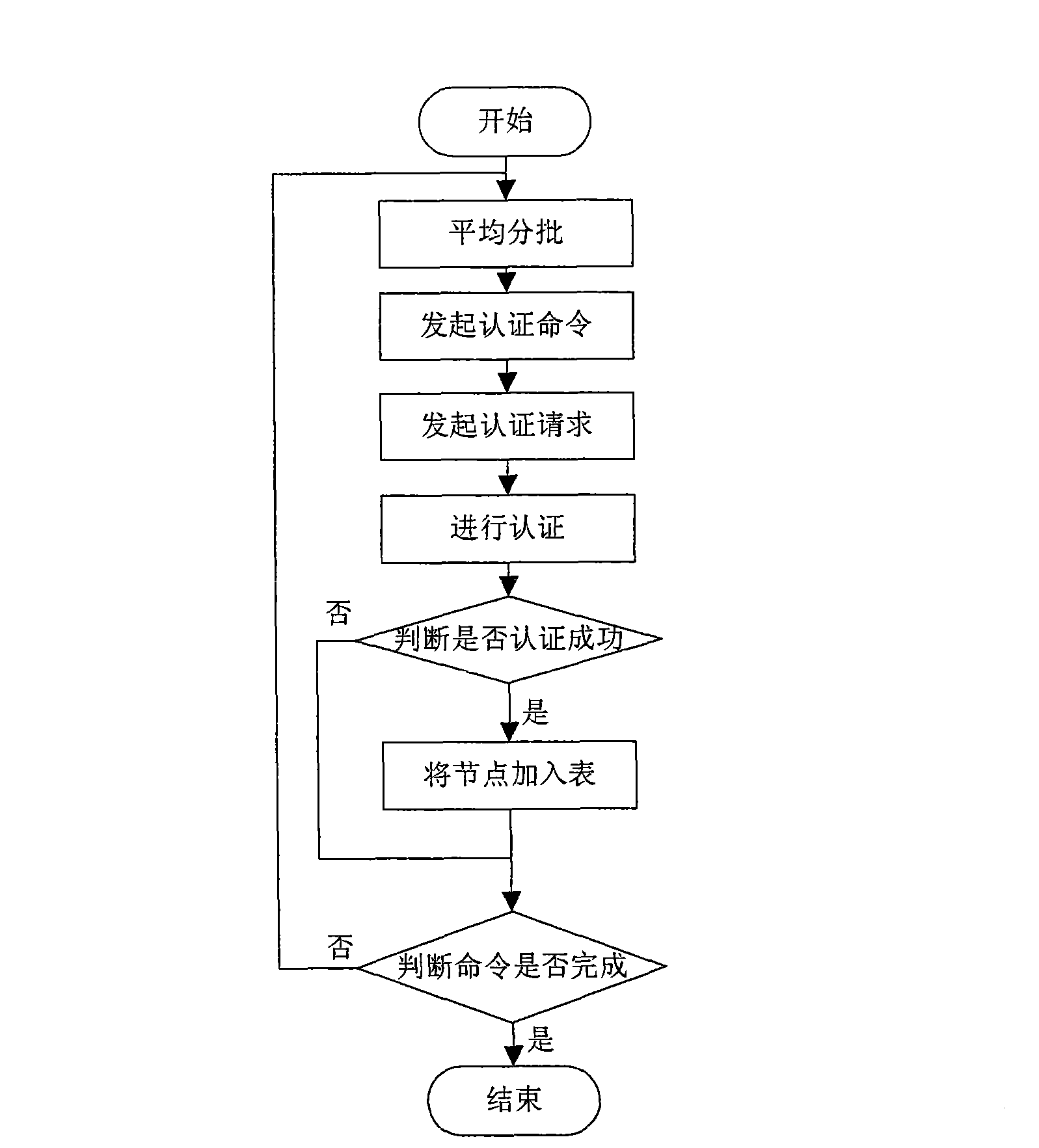
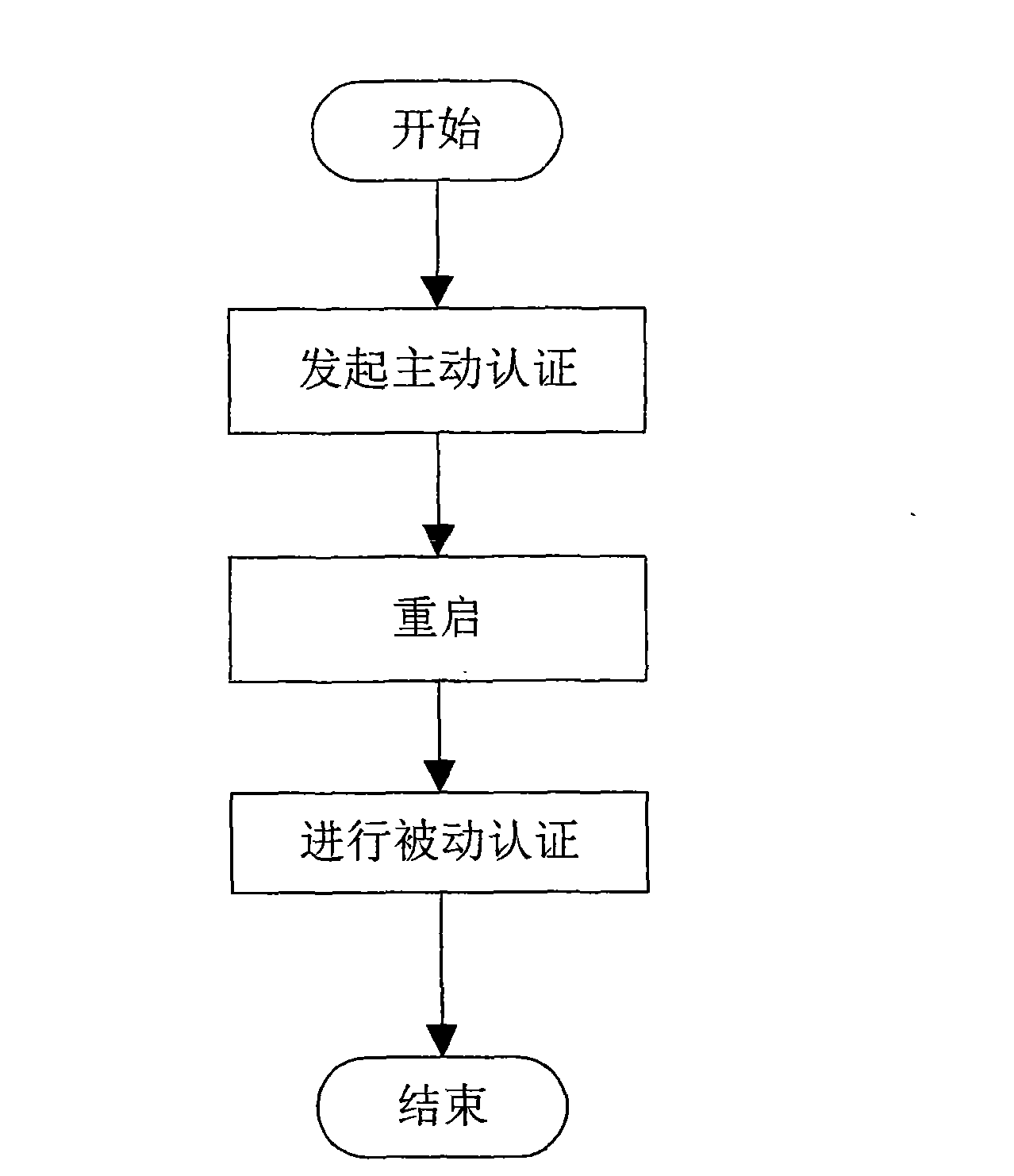
[0043] Applicable environment of the present invention: an overall network is divided into several network areas, and each network area is called a domain; each domain has many nodes and a cluster head node, and nodes in a domain authenticate to the cluster head node, and the cluster head node Then exchange data with the outside world; when the network is established, the node ID will be registered with the cluster head as a registered node, and the cluster head will store all registered nodes in the legal node table. In addition to the legal node table, the cluster head also has a command node table and an authenticated node table.
[0044] Attached below figure 1 Concrete steps of the present invention are further described as follows:
[0045] Step 1, the cluster head and nodes are started, and the legal node table, command node table and authenticated node table are ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com