Method for catching malicious codes
A malicious code and simulator technology, applied in the field of malicious code capture, can solve problems such as insufficient analysis of behavior and attack process, achieve high efficiency and accuracy, and ensure transparency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
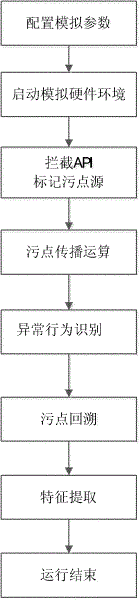
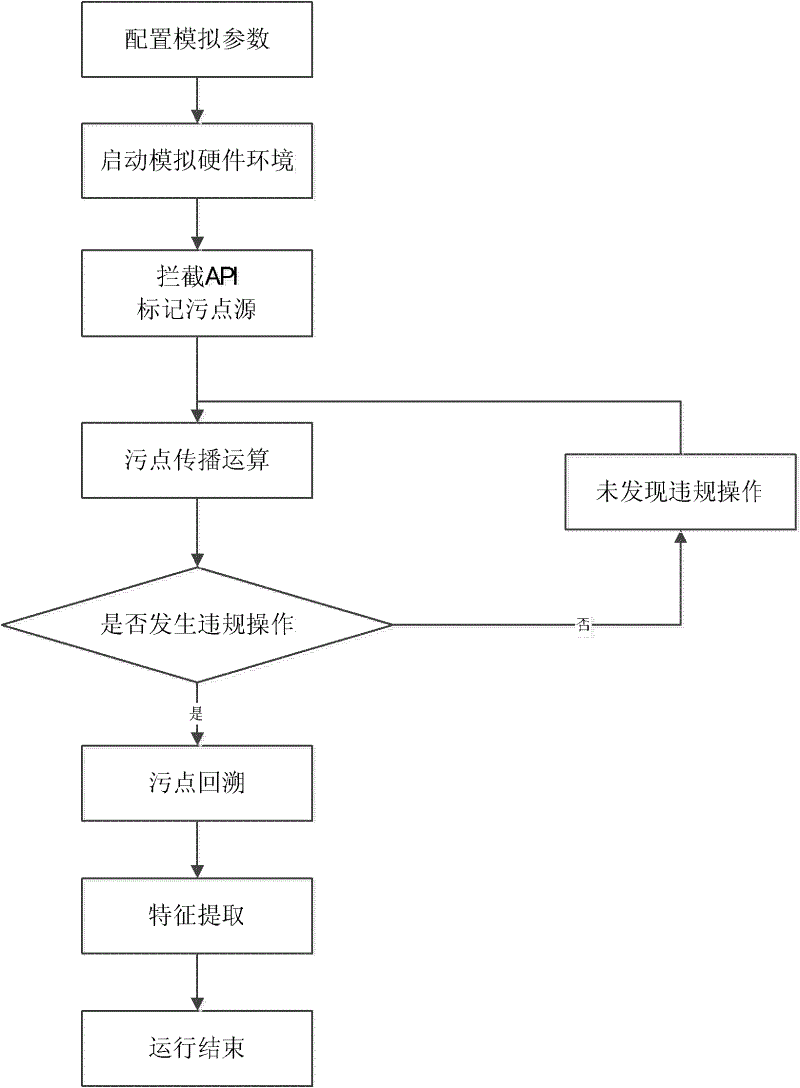
[0045] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
[0046] Such as figure 1 As shown, a method and system for capturing malicious code based on hardware simulator and taint propagation, comprising steps:
[0047] 1. Create the operating system image required for the target file to run
[0048] The invention adopts a linear addressing method to create a virtual image file, which is used as a virtual hard disk, and an operating system is installed on a virtual analysis platform based on the file.
[0049] 2. Configure and start the hardware emulator
[0050] Configure the image path of the operating system to obtain the location of the actual running operating system image; configure the simulated physical memory size, system startup time and simulated CPU type of the hardware emulator, and the hardware emulator allocates a corresponding amount of memory space according to the input memory size , as the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com