Security gateway and method for forwarding webpage by using security gateway
A security gateway and webpage technology, applied in the field of network security, can solve problems such as high dependence, high computing resource requirements, and inability to detect webpage Trojan horses, etc., and achieve the effects of improving detection accuracy, reducing computing overhead, and reducing computing pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] The first embodiment is a method for a security gateway to forward webpages, including:
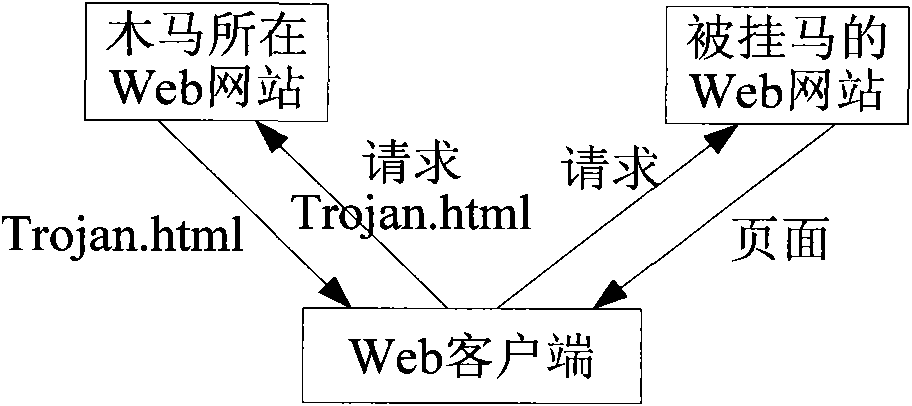
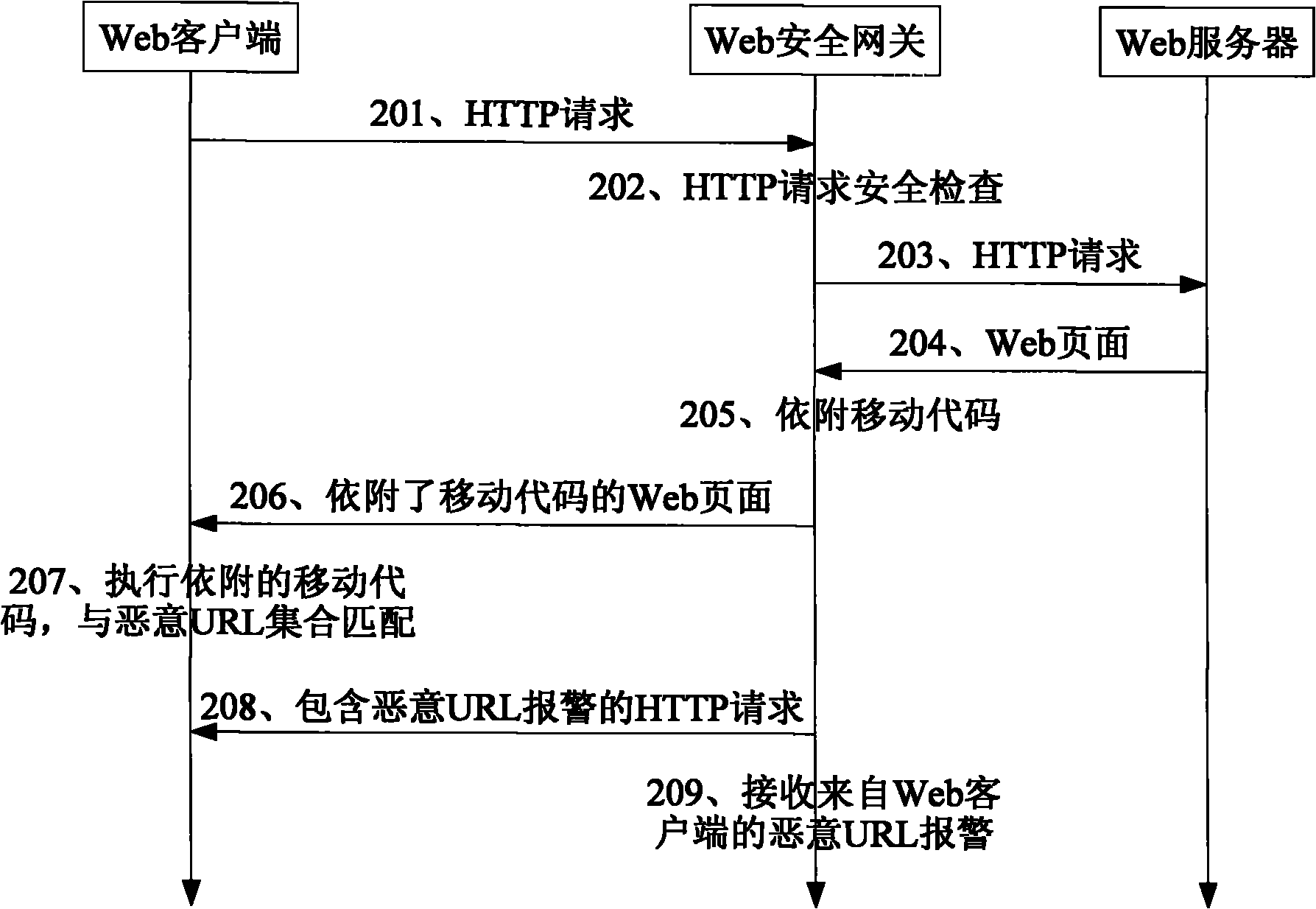
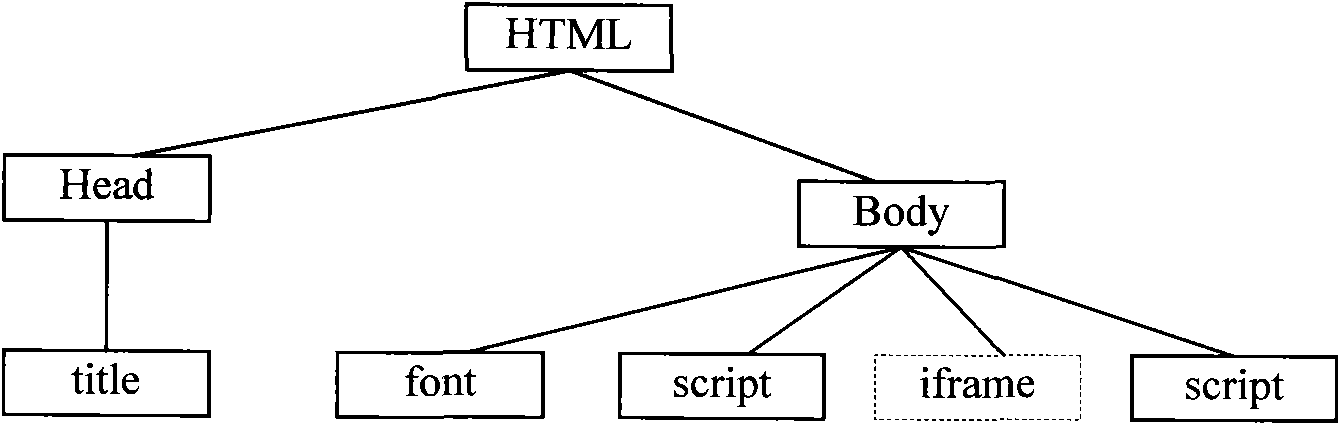
[0051] After getting the Web page requested by the client from the server, attach the pre-generated mobile code to the Web page to be forwarded; the mobile code is set to traverse the document object model corresponding to the attached Web page when executed, and extract Specify the URL in the HTML tag, and match the extracted URL with a preset malicious URL set;
[0052] Adding a command statement to the web page to which the mobile code is attached; the command statement is set to trigger the execution of the mobile code when the web page is loaded;
[0053] The Web page attached with the mobile code and added sentences is forwarded to the client.
[0054] In this embodiment, the mobile code can be interpreted and executed by a Web browser or other programs in the Web client; when a standard Web browser on the Web client loads a Web page that is attached to the mobile code, it will T...
Embodiment 2
[0228] Embodiment two, a security gateway, including:
[0229] The add module is used to attach the pre-generated mobile code to the web page to be forwarded after the web page requested by the client is obtained from the server; the mobile code is set to traverse the document corresponding to the attached web page when executed Object model, extract the URL in the specified HTML tag, and match the extracted URL with the preset malicious URL collection;
[0230] A web page modification module, configured to add a command statement to the web page attached to the mobile code, the command statement set to trigger the execution of the mobile code when the web page is loaded;
[0231] The web page forwarding module is used to forward the web page attached with the mobile code and added sentences to the client.
[0232] In this embodiment, the security gateway may further include:
[0233] A generating module for generating the mobile code;
[0234] And a storage module for storing the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com