Fragment processing method and system
A technology of fragment identification and sender, applied in the field of data communication and Internet security, and can solve problems such as Dos attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
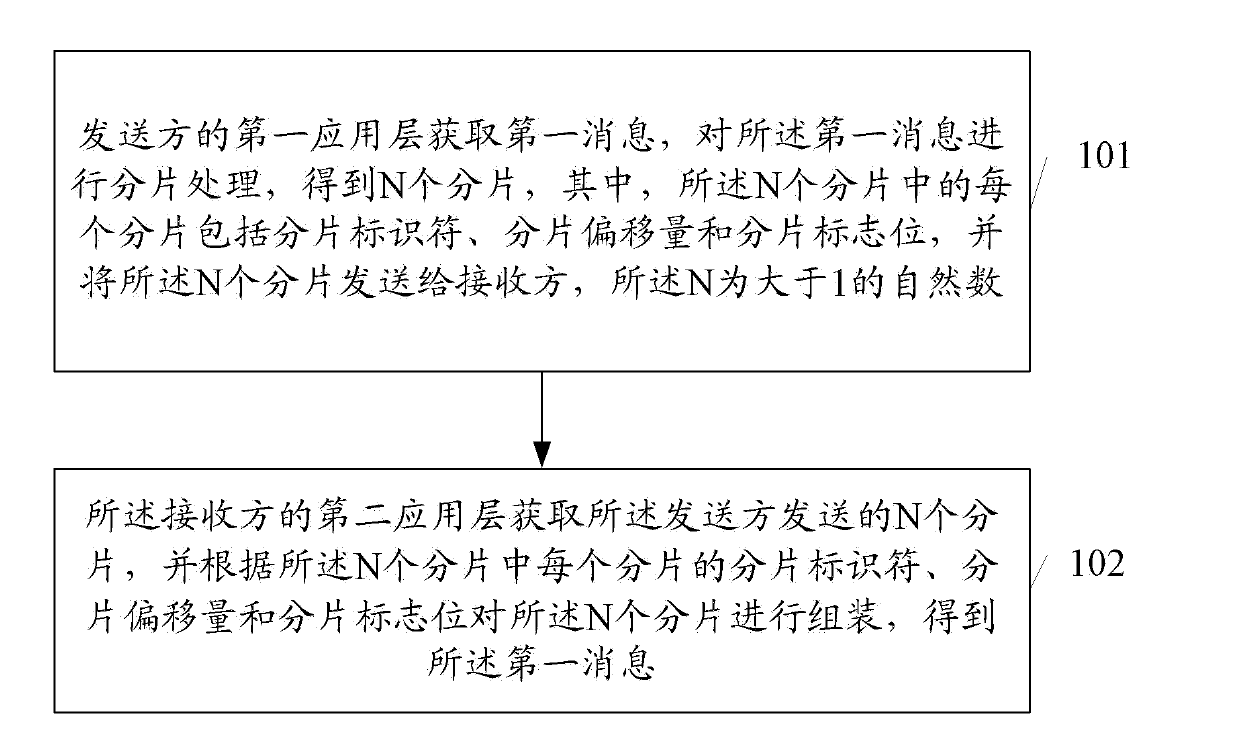
[0061] see figure 1 , the embodiment of the present invention provides a method for slice processing, including:
[0062] 101: The first application layer of the sender acquires the first message, and fragments the first message to obtain N fragments, where each fragment of the N fragments includes a fragment identifier , fragment offset and fragment flag, and send the N fragments to the receiver, where N is a natural number greater than 1;
[0063] 102: The second application layer of the receiver obtains the N fragments sent by the sender, and according to the fragment identifier, fragment offset and fragmentation of each fragment in the N fragments The flag bits are used to assemble the N fragments to obtain the first message.
[0064] In this embodiment, the first message includes IKEv1 and IKEv2 messages, but is not limited to these two messages. The fragmentation identifier is used to identify whether a certain message is a message that needs to be fragmented, and the ...
Embodiment 2
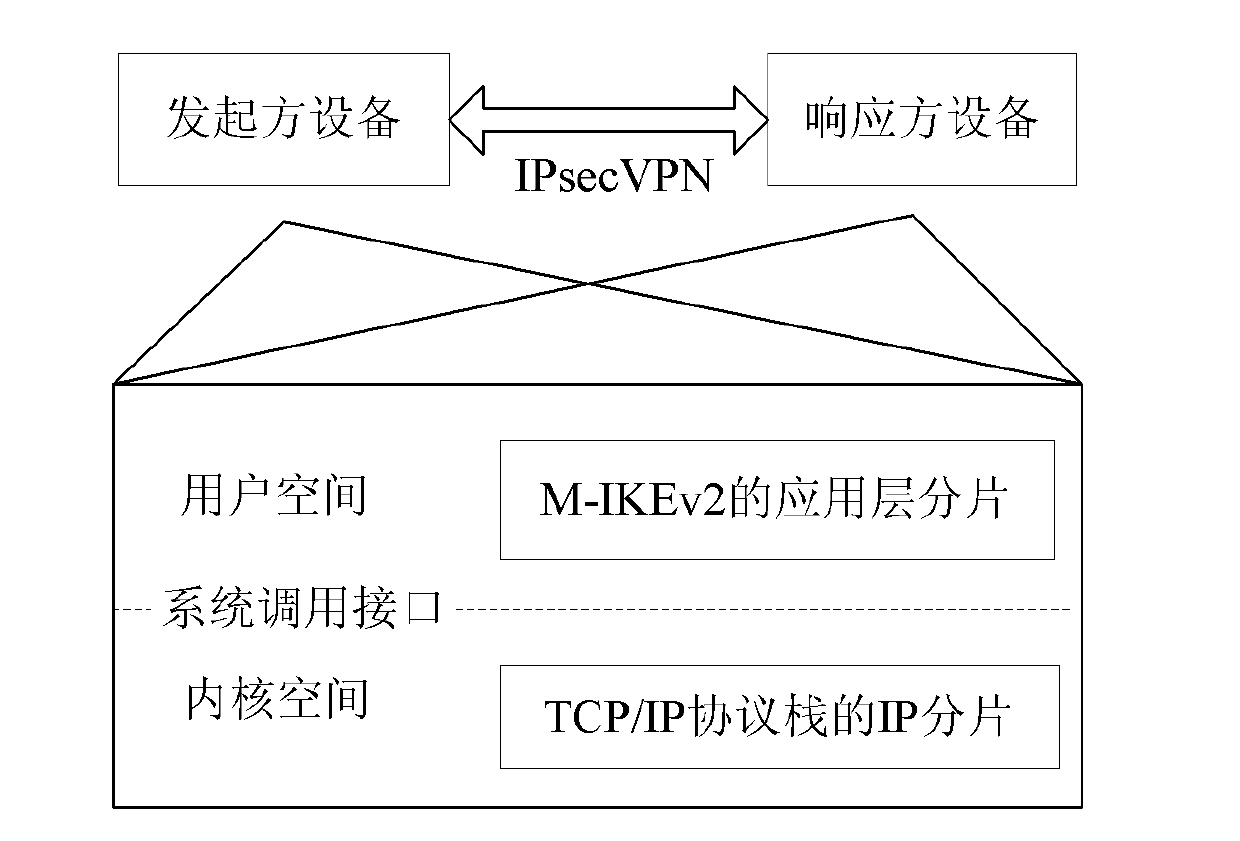
[0084] This embodiment provides a method for slice processing, such as figure 2 Shown is the overall logical system architecture of the IPsec protocol software deployed on the security gateway. Both the sender device and the receiver device need to install the M-IKEv2 protocol. This figure also shows the M-IKEv2 protocol application layer fragmentation and TCP / IP fragmentation. The location of slices in the entire system, the M-IKEv2 protocol application layer slices are in the user space, and the TCP / IP slices are in the kernel space.
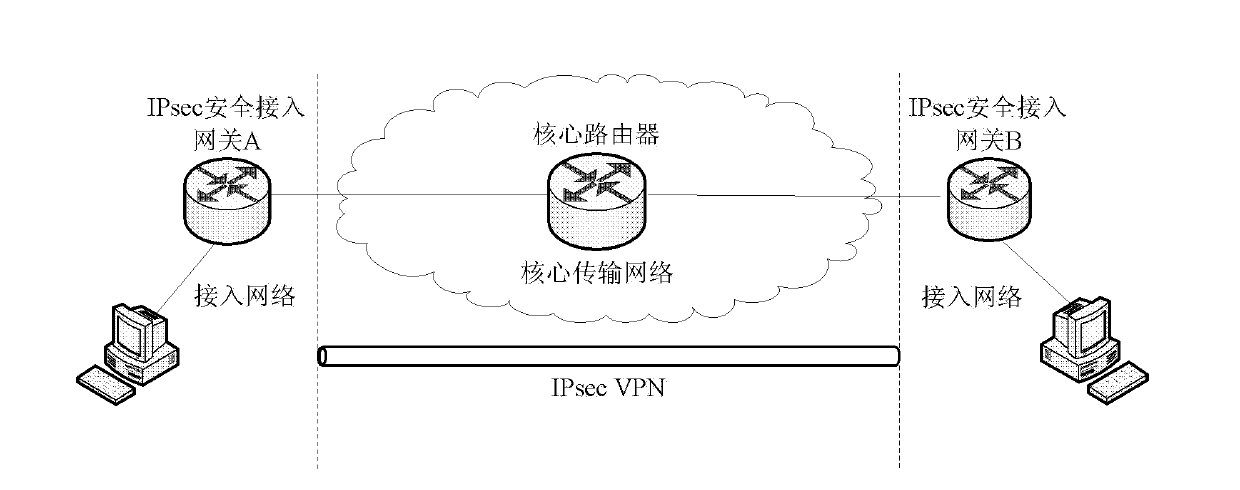
[0085] Such as image 3 Shown is the deployment method of the security gateway-security gateway in the actual network application scenario. In this embodiment, two routers connected to the transmission network are required to deploy the IPsec and M-IKEv2 protocols, and one transmission network is required to connect the two security gateways. transfer data packets between them. The core network router is a high-performance IP router, and th...
Embodiment 3
[0150] see Figure 11 , the embodiment of the present invention provides a fragment processing system, including: a sender 301 and a receiver 302, the sender 301 includes a first application layer, and the receiver 302 includes a second application layer;
[0151] The first application layer of the sender is configured to obtain the first message, and perform fragment processing on the first message to obtain N fragments, wherein each fragment in the N fragments includes a fragment slice identifier, slice offset and slice flag, and send the N slices to the receiver, where N is a natural number greater than 1;
[0152] The second application layer of the receiver is configured to obtain the N fragments sent by the sender, and according to the fragment identifier, fragment offset and fragmentation of each fragment in the N fragments The fragment flag bit is used to assemble the N fragments to obtain the first message.
[0153] Wherein, the first application layer of the sender...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com