Software upgrading method of terminal equipment
A technology for terminal equipment and software upgrades, applied in the field of software upgrades, can solve problems such as data loss and achieve a good user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
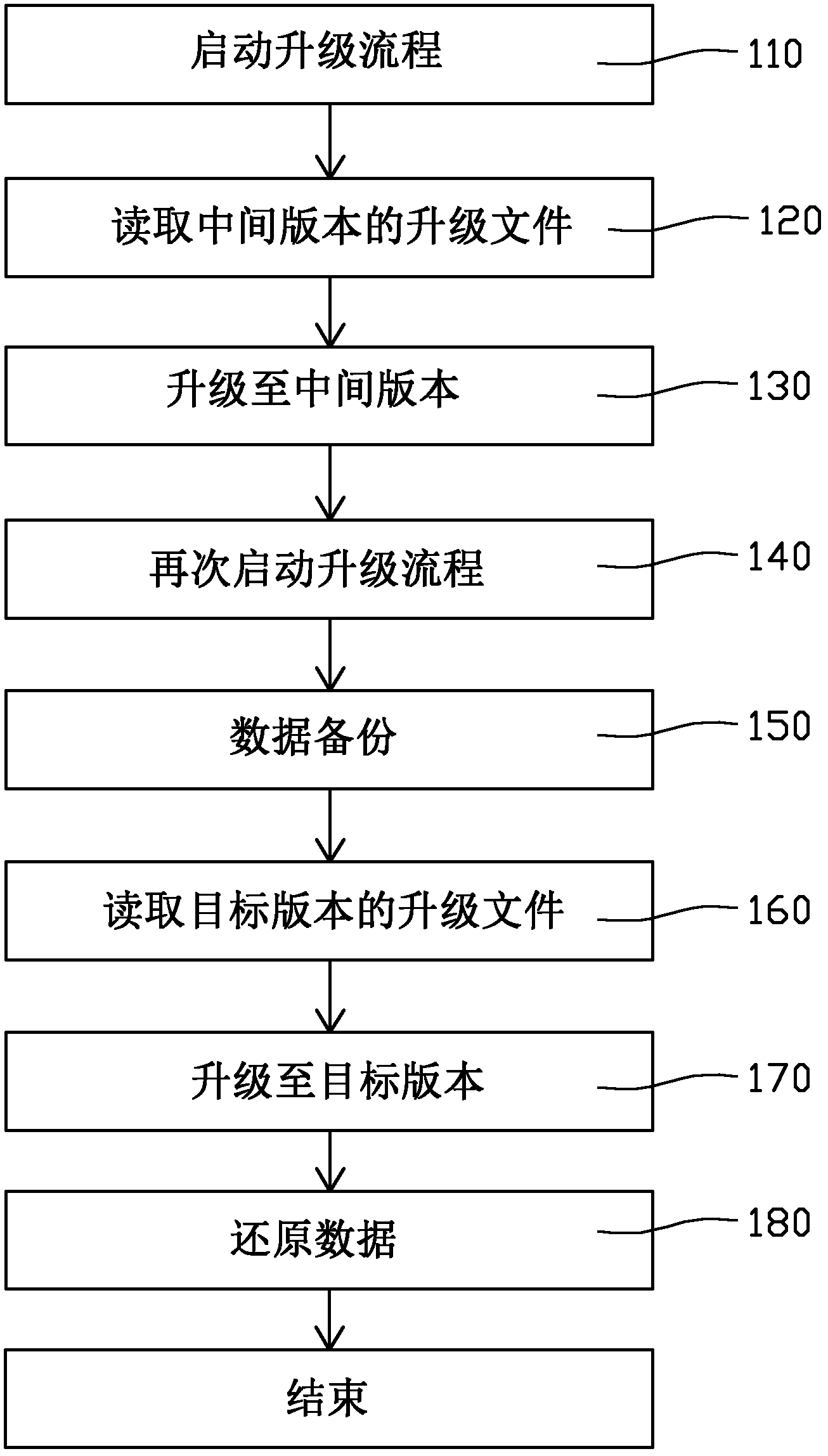
[0018] see figure 1 , which is a flow chart of the method for upgrading software of a terminal device provided in the first embodiment. First, step 110 is executed to start the upgrade process. Specifically, a mobile storage device may be connected to the terminal device first, and a predetermined key or combination of keys on the terminal device may be pressed to start an upgrade program built in the terminal device. Here, the terminal device may be, for example, a digital TV, a set-top box, a router, a home gateway, and the like. The terminal device may include a main control chip, a first storage, a second storage and a USB interface. Wherein the first memory is the main memory, which has relatively large space, and is used for storing the underlying system software and user data of the digital TV. User data includes, for example, installed software, plug-ins, usage records, and registration information. The second memory is used to store a small amount of information t...
no. 2 example
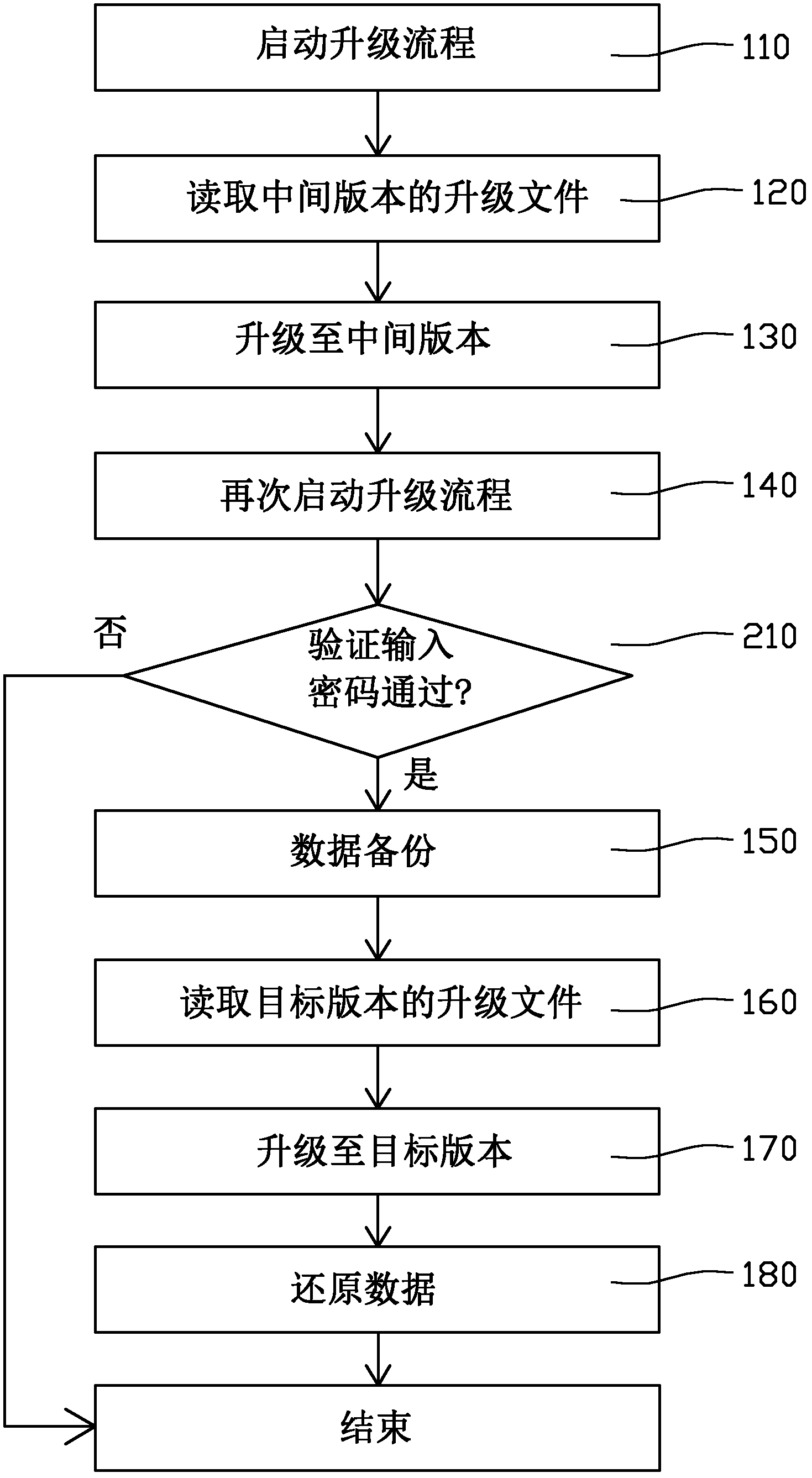
[0028] refer to figure 2 The second embodiment provides a software upgrade method for terminal equipment, which is similar to the software upgrade method of the first embodiment, except that the intermediate version has a password verification function in addition to the data backup function. Correspondingly, a step 210 is also included between step 140 and step 150, verifying the input password. Only after the password verification is passed can the data backup and upgrade operations continue, otherwise the upgrade process ends. Here, the password can be obtained by directly using the hardware information of the terminal device or by using a certain algorithm to calculate the above hardware information. The hardware information may be, for example, the MAC address of the network card, the product serial number of the terminal device, and the like. These hardware information are generally unique, that is to say, a password is valid only for this terminal.
[0029] In the m...
no. 3 example
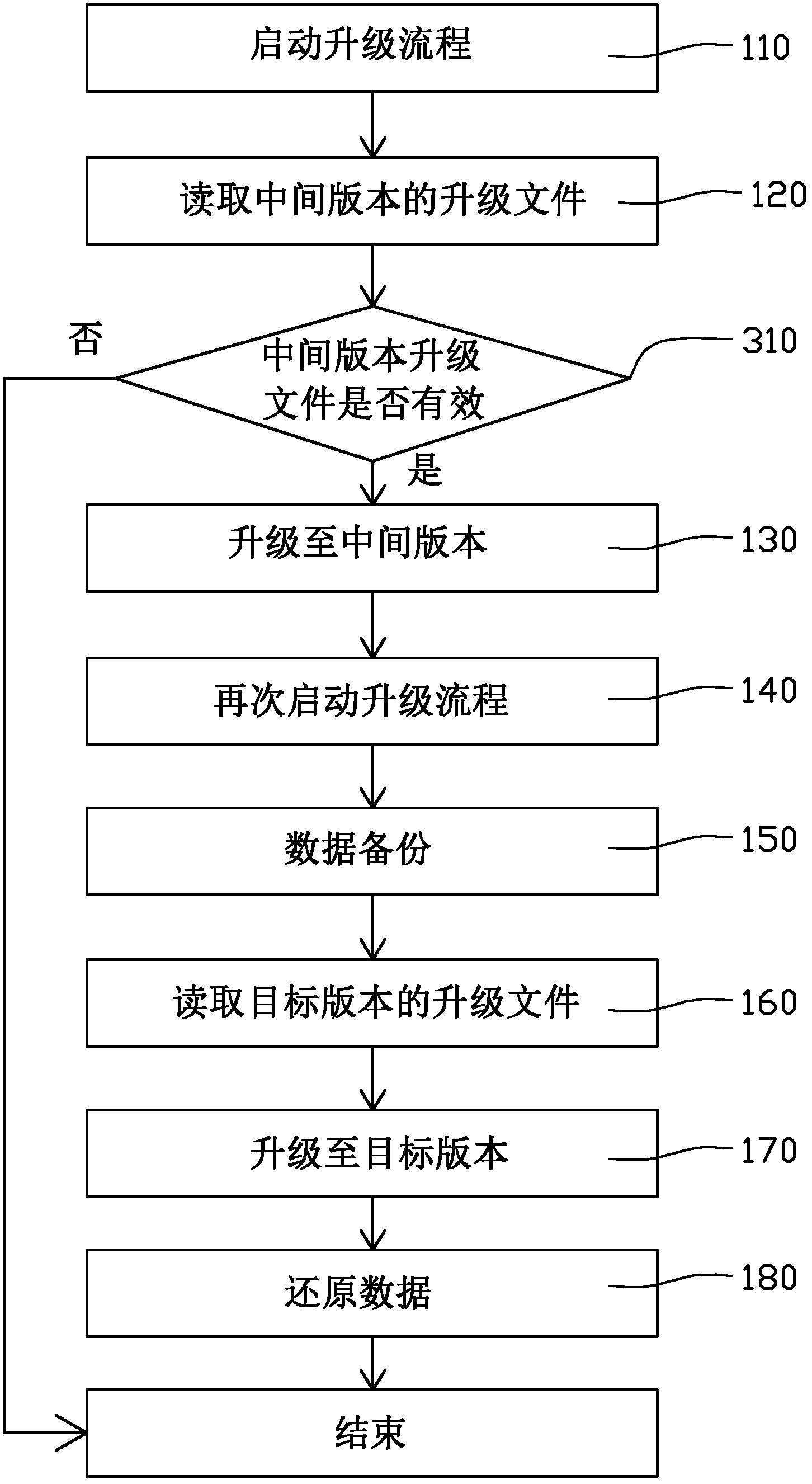
[0031] refer to image 3 , the third embodiment provides a software upgrade method for terminal equipment, which is similar to the software upgrade method of the first embodiment, the difference is that a step 310 is also included between step 120 and step 130 to determine the intermediate version Whether the upgrade file of the intermediate version is valid, the subsequent step 130 is performed only when the upgrade file of the intermediate version is valid, otherwise the upgrade process ends. Here, judging whether the upgrade file of the intermediate version is valid can be realized by reading the version number and other contents of the upgrade file. For example, an intermediate version is only considered valid if its base version matches the version the end device is currently running.
[0032] In the software upgrading method of the terminal device in this embodiment, since the process of judging whether the intermediate version is valid is also included before performin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com