A method and device for monitoring effective visits of application programs
An application and access technology, applied in the computer field, can solve the problems of ineffective access, cheating of APP usage, and increased usage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
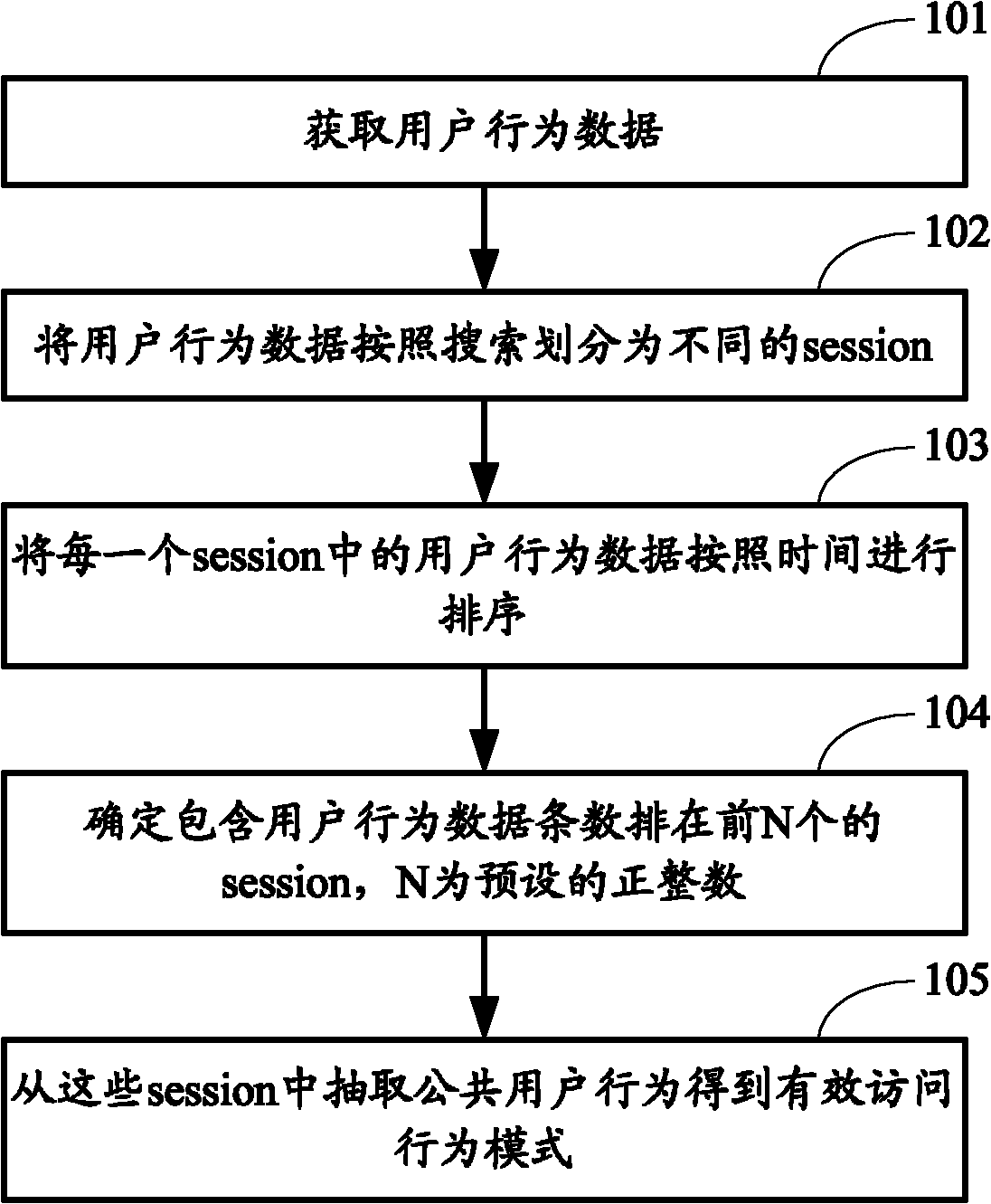
[0077] figure 1 The flow chart of the method for mining APP effective access behavior patterns provided by Embodiment 1 of the present invention, as shown in figure 1 As shown, the specific mining process may include the following steps:
[0078] Step 101: Obtain user behavior data.
[0079] In this step, user behavior data within a set time range can be obtained from user access logs.
[0080] Step 102: Divide user behavior data into different sessions according to searches.
[0081] A session can include multiple pieces of user behavior data, representing a search and the behavior after the search, such as click and loading behavior. In addition to dividing sessions according to search, user behavior data can also be divided into different sessions according to clicks. At this time, a session represents a click and the behavior after the click. User behavior data can also be divided into different sessions according to loading. At this time, a session represents a loadin...
Embodiment 2
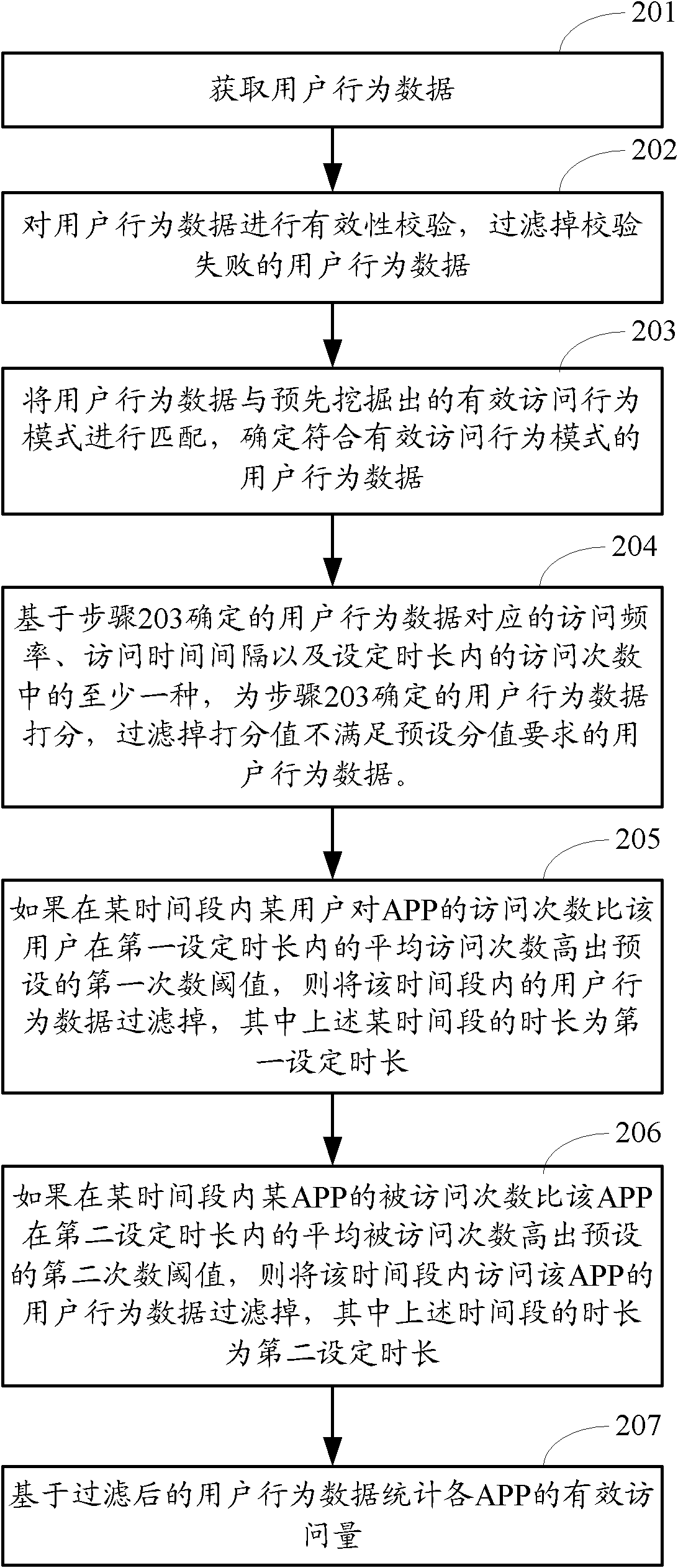
[0091] figure 2 The flow chart of the method for monitoring the effective visits of APP provided by Embodiment 2 of the present invention, such as figure 2 As shown, the method may include the following steps:
[0092] Step 201: Obtain user behavior data.
[0093] Usually, user behavior data is recorded in the user access log. In this step, the user behavior data can be obtained from the user access log.
[0094] Wherein, the user behavior data may include but not limited to: behavior data of searching APP, clicking APP behavior data, loading APP behavior data and dwell time corresponding to various user behaviors.
[0095] Step 202: Verify the validity of the user behavior data, and filter out the user behavior data that fails the verification.
[0096] The aforementioned validity verification includes but is not limited to: cookie verification, key verification or reference (refer) verification.
[0097] Wherein, when performing cookie verification, if the cookie is em...
Embodiment 3
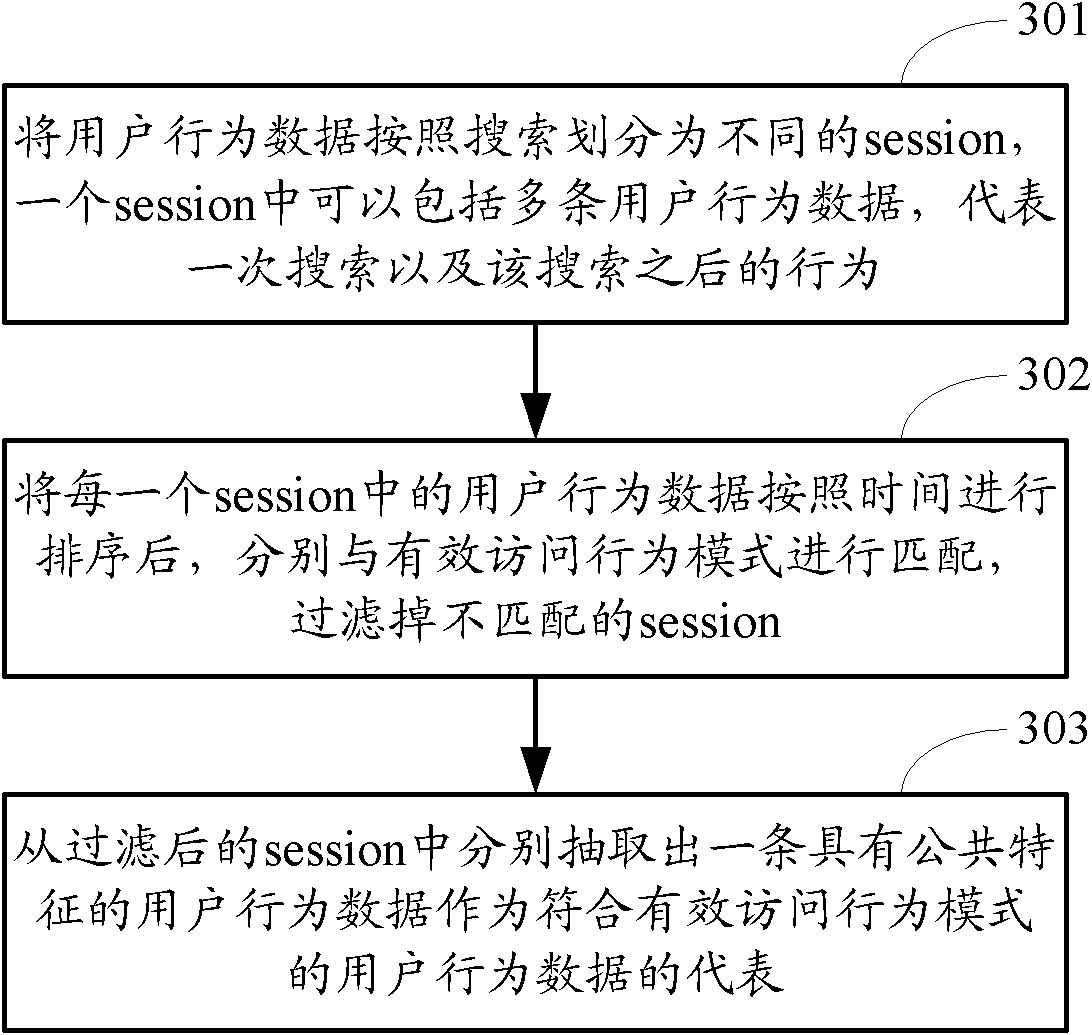
[0122] Figure 4 The structure diagram of the device for mining APP effective access behavior patterns provided by Embodiment 3 of the present invention, as shown in Figure 4 As shown, the apparatus may include: a data acquisition unit 400 , a session segmentation unit 410 , a behavior sorting unit 420 , a session determination unit 430 and a pattern extraction unit 440 .
[0123] The data acquisition unit 400 acquires user behavior data.
[0124] The session segmentation unit 410 divides the user behavior data into sessions according to the preset user behavior, and each session represents the preset user behavior and the behavior after the preset user behavior. Wherein, the preset user behavior may include: a behavior of searching for an APP, a behavior of clicking an APP, or a behavior of loading an APP.
[0125] The behavior sorting unit 420 sorts the user behavior data in each session according to time.
[0126] The session determination unit 430 determines the sessio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com