Client computer for protecting confidential file, server computer therefor, method therefor, and computer program
A technology for confidential documents and computers, applied in computer security devices, computing, digital data protection, etc., can solve problems such as reduced office efficiency and poor convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0095] Hereinafter, embodiments of the present invention will be described with reference to the drawings. It should be understood that this example is an example illustrating a preferred embodiment of the present invention, and the content described here is not intended to limit the scope of the present invention. Also, the same symbols in the following drawings refer to the same objects unless otherwise specified.
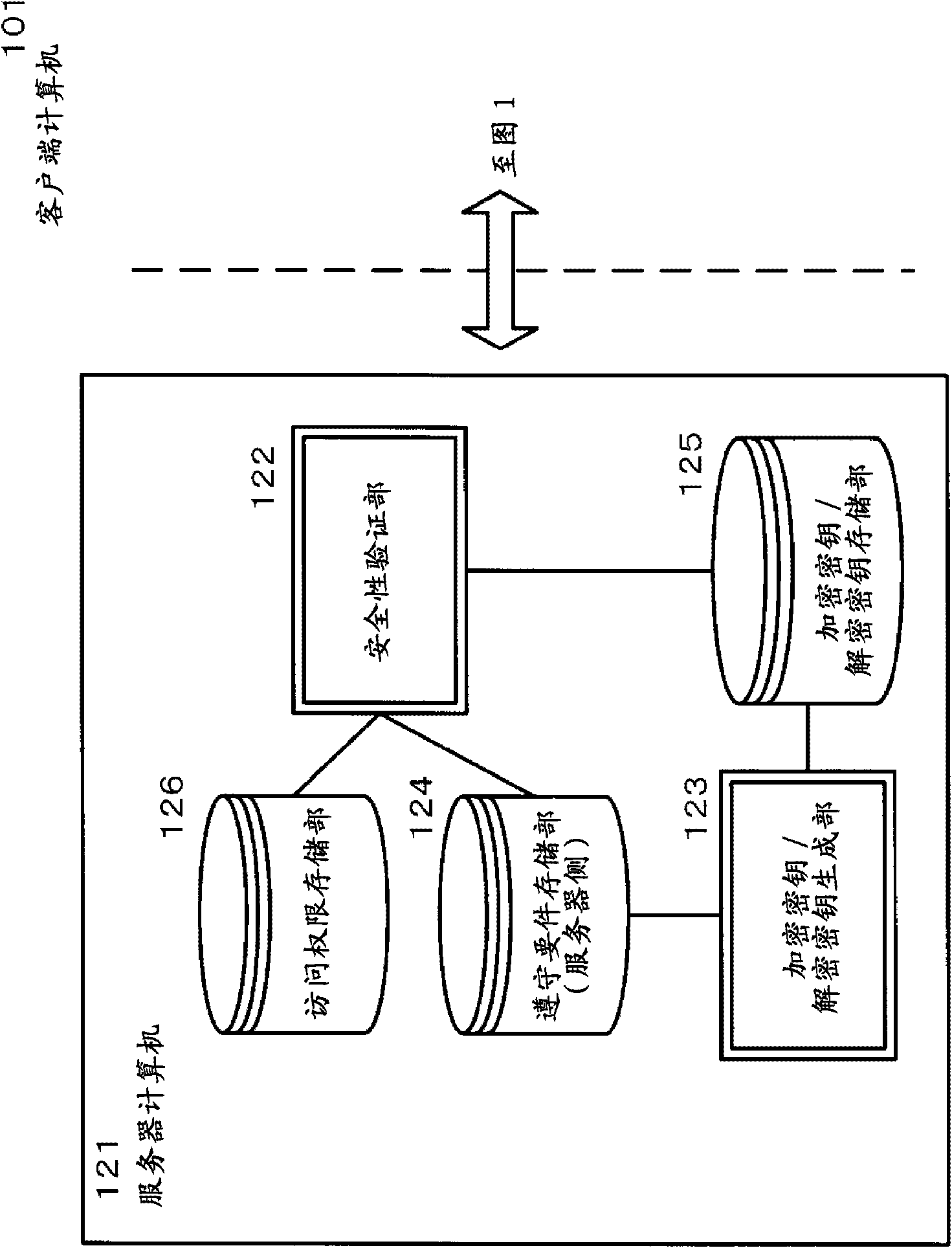
[0096] figure 1 An example of a configuration of a client computer (101) representing an embodiment of the present invention is shown.
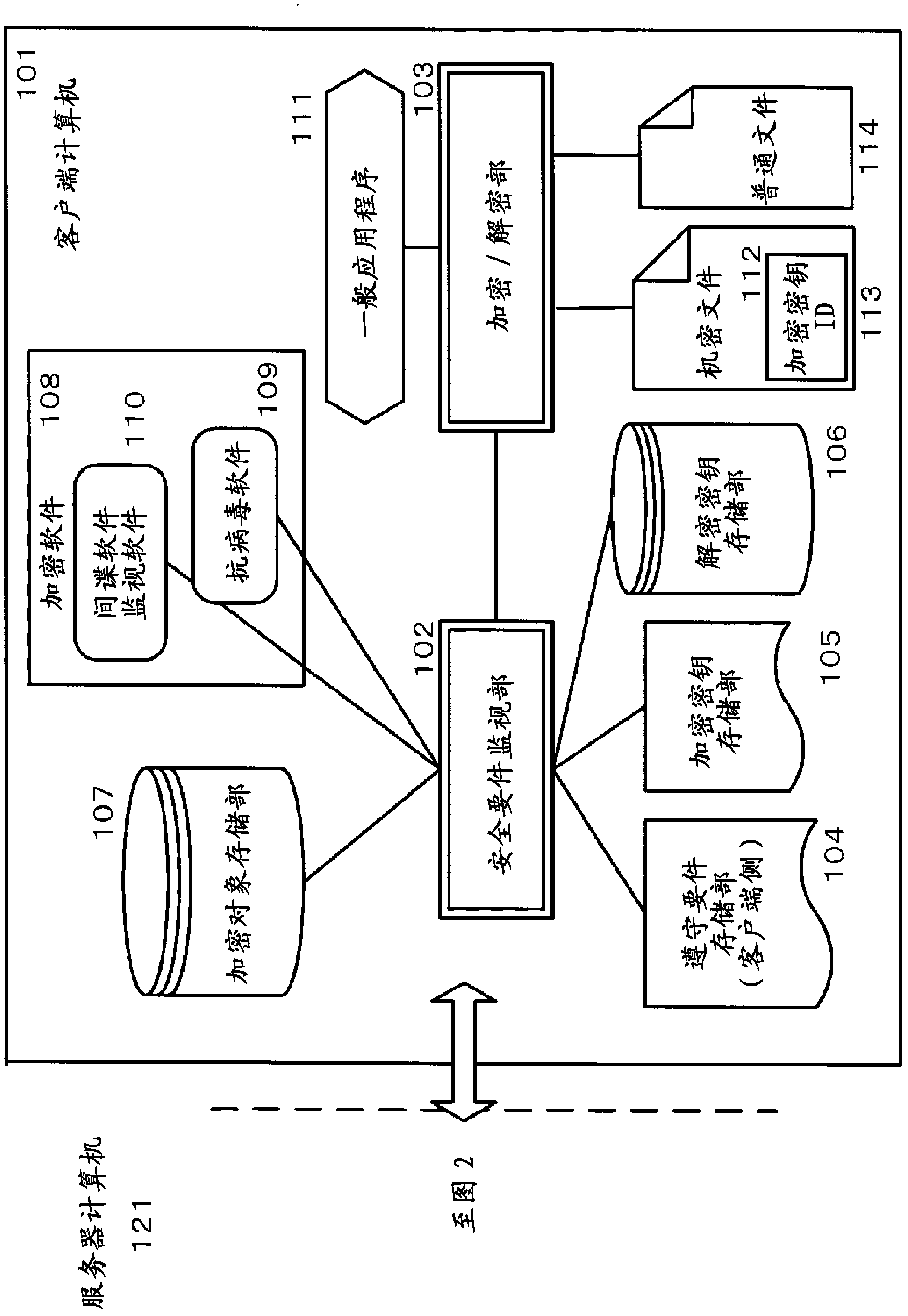
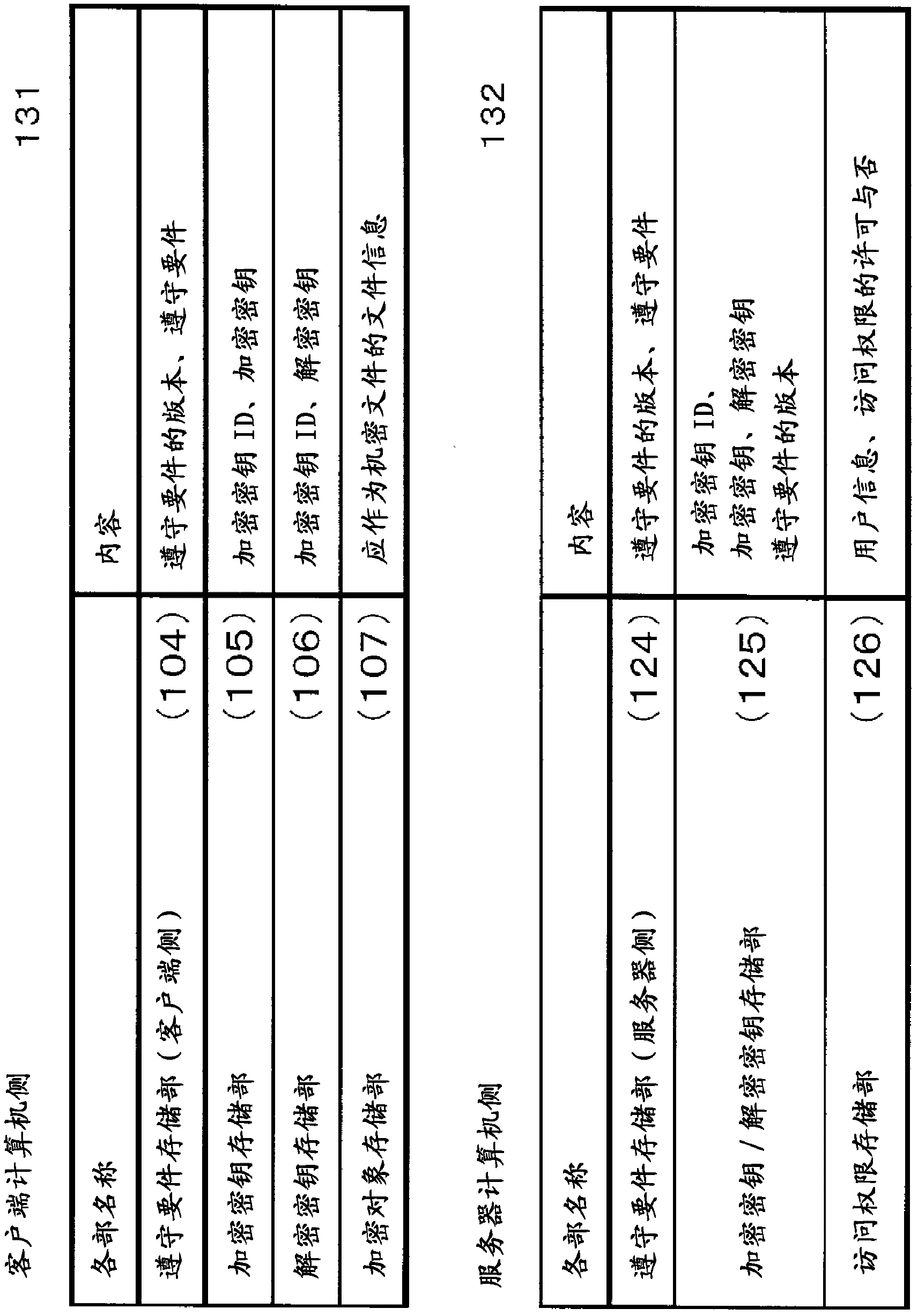
[0097] The client computer (101) includes a security requirement monitoring unit (102), an encryption / decryption unit (103), a compliance requirement storage unit (client side) (104), an encryption key storage unit (105), a decryption key storage unit part (106), encrypted object storage part (107). In addition, security software (108) such as antivirus software (109) and spyware monitoring software (110) and general applica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com