Method for realizing program killing prevention
A process and byte technology, applied in the field of process anti-killing, to achieve the effect of protecting against illegal shutdown
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
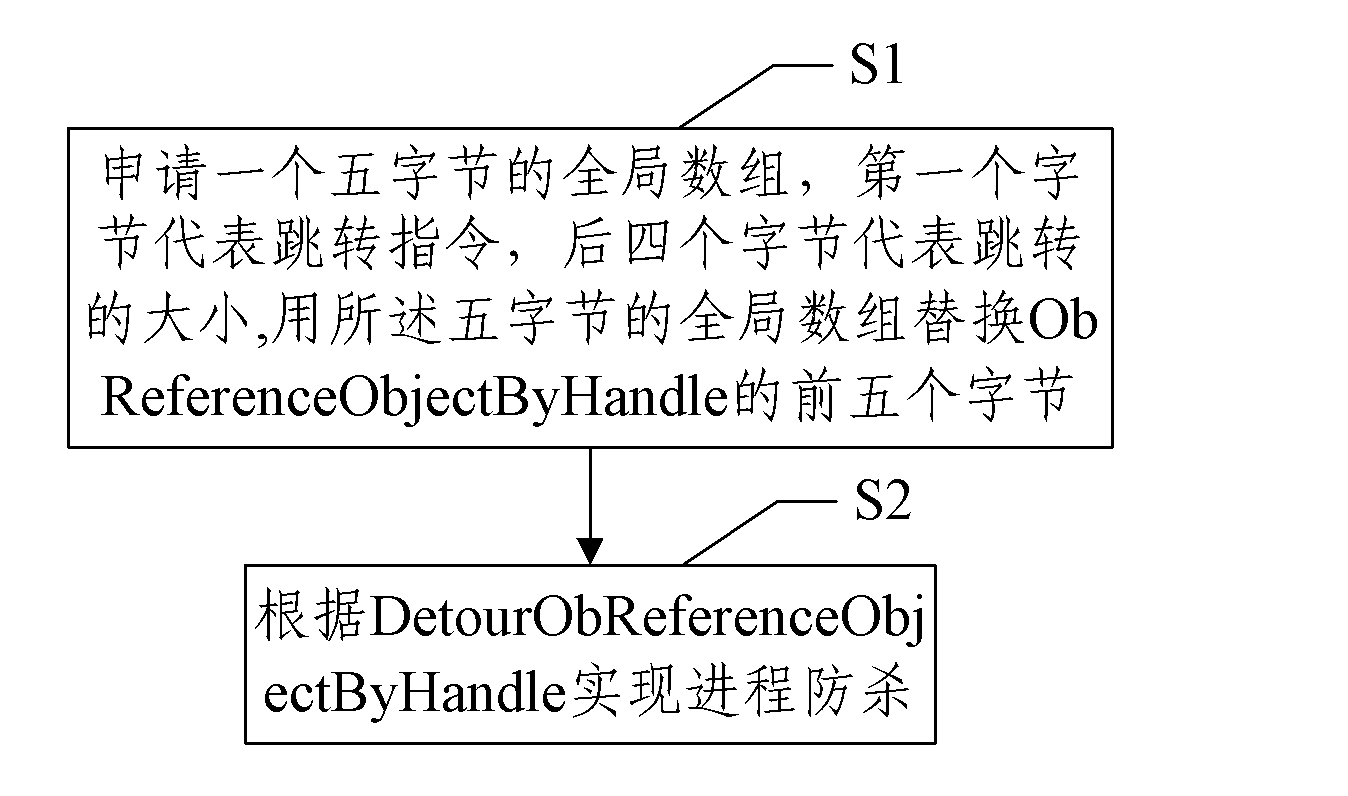
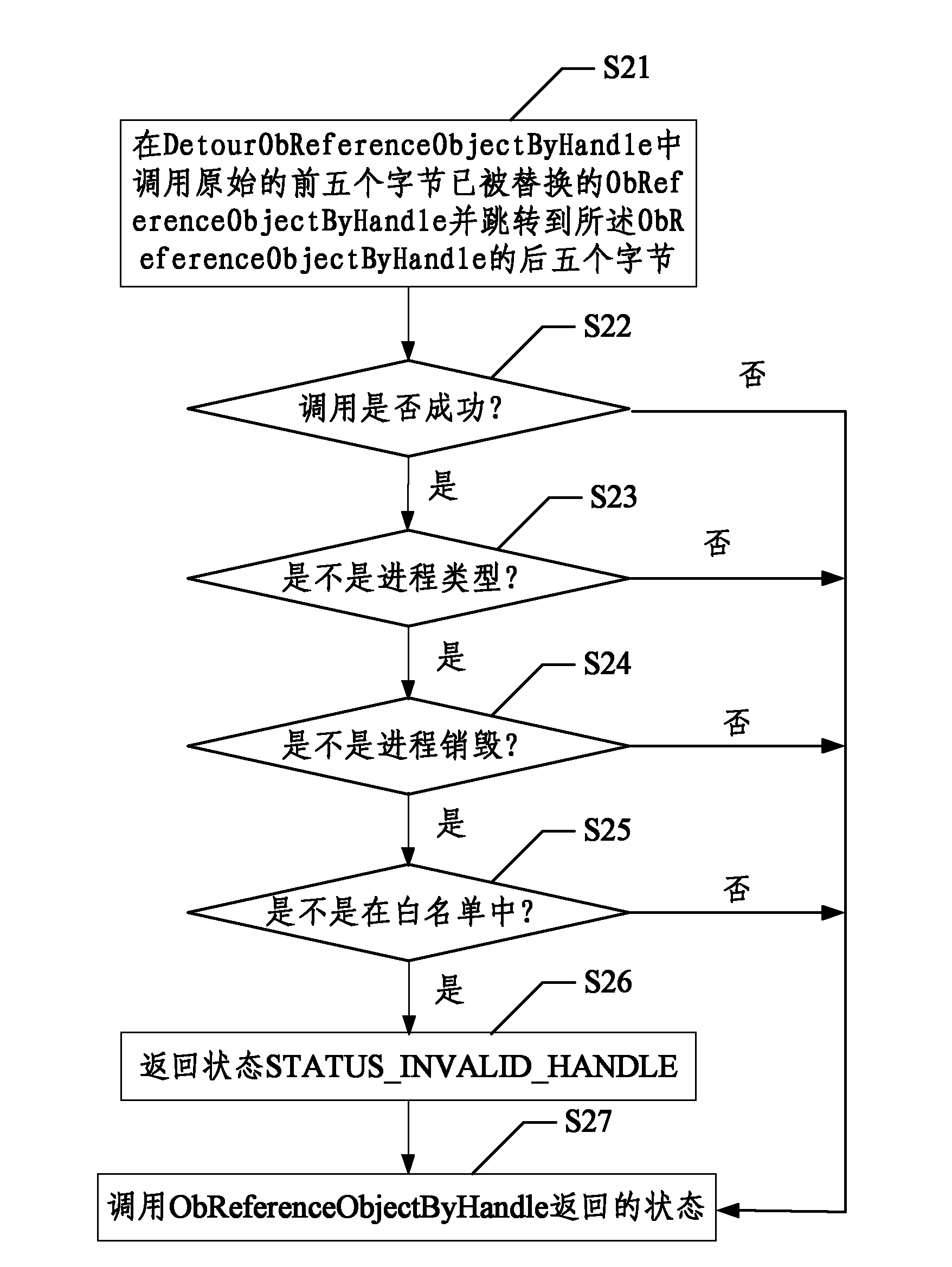
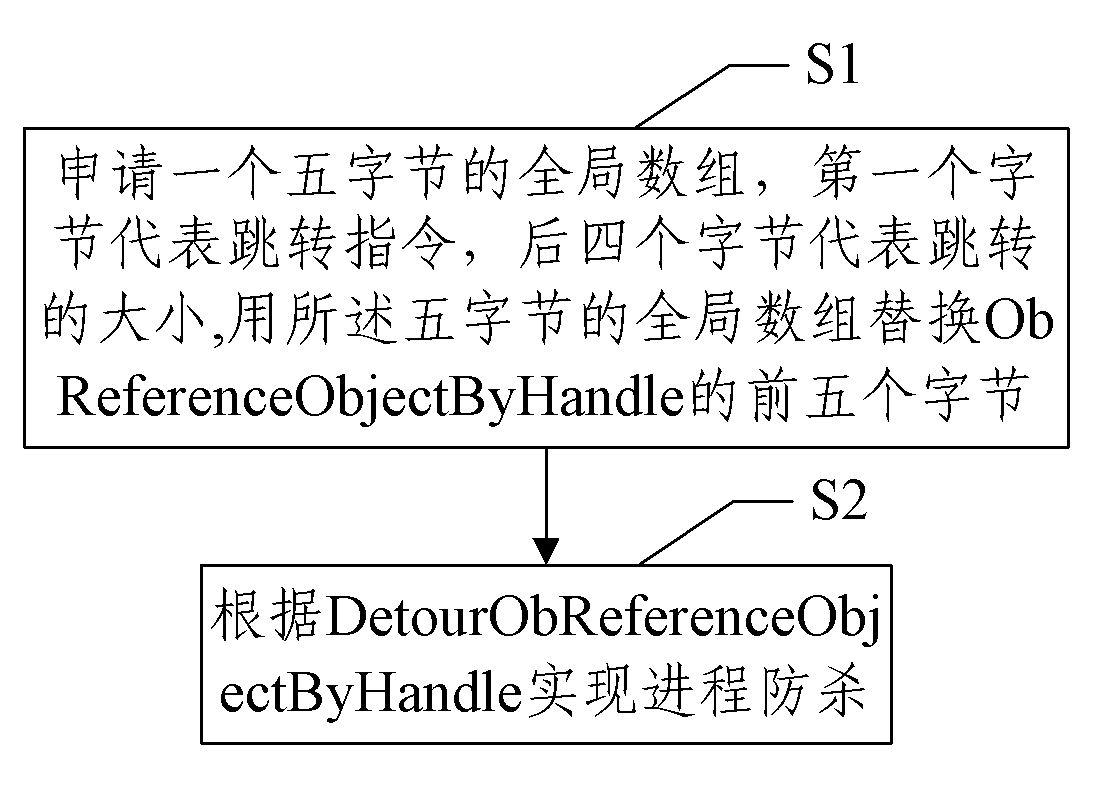
[0030] figure 1 It is a flowchart of a method for realizing process anti-killing described in the embodiment of the present invention; figure 1 Said, the method for realizing process anti-killing comprises steps:
[0031] S1: Apply for a five-byte global array, the first byte represents the jump (JMP) instruction, such as 0XE9, the last four bytes represent the size of the jump, and the size of the jump is DetourObReferenceObjectByHandle-ObReferenceObjectByHandle- 5; Replace the first five bytes of ObReferenceObjectByHandle with the five-byte global array;
[0032] In this step, as long as it runs to ObReferenceObjectByHandle, it will jump to DetourObReferenceObjectByHa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com