Method for deleting repeated data by using double-fingerprint hash check
A technology of data deduplication and hash function, which is applied in the direction of redundant data error detection, electrical digital data processing, and special data processing applications, etc., which can solve the problem of increasing the amount of data block fingerprint calculations, costing calculations, Problems such as data block collisions can be achieved to reduce the amount of fingerprint calculations and save calculation costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
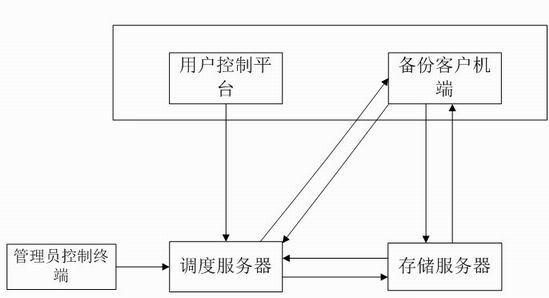
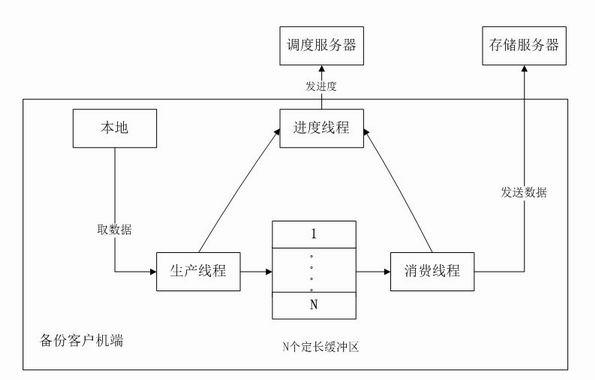
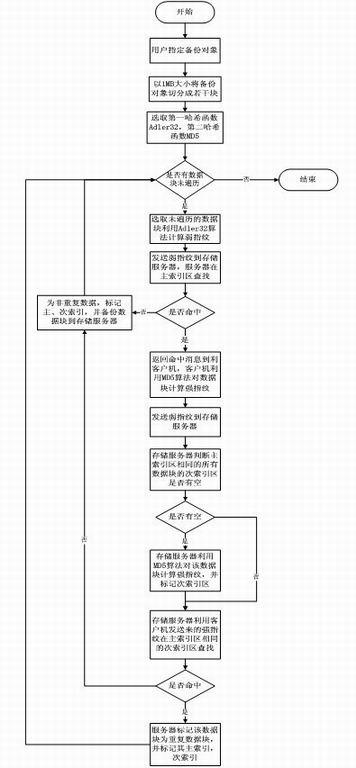
[0024] The present invention is based on the backup mechanism of double fingerprint verification, on the basis of data fixed-length block, utilizes the characteristics of local existence of repeated data, adds double fingerprint hash verification, and deletes repeated data, thereby reducing the calculation amount of data fingerprints . Double-fingerprint hash verification aims to optimize fingerprint calculation, that is, to use weak verification (low calculation amount) and strong verification (high calculation amount), first use the former for screening, and use the latter for calculation after a collision occurs . The so-called weak check means that different data blocks may get the same check value. Strong check is to ensure that different data blocks must not get the same check value. The check value calculated by weak check is called weak check. Fingerprint, the verification value calculated by strong verification is called strong fingerprint. The weak checksum here is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com